Use Case:
This guide will go over configuring Fiddler to intercept traffic from mobile devices for debugging purposes. This scenario can be beneficial in tracing/debugging SAML tokens issued from your IdP for a mobile application to consume. We will be able to validate all traffic flowing in/from the Android device.
Configuring/Setting up Fiddler:
- Grab the latest copy of Fiddler from their website for Windows (it is a free download)
- Install Fiddler on your local machine
- Launch Fiddler
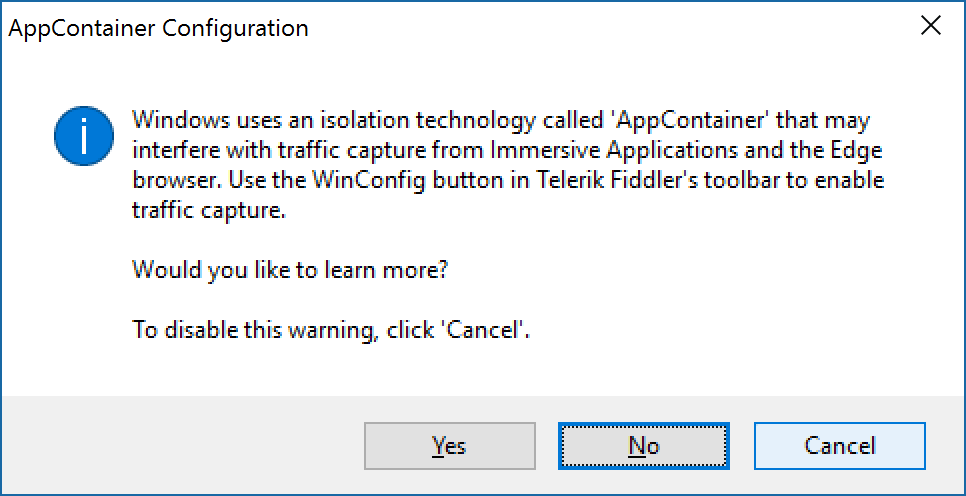
- Click Cancel if prompted about AppContainers
- With Fiddler open click on Tools -> Telerik Fiddler Options...

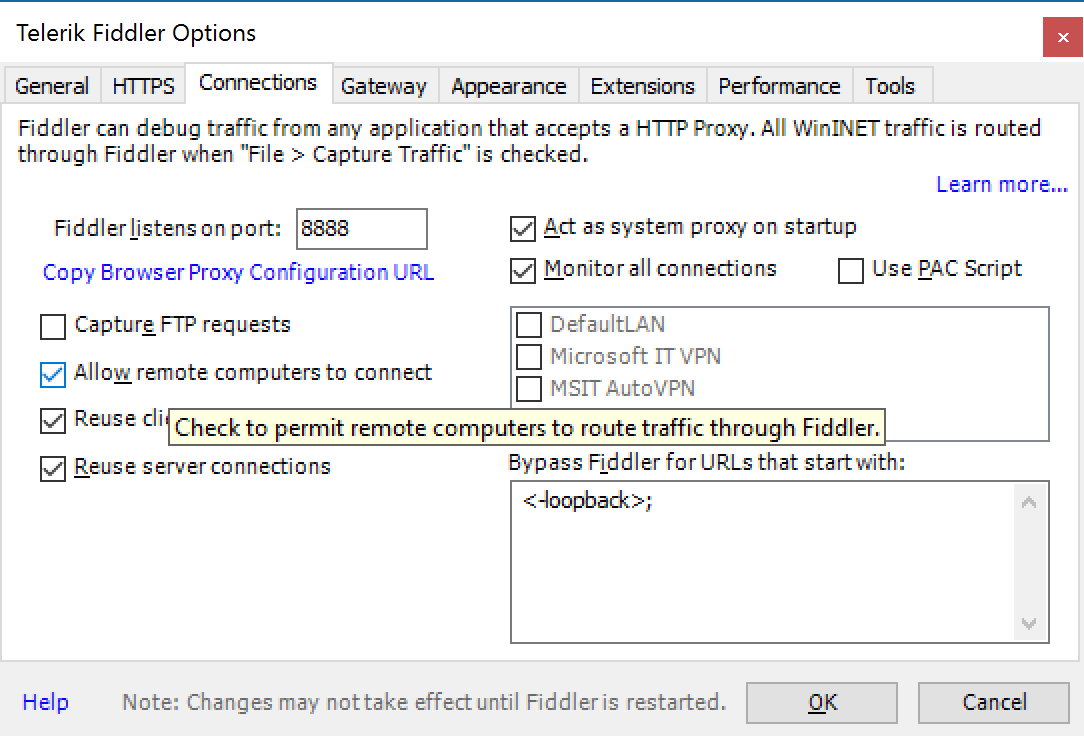
- Click on the Connections tab and check Allow remote computers to connect
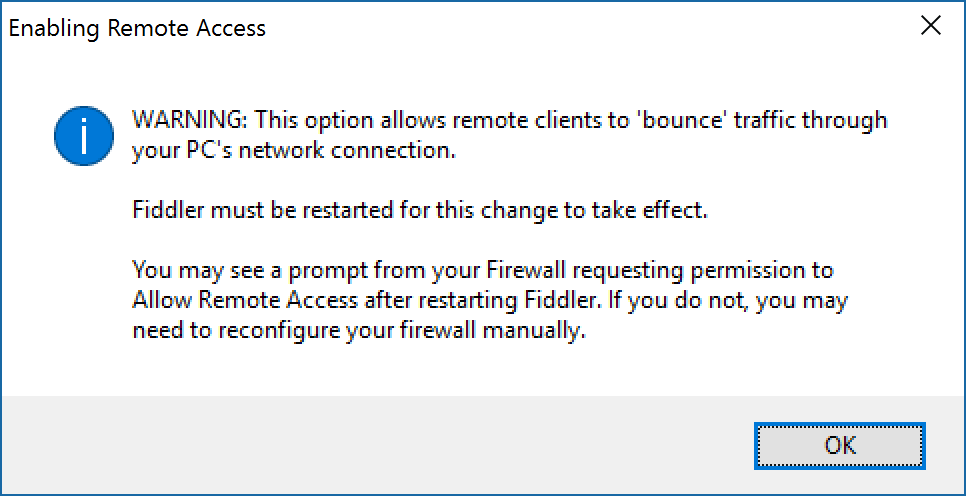
- You will receive a dialog box saying it will need to restart. Click OK and close out of Fiddler
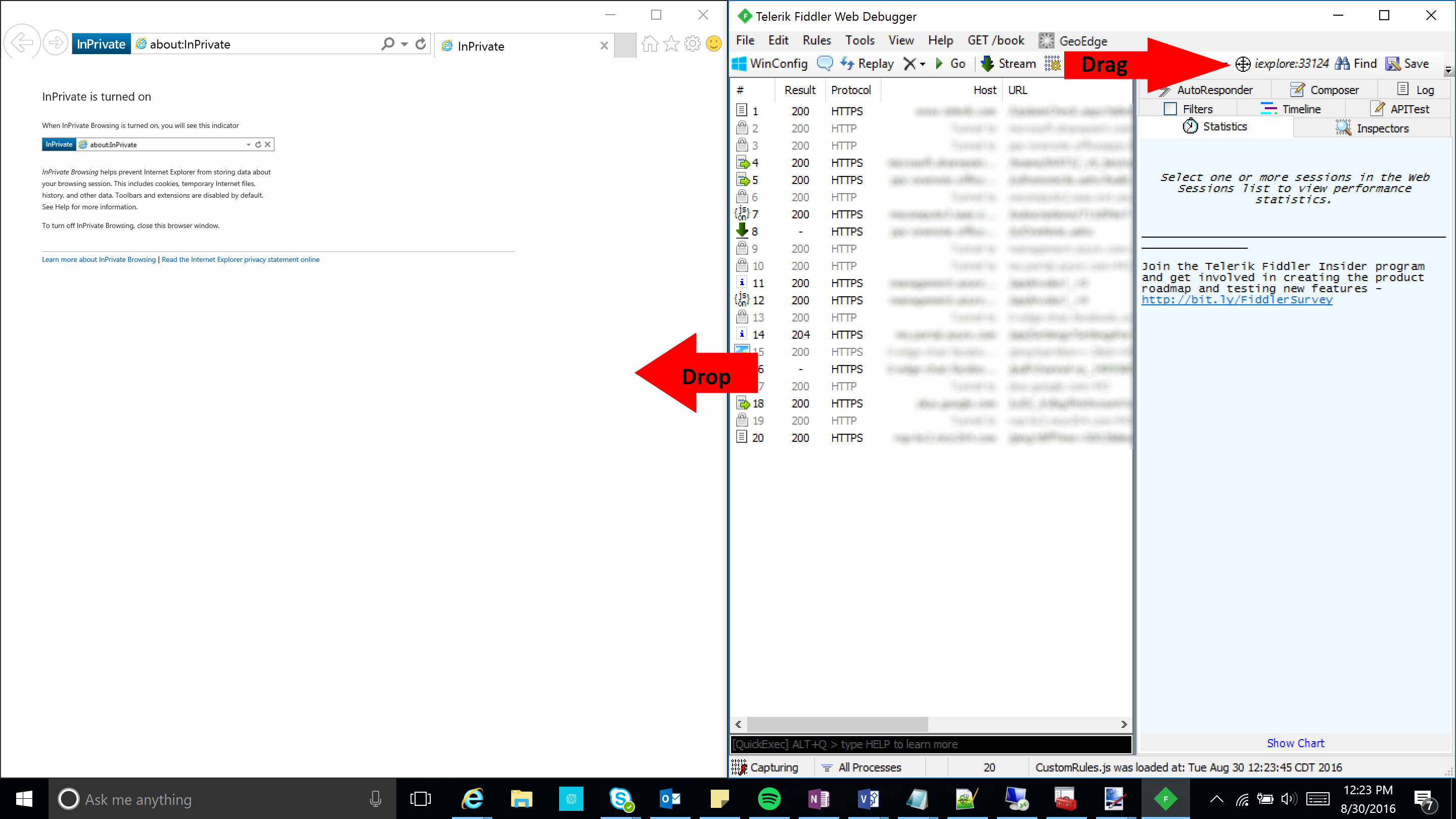
- Once you relaunch Fiddler, click on the down arrow (if shown) and hover over the Online icon

At this point, Fiddler is configured properly, let's shift over to your mobile device. We'll shift gears to configuring the Android device to push traffic to Fiddler.
