Problem:
Many applications want to federate with leverage certain attributes like nameid (nameidentifier), but the problem is the format is wildly different from one application to another. In this case, one application might use a unique value like an employee ID, another UPN, another email address, and so on. Or maybe it isn't an attribute, but you are leveraging SHA1 as your signature hashing algorithm and the application is looking for MD5.
In this case, sometimes you may not be sure what you are sending to the application and are looking to the vendor to help you understand what you need to change in ADFS or if you are working on a custom application, need help debugging your claims rules to integrate into that application. In this case, I will show you how to leverage Fiddler to acquire the SAML Tokens issued by ADFS to validate what attributes/values you are passing to the federate application.
Tutorial:
- Grab the latest copy of Fiddler from their website (it is a free download)
- Install Fiddler on your local machine
- Launch Fiddler
- Click Cancel if prompted about AppContainers
- With Fiddler open click on Tools -> Telerik Fiddler Options...

- Click on the HTTPS tab and check Decrypt HTTPS traffic and click OK
- Close out of Fiddler
- Open Fiddler

- Open up Internet Explorer in one window and Fiddler side-by-side. Drag the Crosshair icon onto Internet Explorer. This will target only traffic in this process (browser window) to help filter down intercepted traffic.
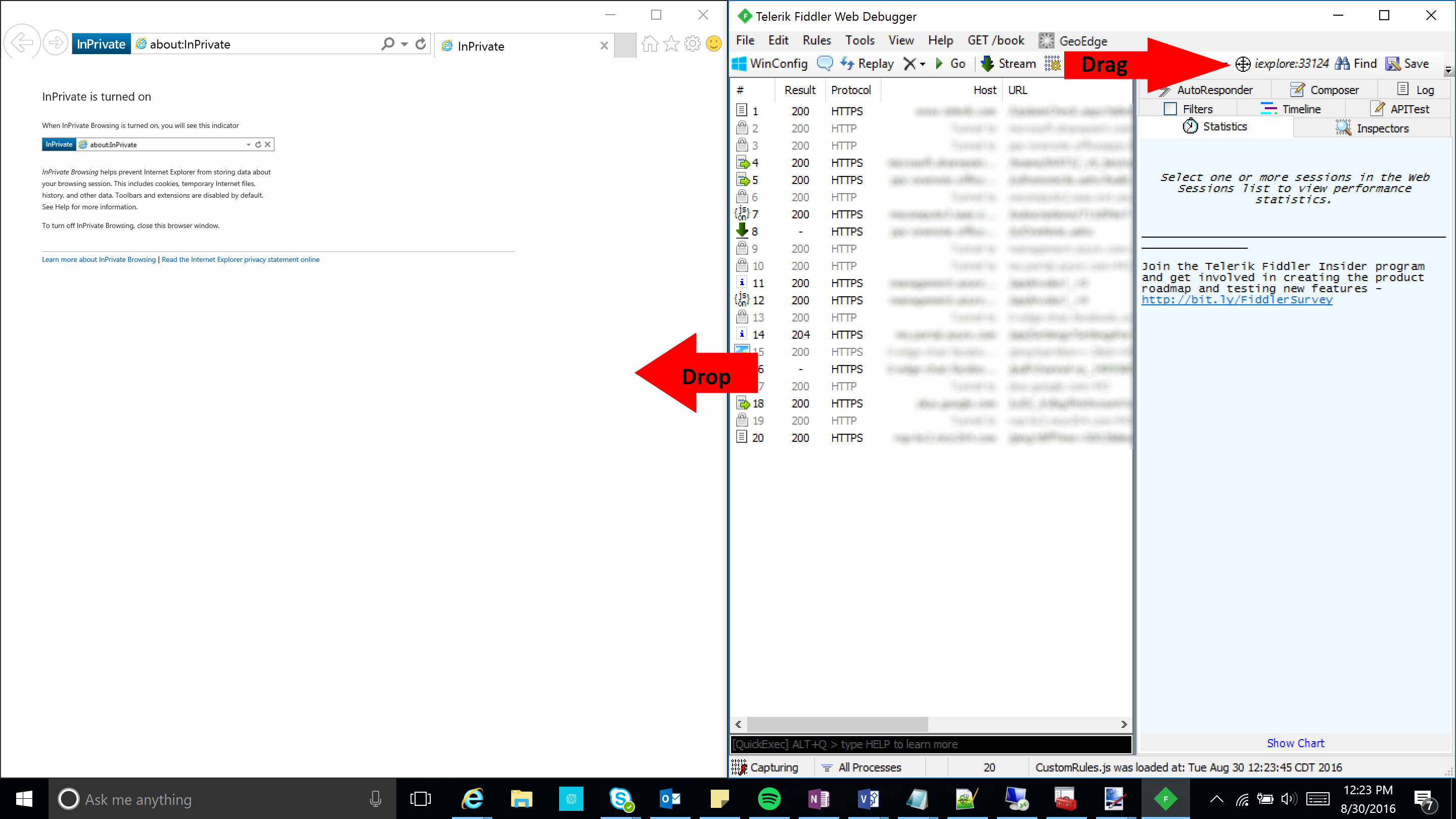
- Select the X icon with a dropdown and click Remove all to clear your trace
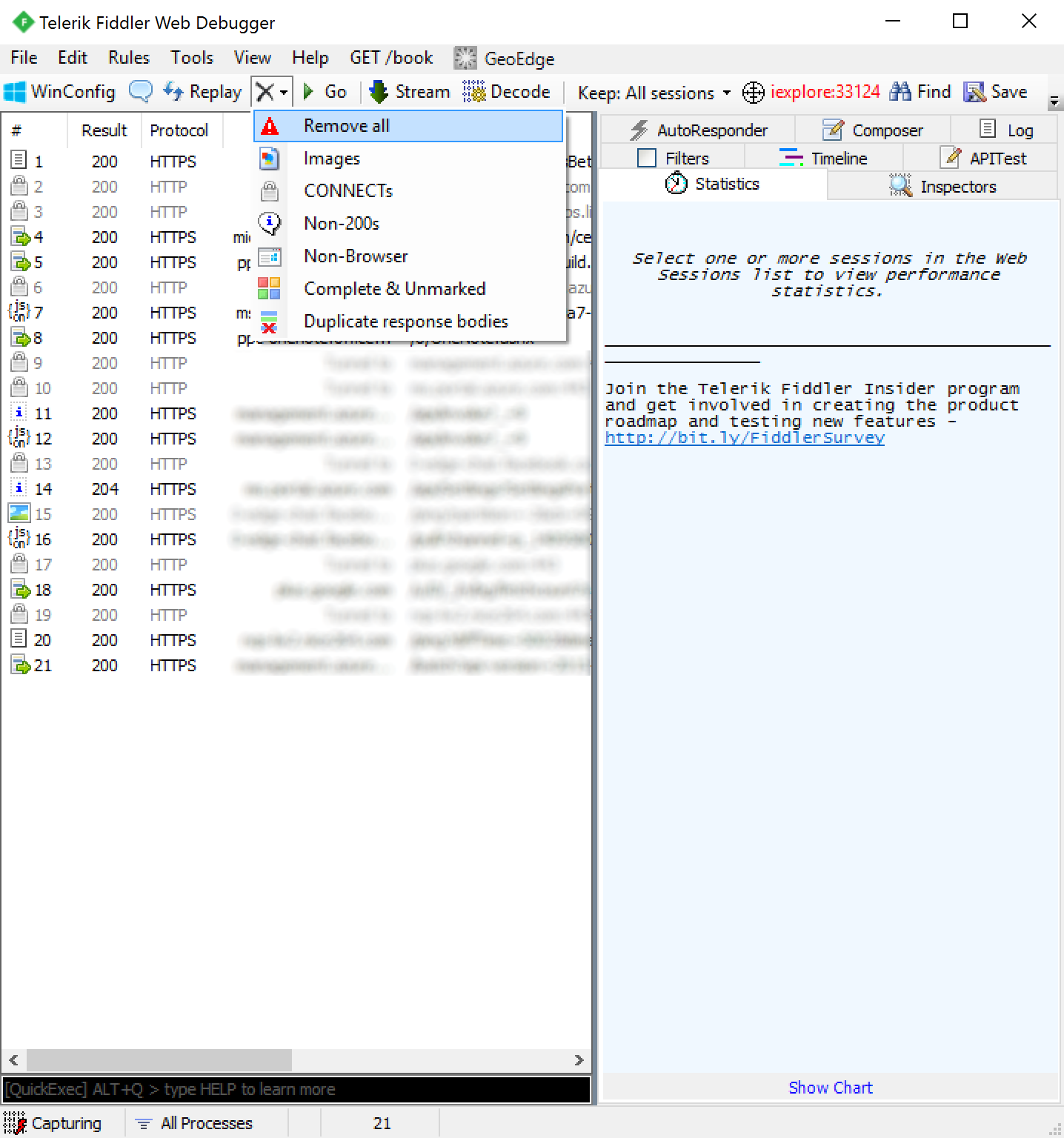
- Go to the url of the federated application and login. In this case, I am going to use https://outlook.com/owa/jackstromberg.com; once you have logged into the application