As of 11/11/2014, Microsoft has released their next generation tool for providing synchronization between an on-premise Active Directory environment and Microsoft based cloud service (Azure, Office 365 Suite (Lync Online, CRM, SharePoint, Exchange, etc.)). The utility is now referenced as Microsoft Azure Active Directory Sync Services (AADSync).
In this tutorial, we will go over the process to ensure you are on the new generation of their synchronization tool. The process is fairly straight forward, uninstall the old DirSync utility, install the new AADSync utility. If you wish to install the utility on a new server, stop the DirSync service, install the AADSync utility on the new server, and then uinstall DirSync after you have verified synchronization is successful on the new machine.
Here is the uninstall DirSync and install AADSync process
- Download a copy of the AADSync utility from Microsoft's website: http://www.microsoft.com/en-us/download/details.aspx?id=44225
- Login to the server currently running DirSync
- Open up Control Panel
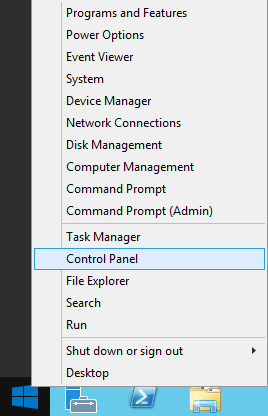
- Select Programs and Features (notice I am in the View By Small icons view)
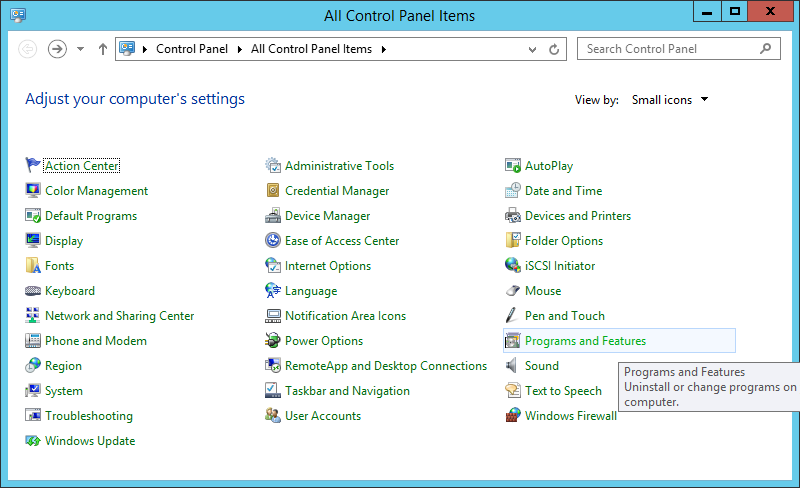
- Uninstall the Windows Azure Active Directory Sync tool