Configuring an Android device
(Android v6.0.1 at the time of writing)
- Slide down the notifications drawer from the top of the screen and hit the Settings (gear) icon in the top right
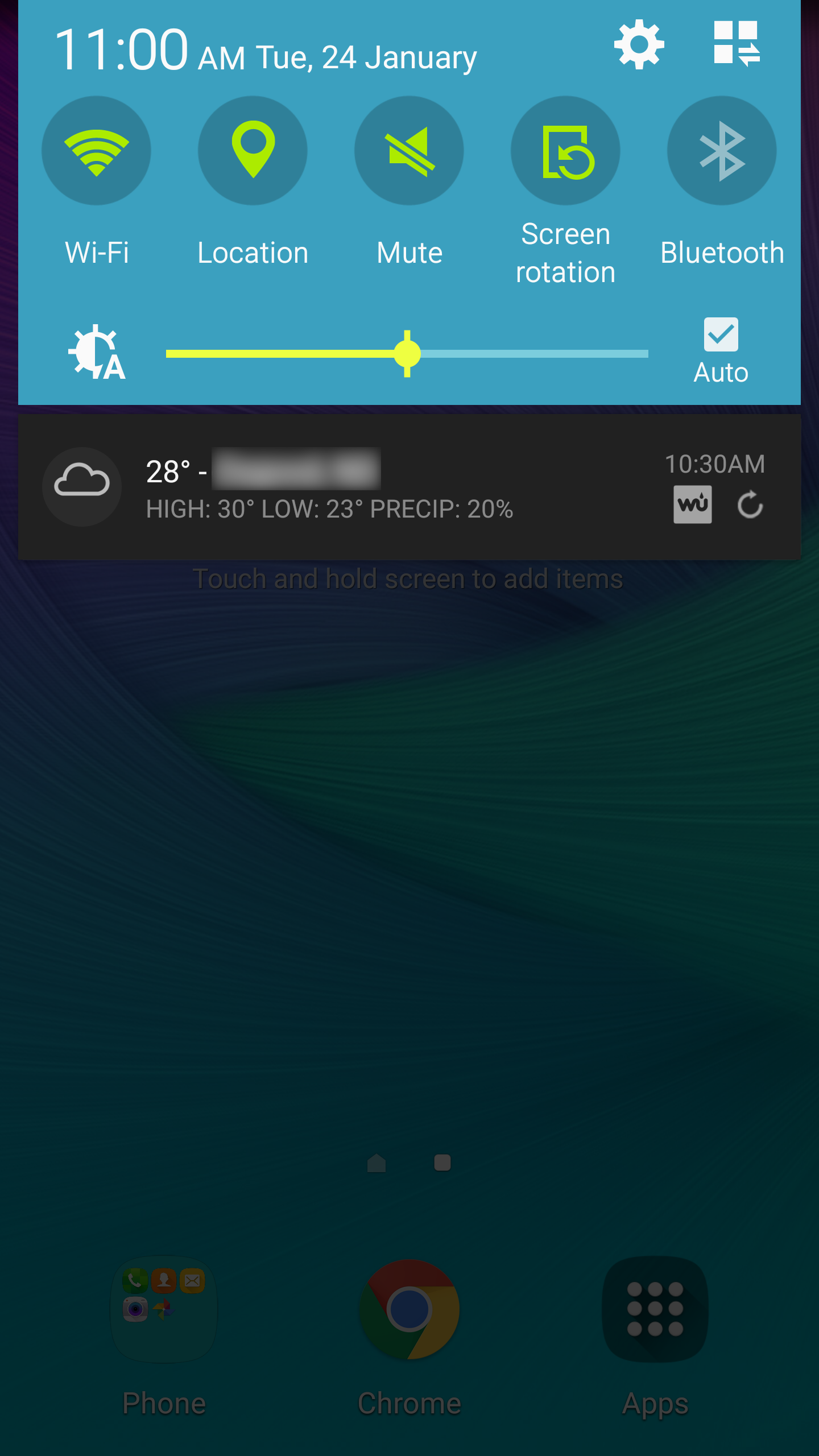
- Select Wi-Fi under the Wireless and networks section
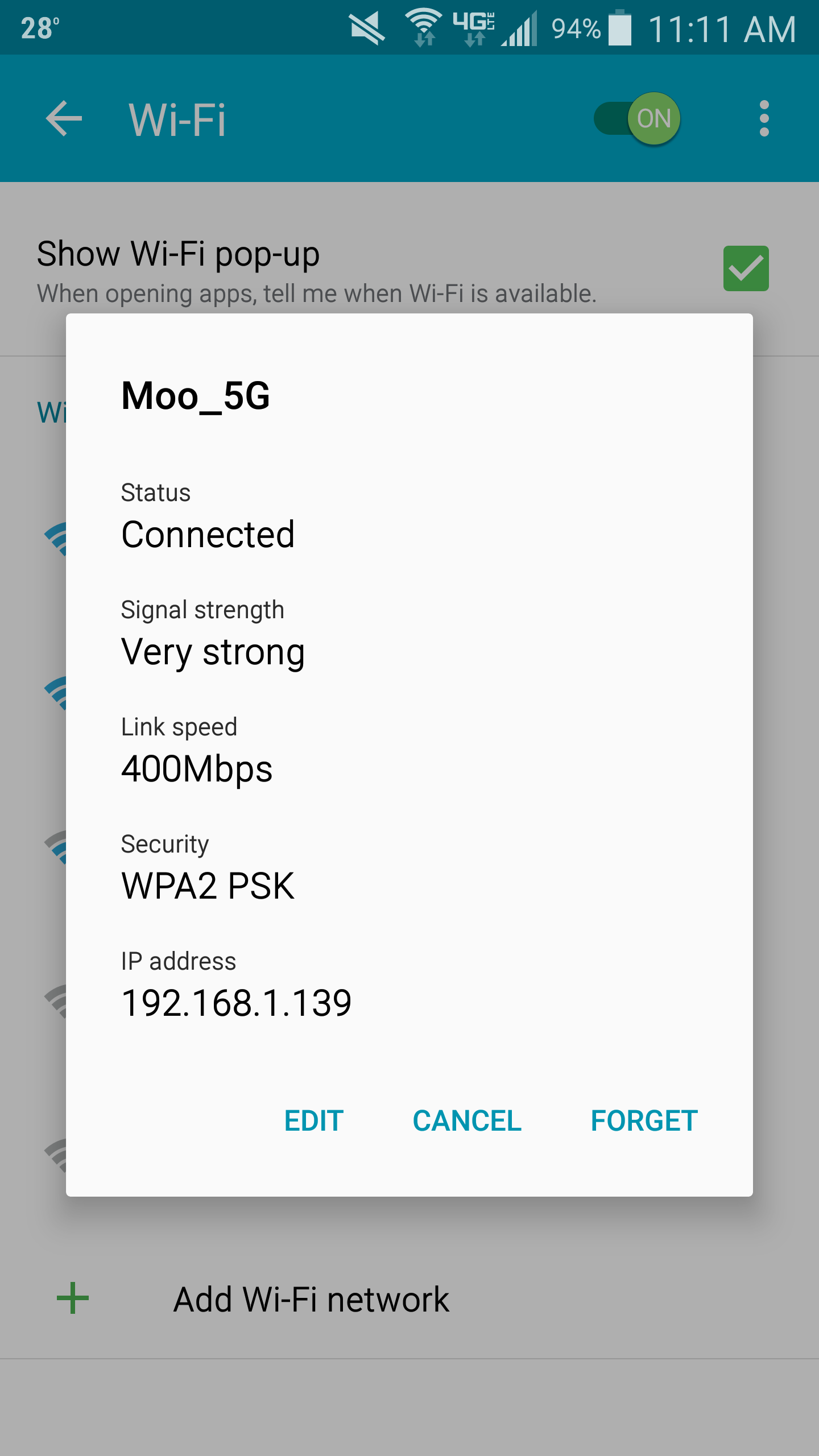
- Select the wireless network you are connected to and click Edit