or received the error to your application upon login, click File - Capture Traffic to stop the logs

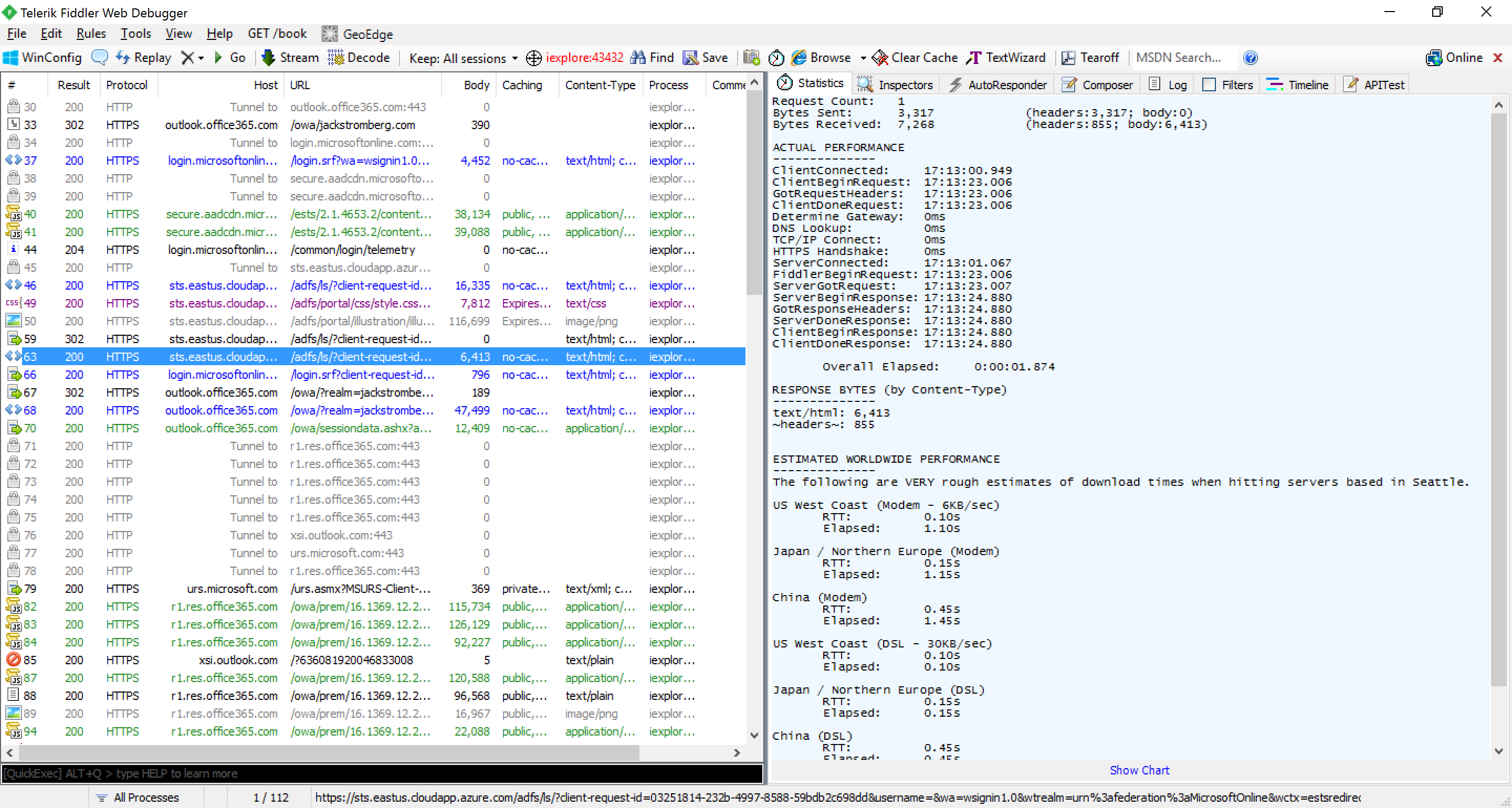
- Within your logs, look for the last 200 response from your ADFS server before being redirected to your application (which will not show up as a 302, since we are posting to the new URL)
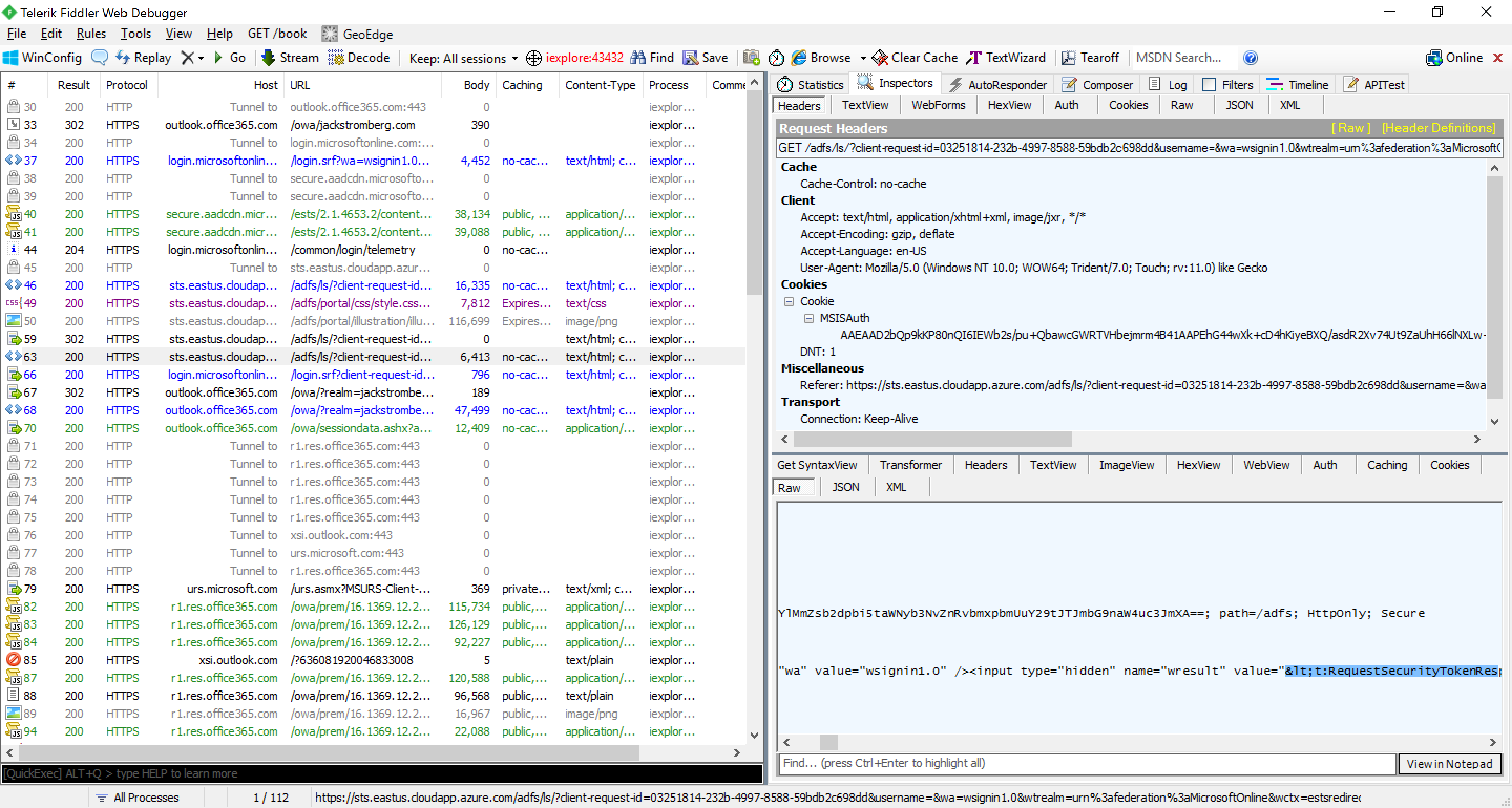
- Click on the Inspectors tab, and select the Raw tab at the bottom and copy the value from the hidden input tag with the name of wresult
- Paste the encoded HTML into my HTML Encoder/Decoder in the Encoded text box and click Decode.
