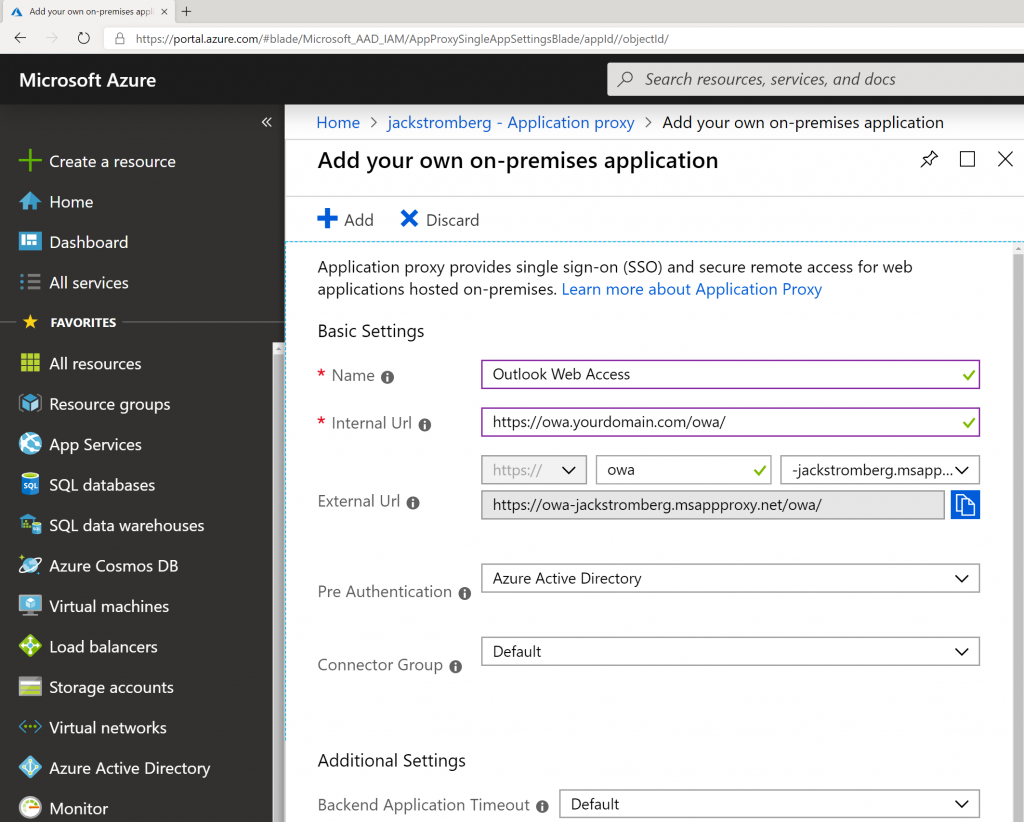
One thing that is a bummer is Exchange online does not support setting an autoreply / out of office message for a distribution list. Usually if you want such functionality, you'd convert the distribution list to a shared mailbox and configure the autoreply or use a 3rd party utility, or potentially come up with some complex transform rule.
Solution
One workaround you can apply is to enable out of office / autoreply messages from recipients in the distribution list. By default, Exchange Online will suppress autoreply messages when going to a distribution list, but you can quickly configure the behavior to allow the messages per distribution list.
Steps
- Install Exchange Online PowerShell module
- Open PowerShell as an administrator and execute the following command:
Install-Module exchangeonlinemanagement
- Open PowerShell as an administrator and execute the following command:
- Import the module for use
- Import-Module ExchangeOnlineManagement
- Login to Exchange online
- Connect-ExchangeOnline -UserPrincipalName [email protected]
- Configure the distribution list to allow the out of office / autoreply messages to be returned to the sender / originator.
Set-DistributionGroup -identity [email protected] -SendOofMessageToOriginatorEnabled $true
Result
Now when someone emails the distribution list, they will receive an out of office / autoreply if configured by an individual member. Note, if multiple members have the autoreply configured, the sender/originator will receive multiple replies.