- Scroll down and check Show advanced options
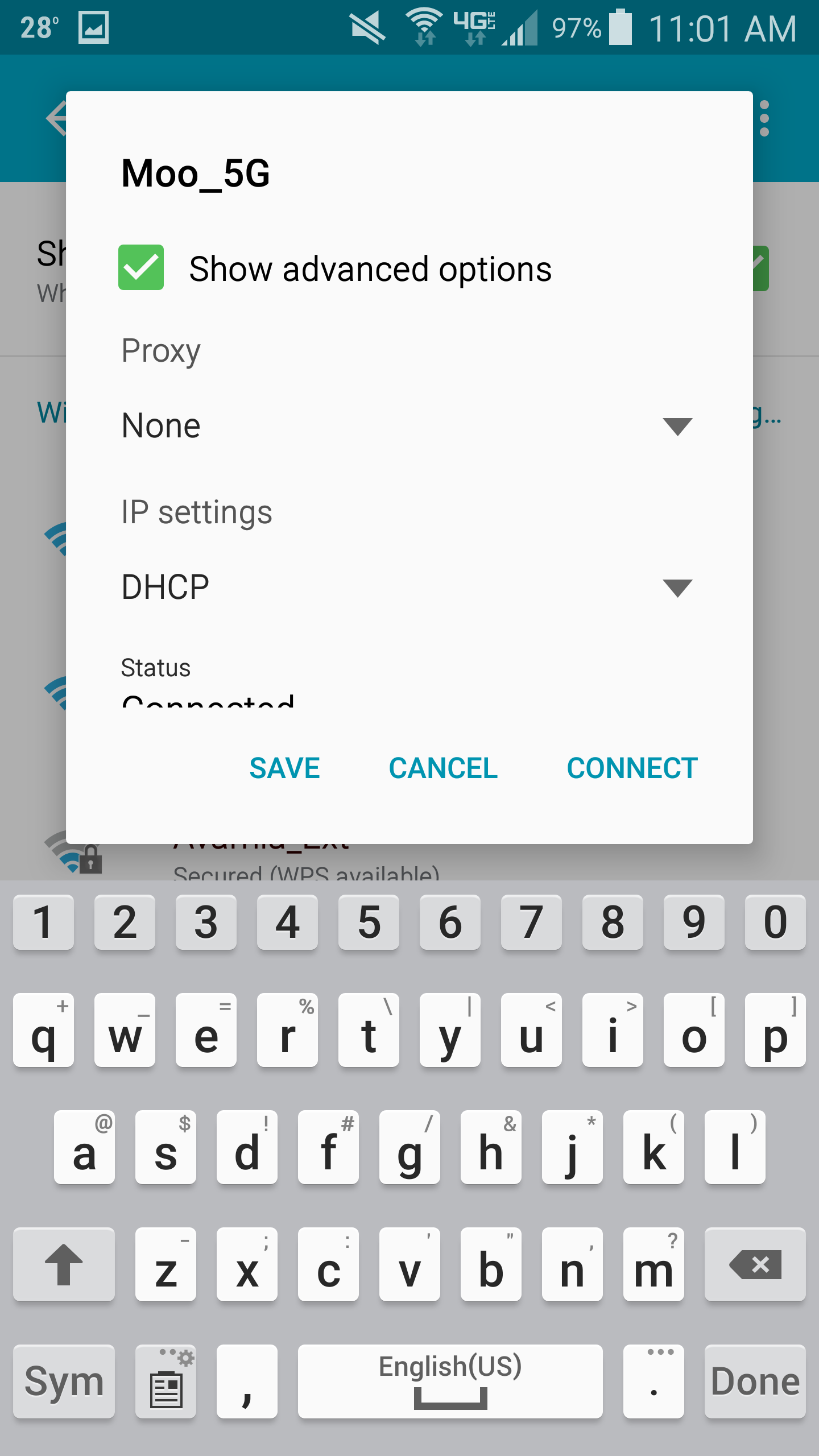
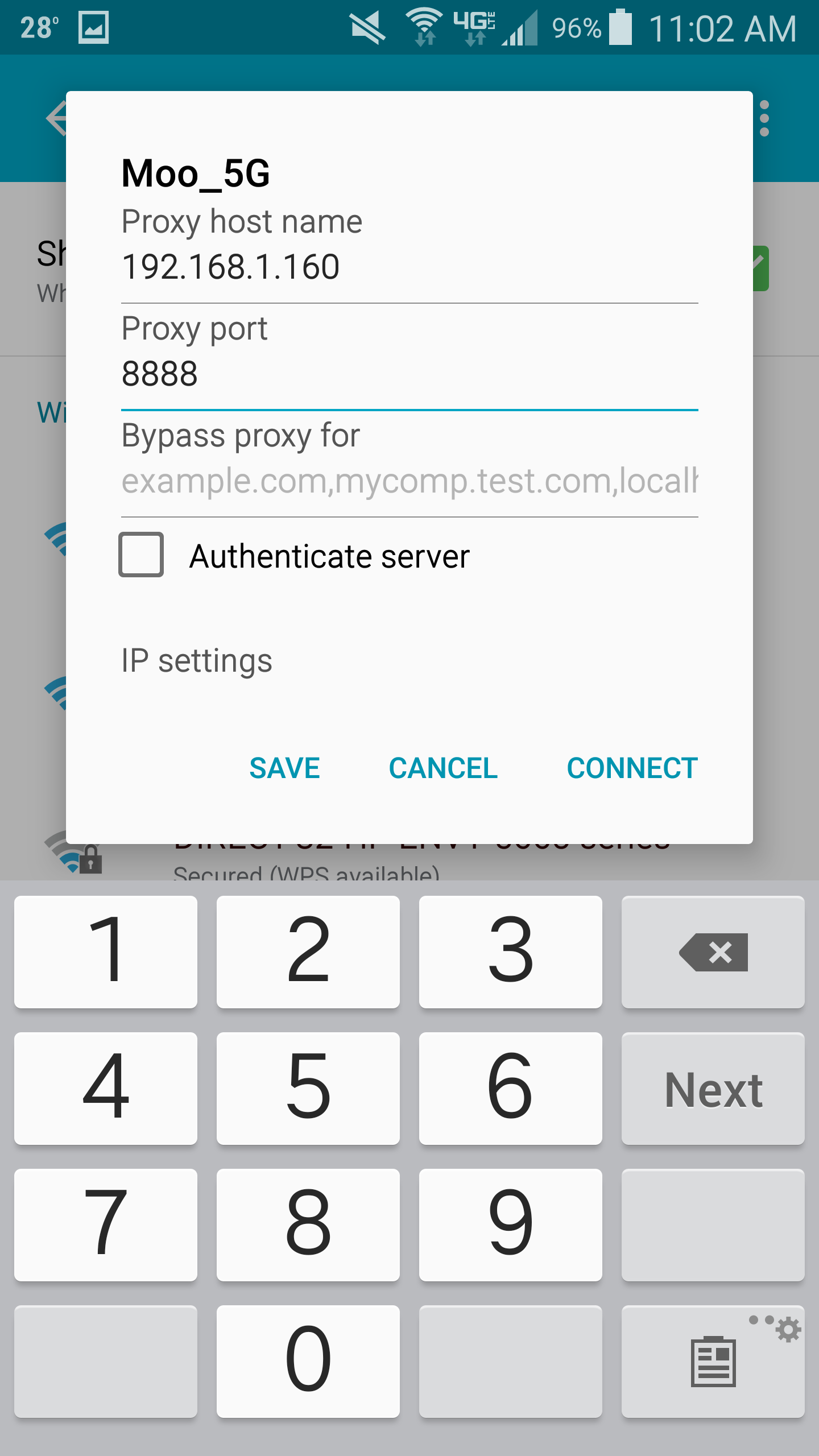
- Select the drop-down for Proxy and choose Manual
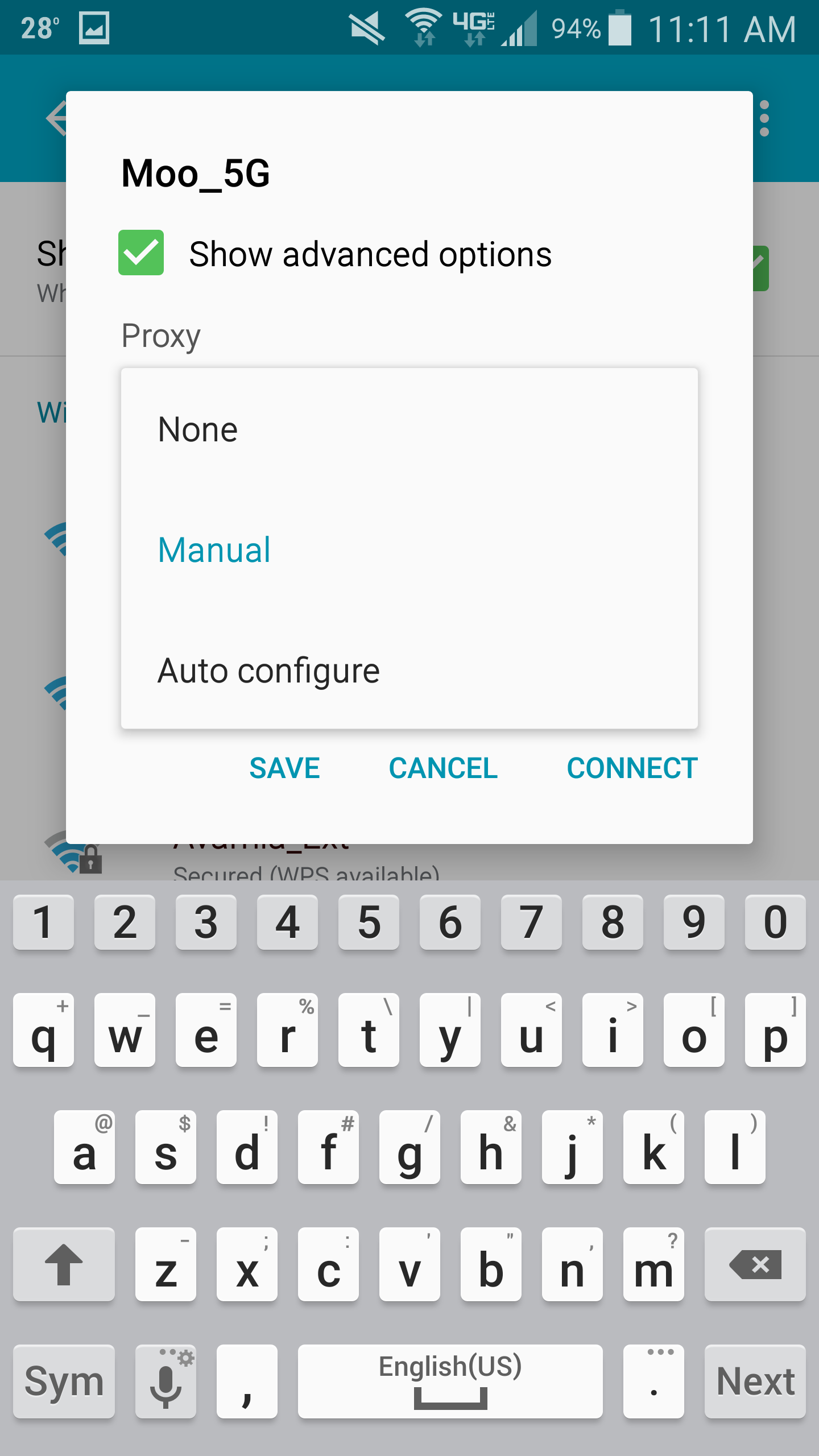
- Type in the IP address gathered from Fiddler for the Proxy host name and set the Proxy Port to 8888 and click Save
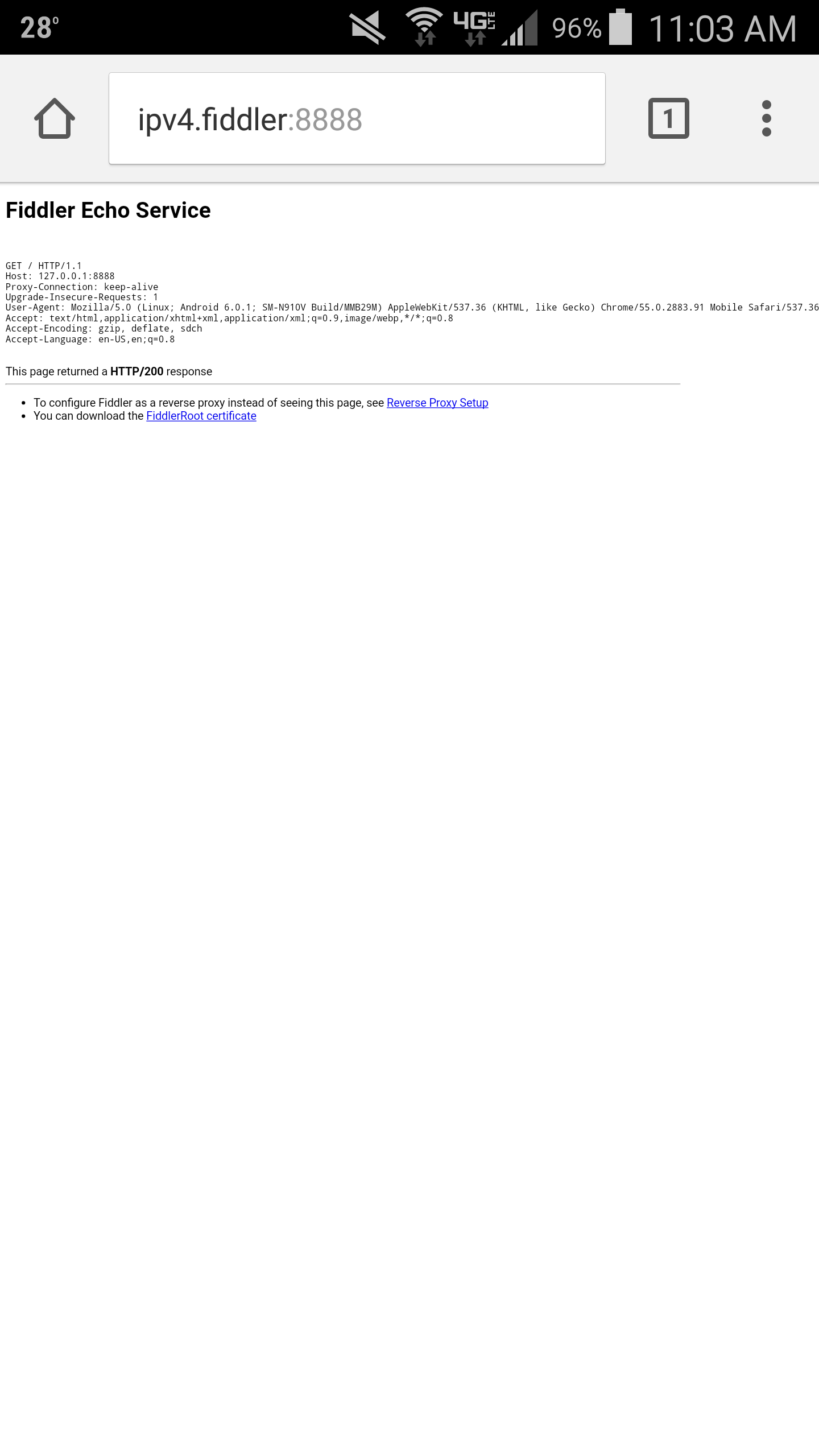
