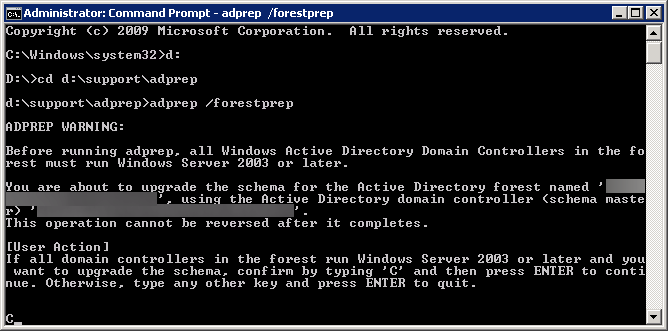
Symptom:
You receive the following error when trying to publish your new Lync Topology, after removing the last Lync 2010 Front End Server.
Result: Call orbit depends on an application server that is being removed.
ServiceInUse: The new topology XML removes services that will create stale configuration settings.
ServiceInUseResolution: Consult your Lync Server documentation to learn how to to disassociate the service of the settings using it.
Error: Cannot publish topology changes. Unassigned number still exists on one or more deleted application servers.
▼ Details
└ Type: InvalidOperationException
└ ▼ Stack Trace
└ at Microsoft.Rtc.Management.Deployment.Tasks.PublishTopologyTask.CheckIfVacantNumberRangesInUse(DeletedServices deletedServices) at Microsoft.Rtc.Management.Deployment.Tasks.PublishTopologyTask.VerifyServiceDependentSettings(DeletedServices deleteServices) at Microsoft.Rtc.Management.Internal.Utilities.LogWriter.InvokeAndLog[T](Action`1 action, T arg)
Error: An error occurred: "System.InvalidOperationException" "Cannot publish topology changes. Unassigned number still exists on one or more deleted application servers."
Solution:
Open up the Lync Server Management Shell as an Administrator on a different Front End server that you aren't retiring and execute the following command:
Get-CsUnassignedNumber
For each of the returned results with the AnnouncementServerFqdn matching the server you are trying to retire, execute the following command:
Set-CsUnassignedNumber -Identity IdentityFromPreviousCommand -AnnouncementService newlyncpoolorfrontend.mydomain.local
Alternately, you can change the Front End server these numbers are on through the Lync Web GUI (Cscp). To do so, navigate to the Lync Server 2013 Control Panel, click on Voice Features->Unassigned Number, and then double click every entry that has a destination with the old Front End. When the Edit Unassigned Number Range dialog shows up, type in the FQDN to the new Front End Pool/Server and then click OK. Repeat for each number.
Lastly, if you want to cleanup your Lync server, you can remove all instances of the old Announcements using the following command:
Remove-CsAnnouncement -Identity "ApplicationServer:myoldfrontend.mydomain.local"
Alternately, if you published the topology, you may have to remove the Announcements individually by using entering the command below with the entire Identity value or via the old ApplicationServer's name (in my case it was 1-ApplicationServer-1 as shown below):
Remove-CsAnnouncement -Identity "ApplicationServer:probablysays1-ApplicationServer-1/1951f734-c80f-4fb2-965d-51807c792b90"
Once all Unassigned Numbers have been moved to the new Front End server or pool, you should be able to successfully publish your topology.