- Select Yes to uninstall when prompted

- Uninstall Forefront Identity Manager Synchronization Service if it wasn't uninstalled already
- Run the MicrosoftAzureADConnectionTool.exe application you downloaded from Microsoft
- Check I agree to the license terms and click Install
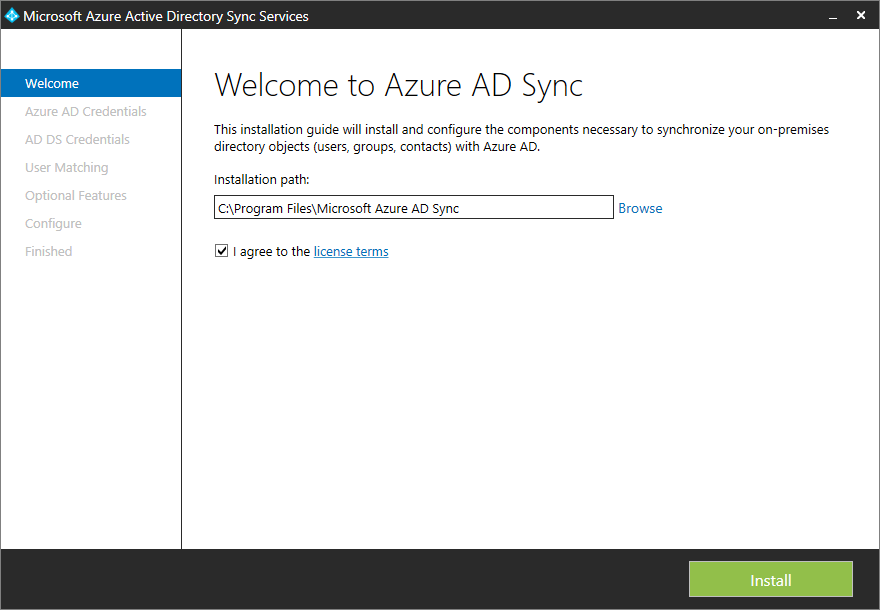
- Once the install has finished, open up Computer Management and navigate to System Tools -> Local Users and Groups, Groups, and double click on ADSyncAdmins
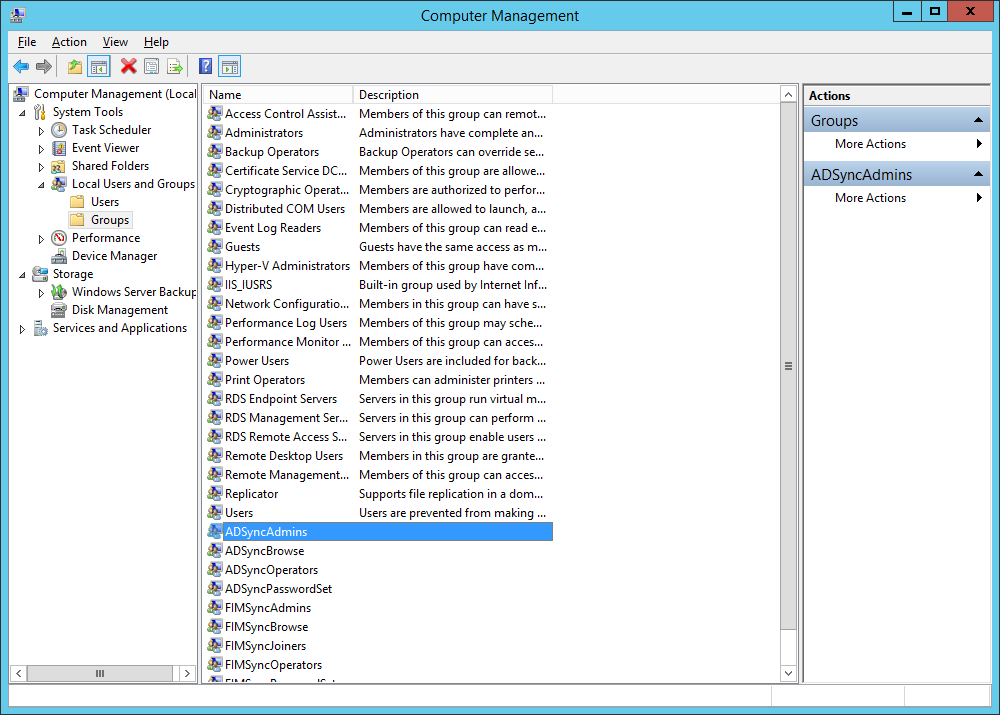
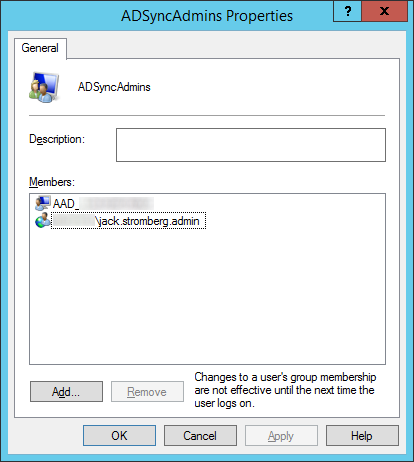
- Ensure your user account, user group, or local machine has been added to the security group
- Log out of Windows
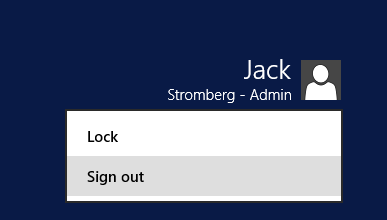
- Note: This step is needed to ensure you have proper user privileges when running the sync tool. When running through the sync tool's installer, your user account will automatically be placed in a local security group called ADSyncAdmins. A logout is needed to update your session otherwise you may receive the following error message:
Your account is not a member of the ADSyncAdmins security group. If you have recently installed Azure AD Sync, sign out before running this installation guide again.