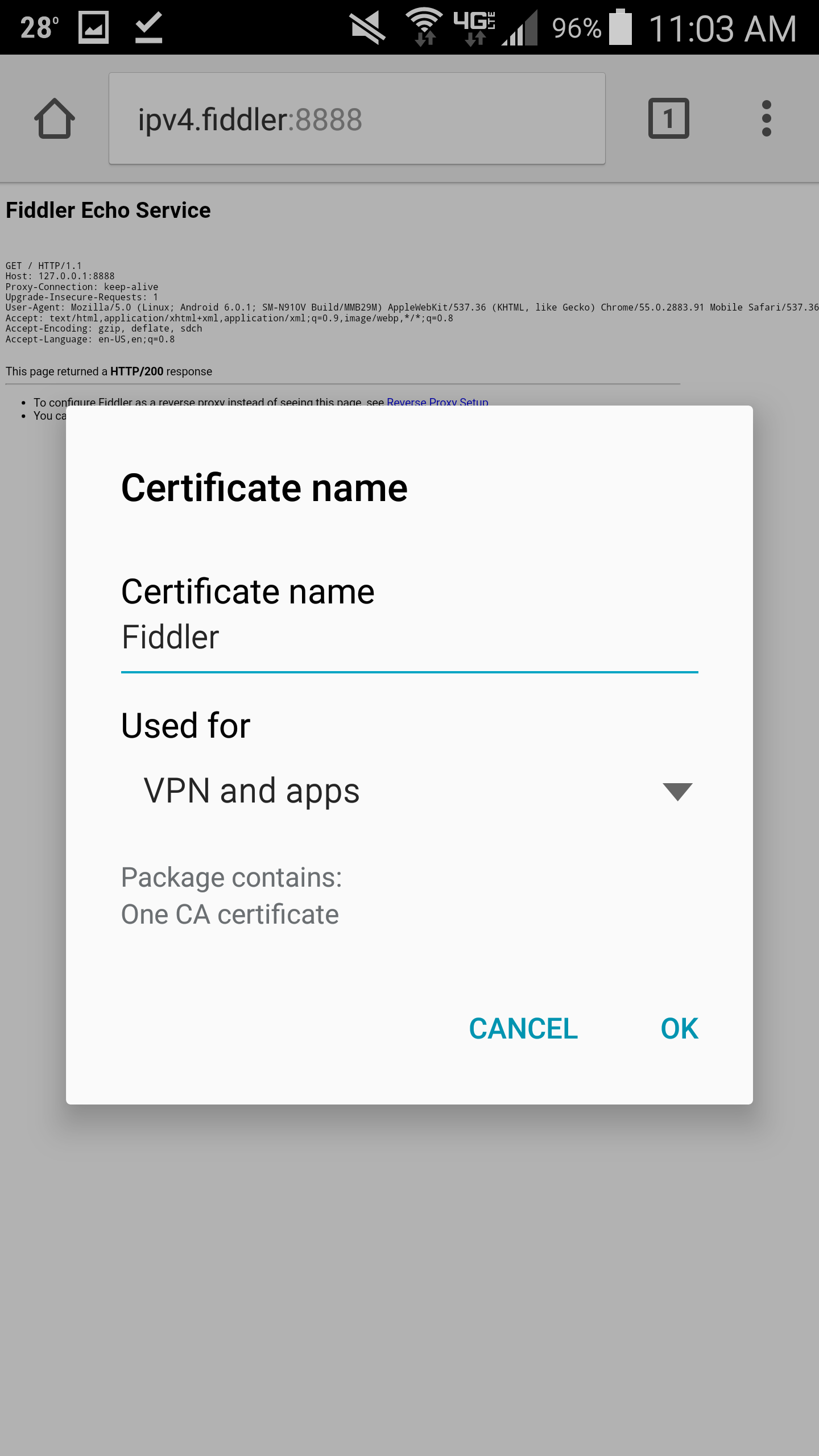
- Next, open up your web browser and navigate to http://ipv4.fiddler:8888
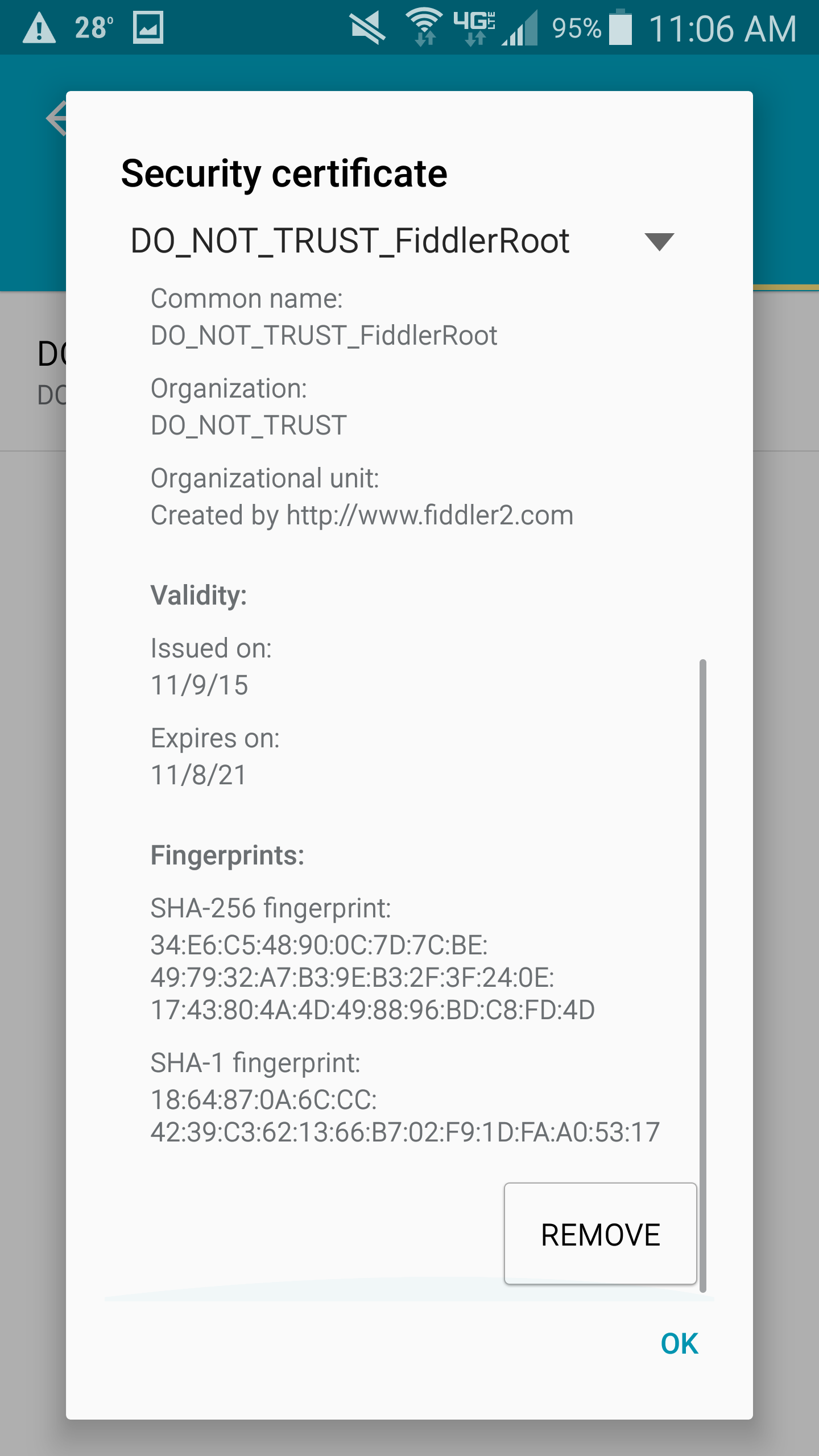
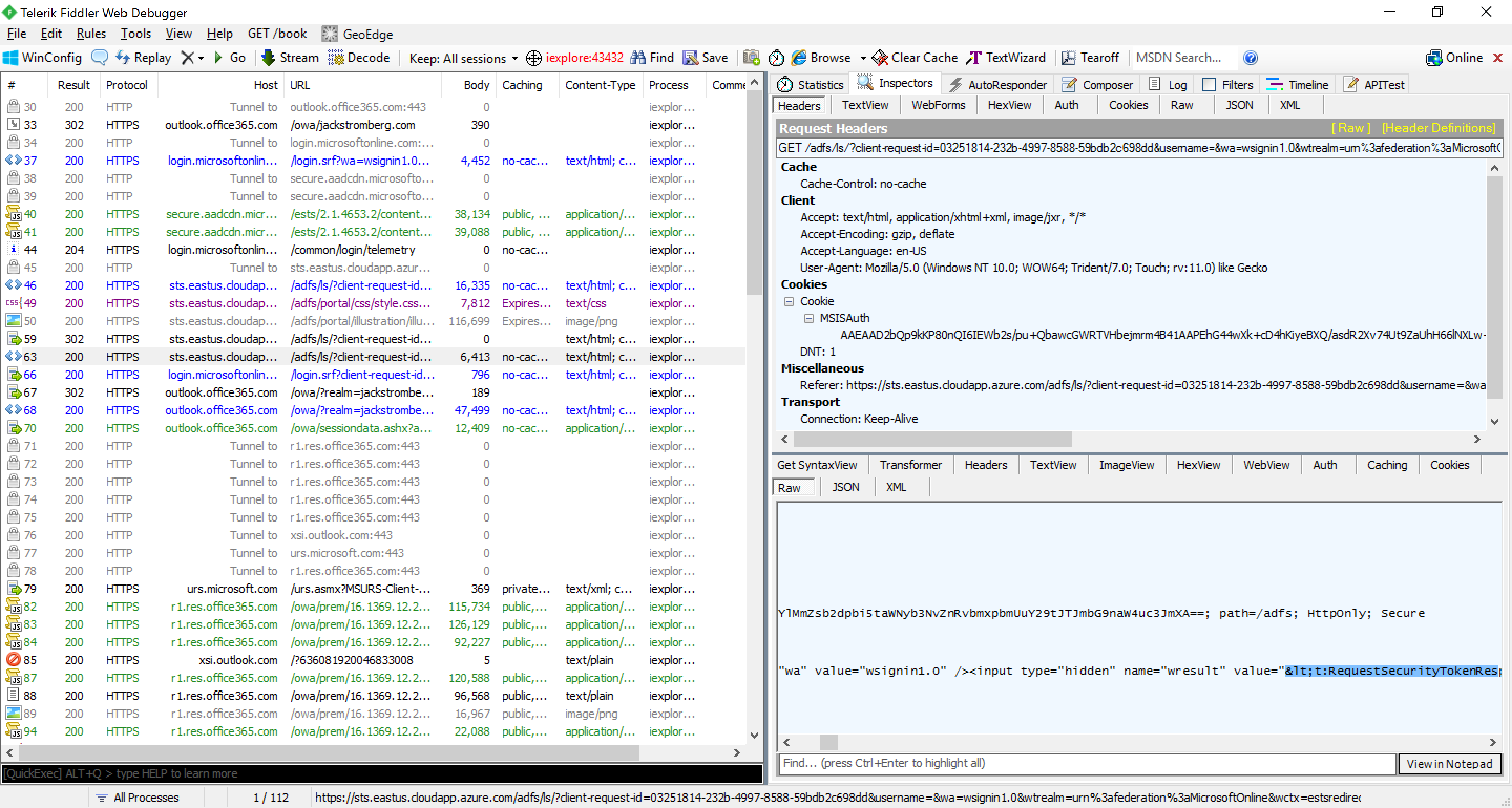
- On the Fiddler Echo Service page, click on the You can download the FiddlerRoot Certificate link
- Note: This download Fiddler's root certificate to allow us to intercept SSL traffic for debugging purposes