- Copy the Decoded HTML and paste it into an XML formatter of your choice. Here I am using Bing:

- Copy the result into Notepad and you can now read the information
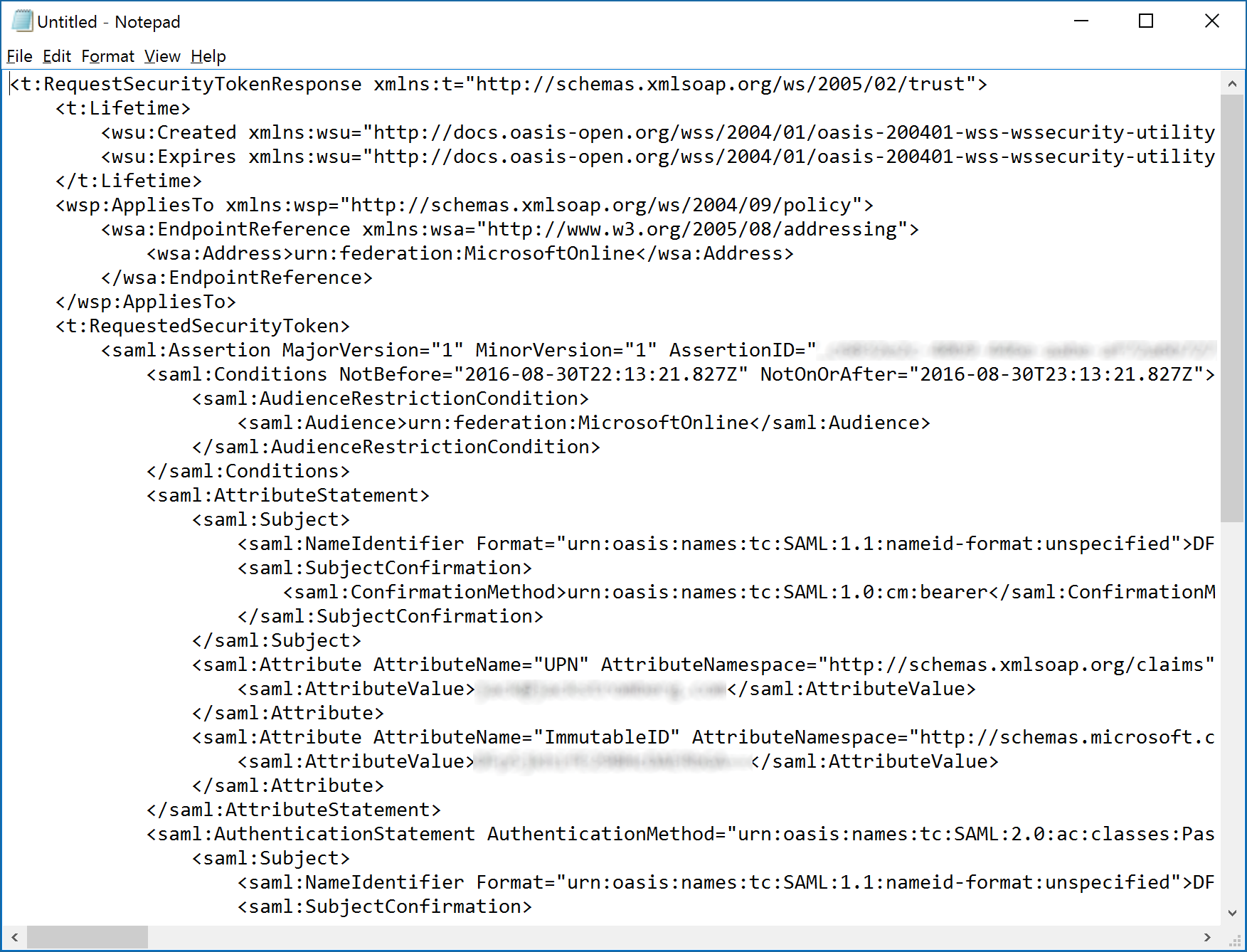
Going into the claim and how it works is outside the scope of this tutorial, but as you can see in the last screenshot above we have the raw SAML token we will send to the relying party trust to consume. At this point, the vendor can be involved to help troubleshoot any values or attributes that are in an incorrect format.