- Once the certificate has downloaded, type Fiddler as the Certificate name and click OK
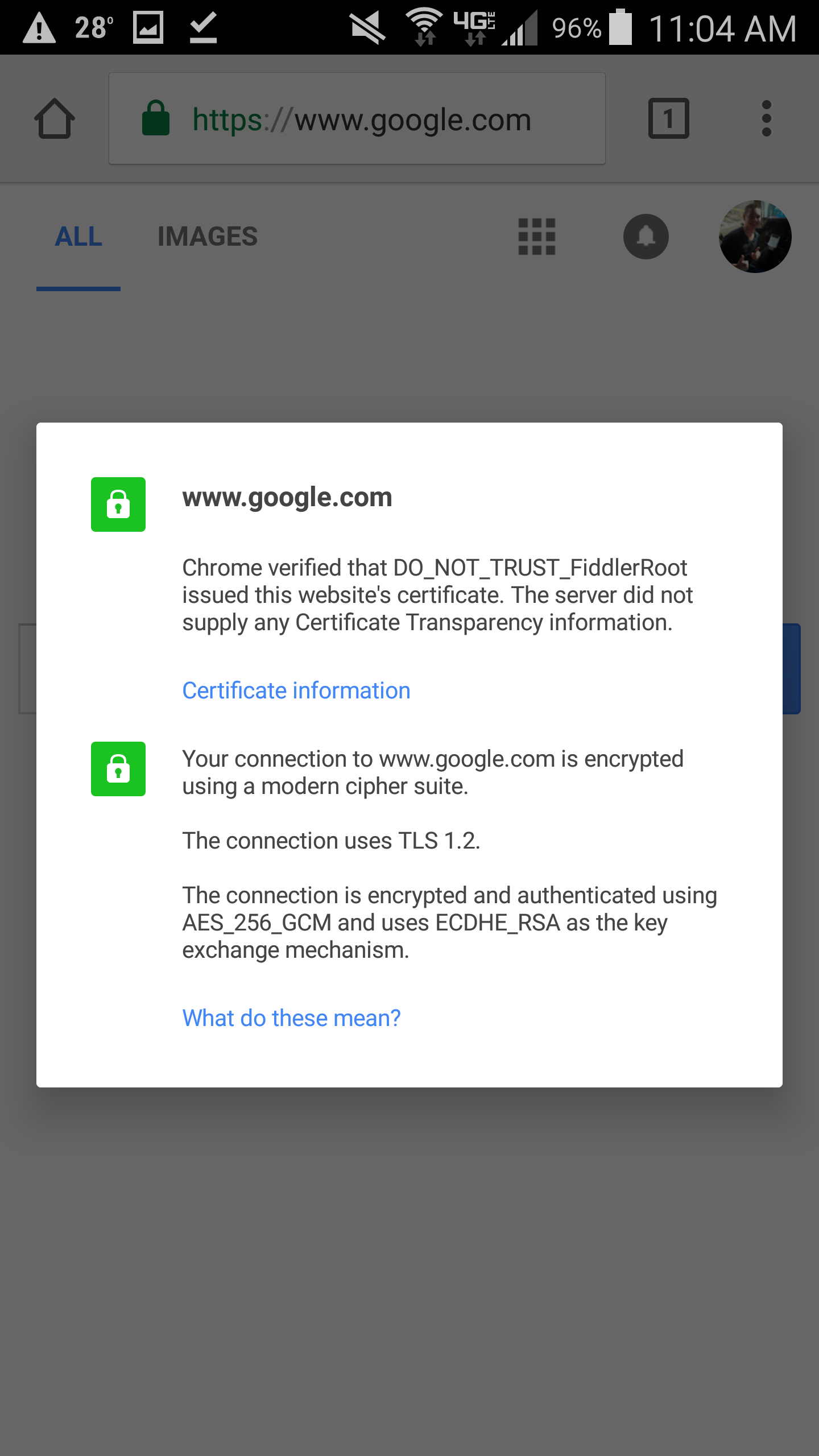
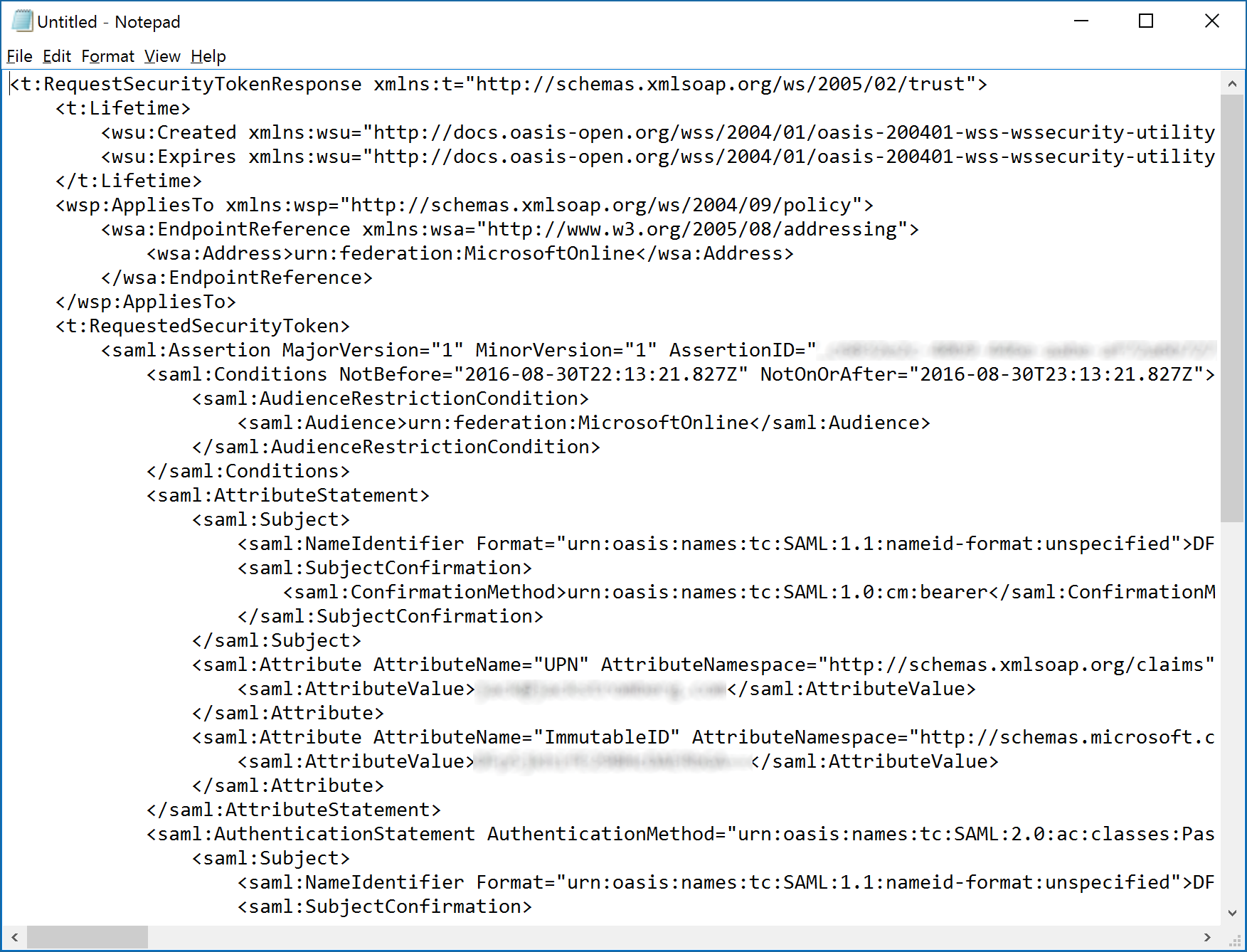
- Optional step: Open up your web browser and navigate to a website using SSL (I did https://google.com)
Turn off Fiddler from intercepting SSL traffic
Remove the proxy settings
- Slide down the notifications drawer from the top of the screen and hit the Settings (gear) icon in the top right

- Select Wi-Fi under the Wireless and networks section

- Select the wireless network you are connected to and click Edit

- Scroll down and check Show advanced options (you should see your old proxy settings unlike my screenshot below)

- Select the drop-down for Proxy and choose None
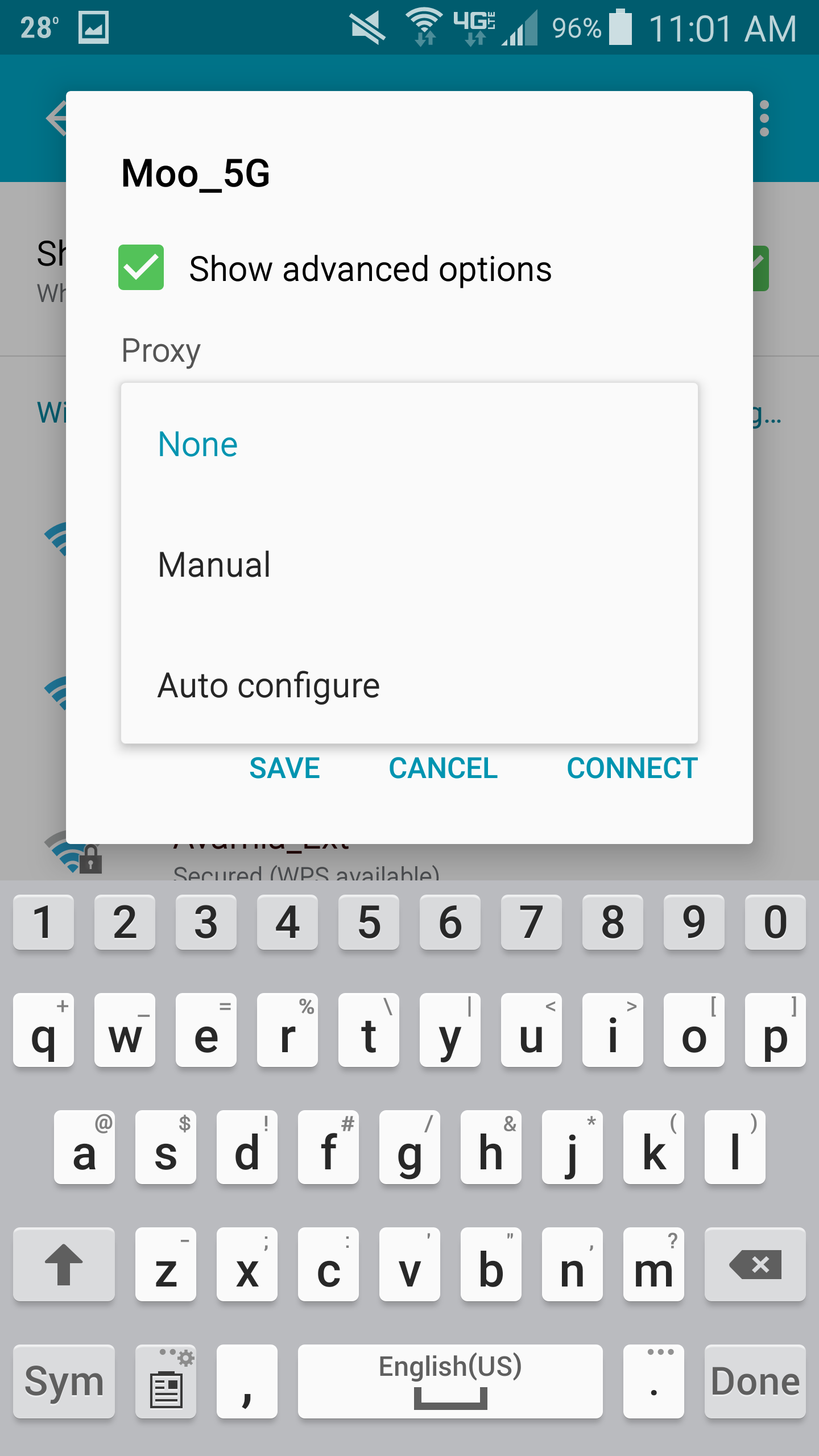
- Select Save

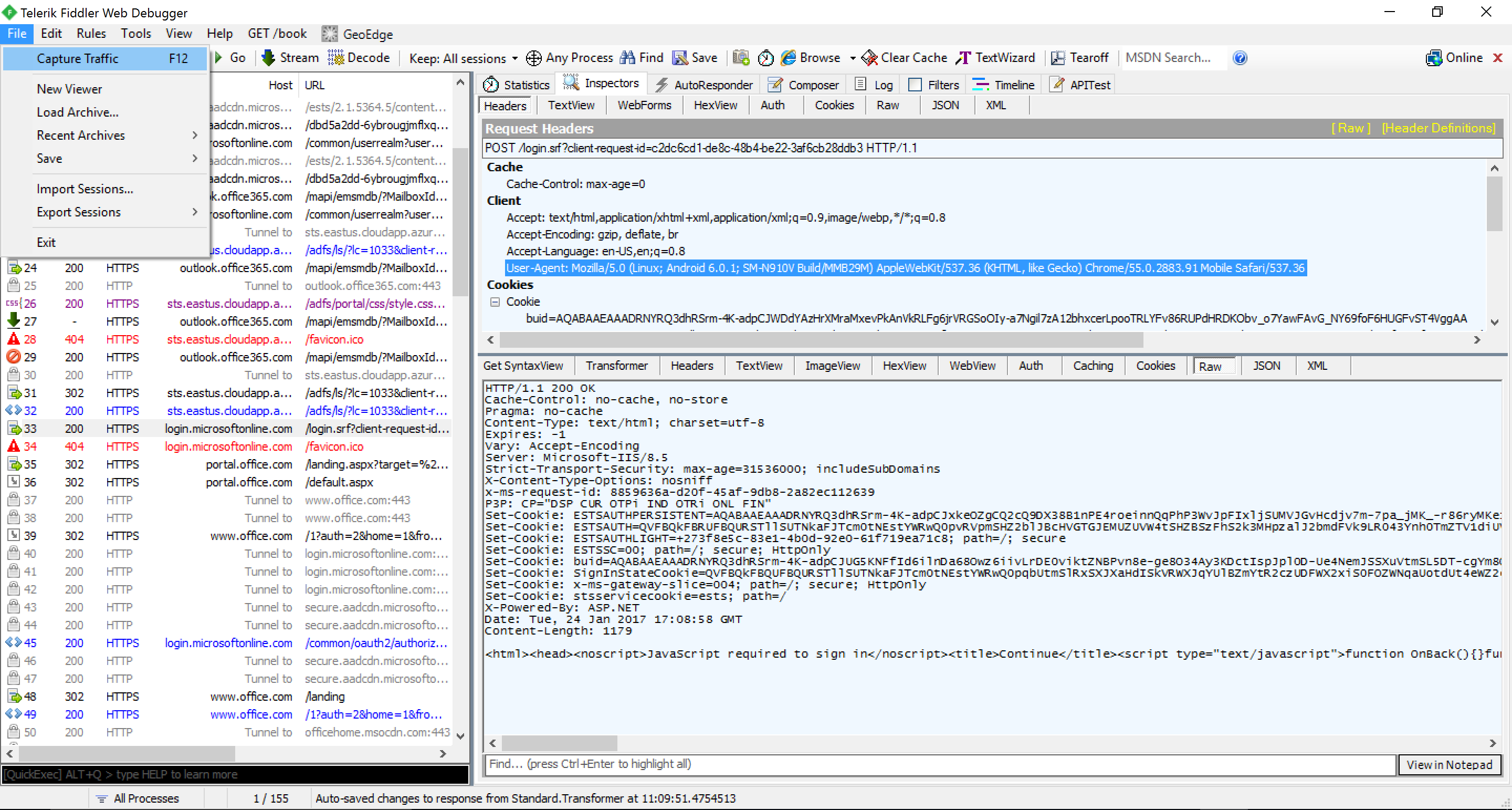
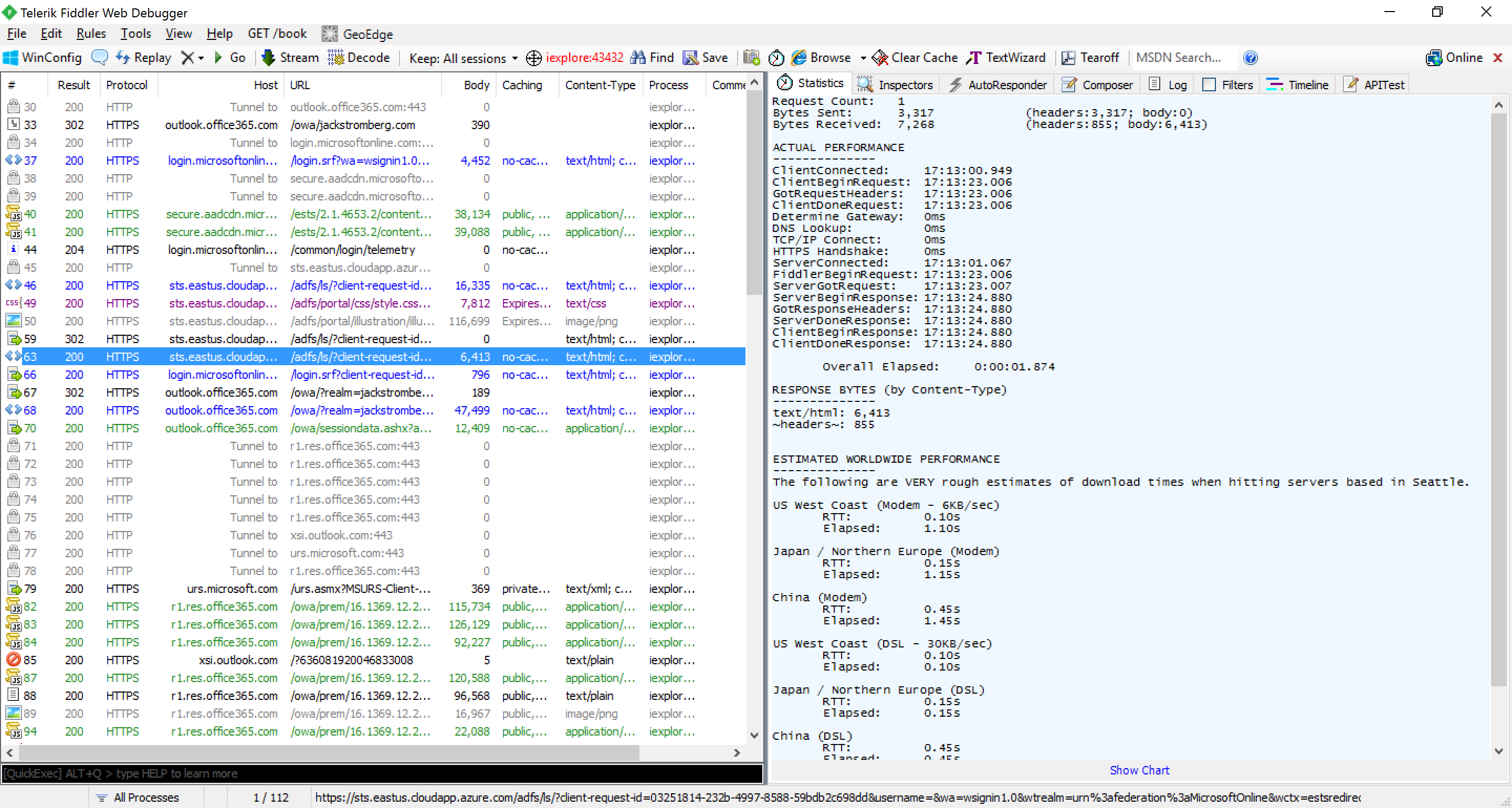
- At this point, you should be able to capture the traffic through the Fiddler application on your Windows machine; see the screenshot below showing traffic from the android device
Remove the Fiddler SSL certificate
- Slide down the notifications drawer from the top of the screen and hit the Settings (gear) icon in the top right

- Select Security
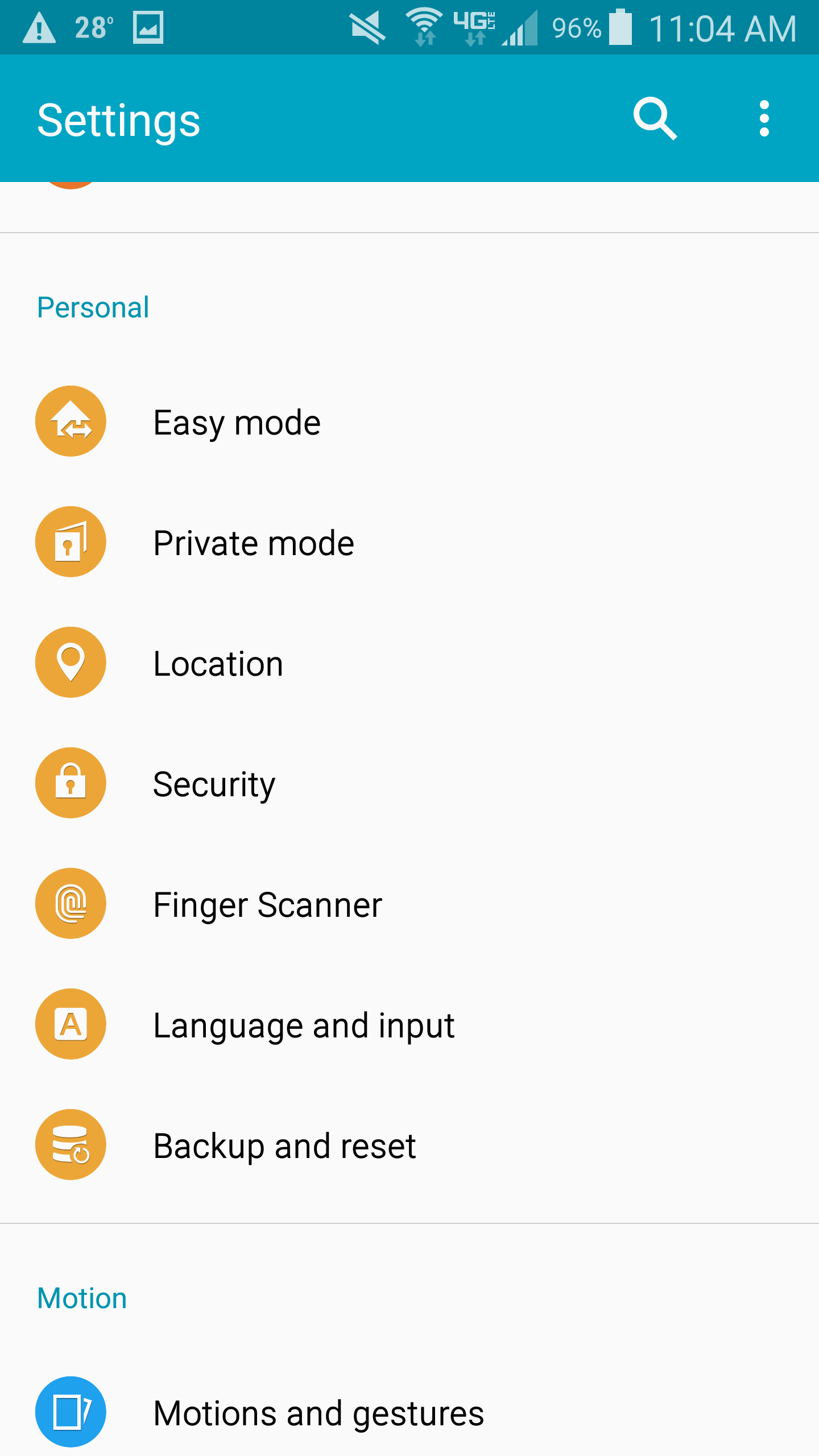
- Select Trusted credentials
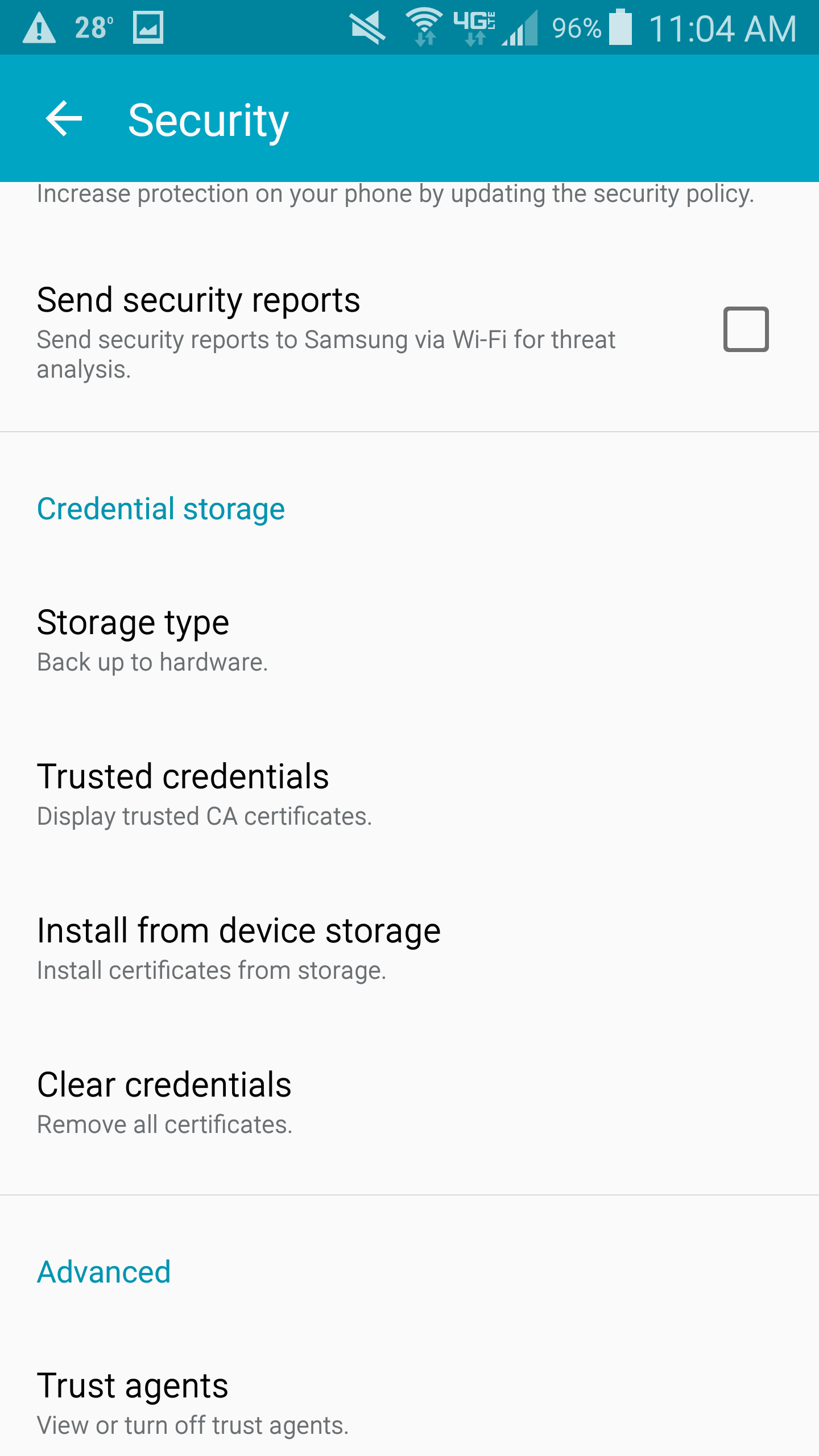
- Select the User tab on the Trusted credentials window
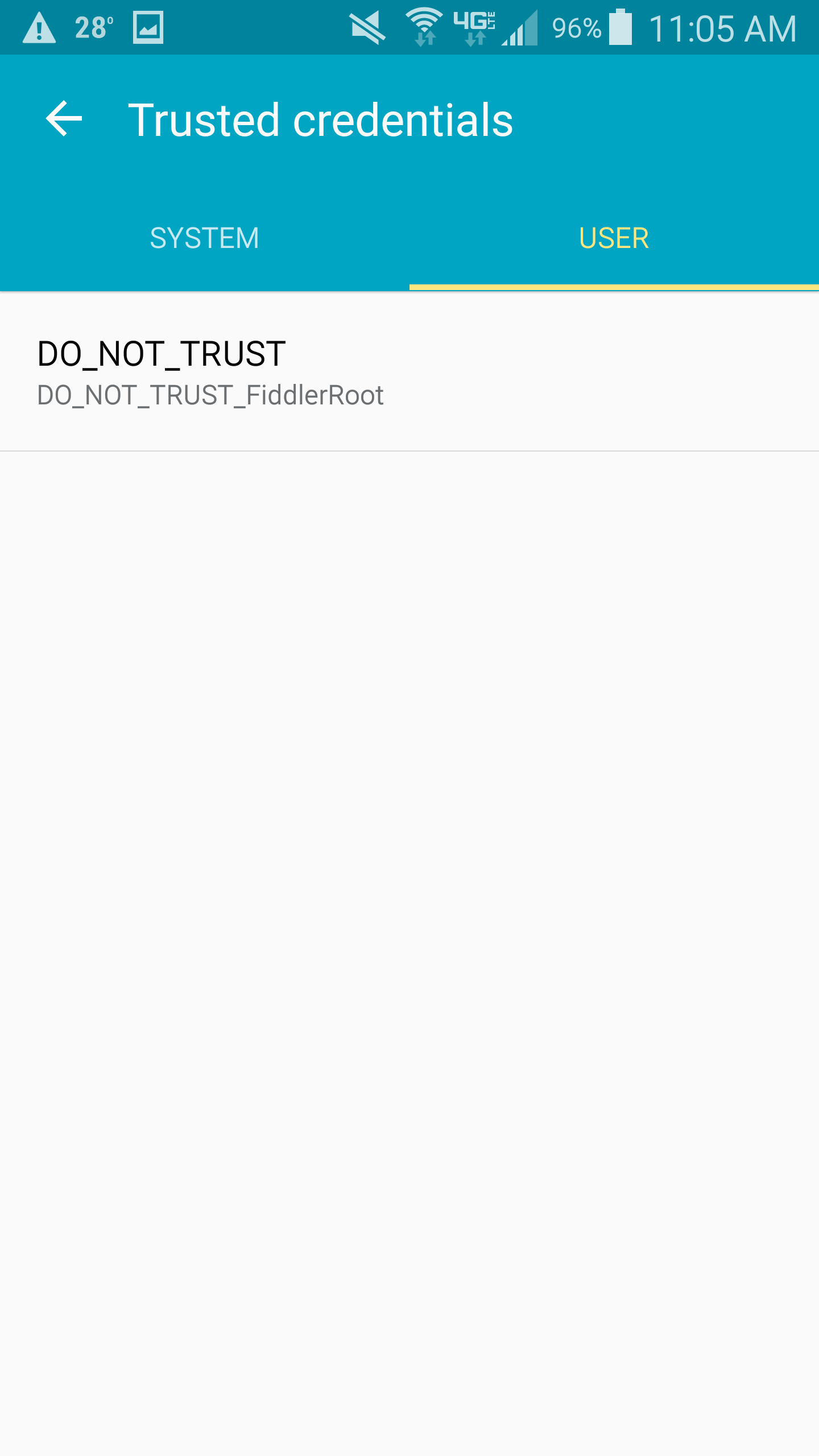
- Scroll down through the certificate information and towards the bottom you will see a Remove button; press the REMOVE button.