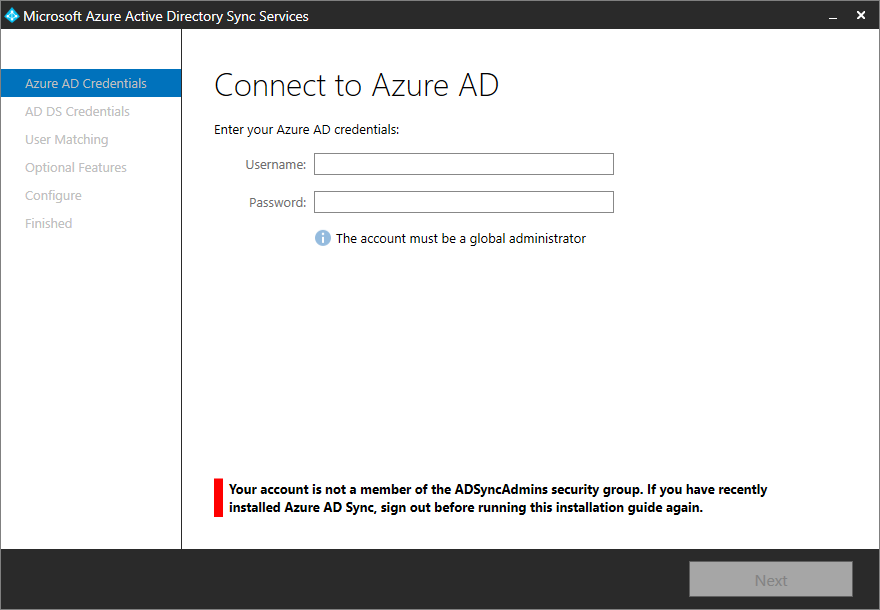
- Note: This step is needed to ensure you have proper user privileges when running the sync tool. When running through the sync tool's installer, your user account will automatically be placed in a local security group called ADSyncAdmins. A logout is needed to update your session otherwise you may receive the following error message:
- Upon login, open up the DirectorySyncTool application

- Enter your Azure or Office 365 admin credentials and click Next
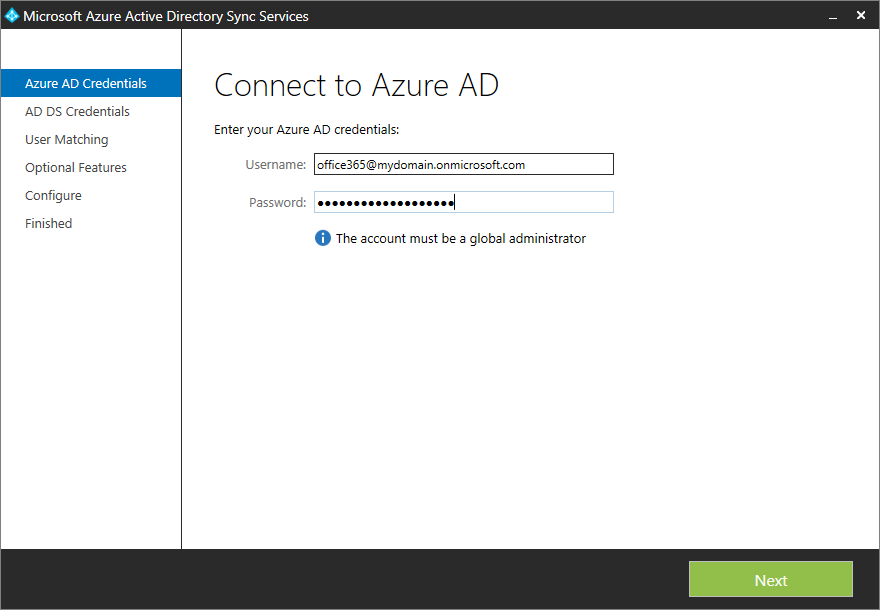
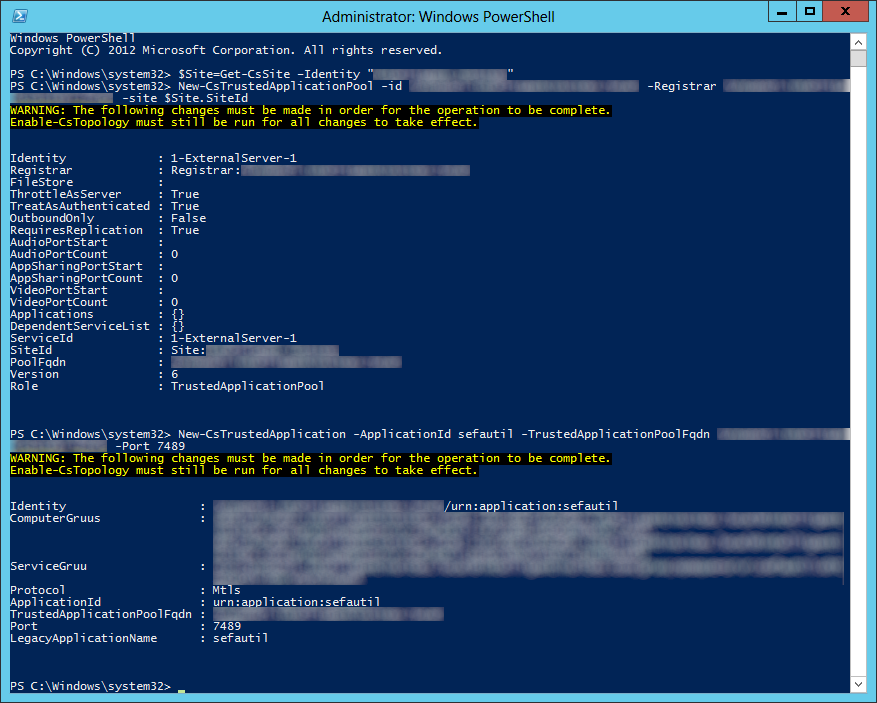
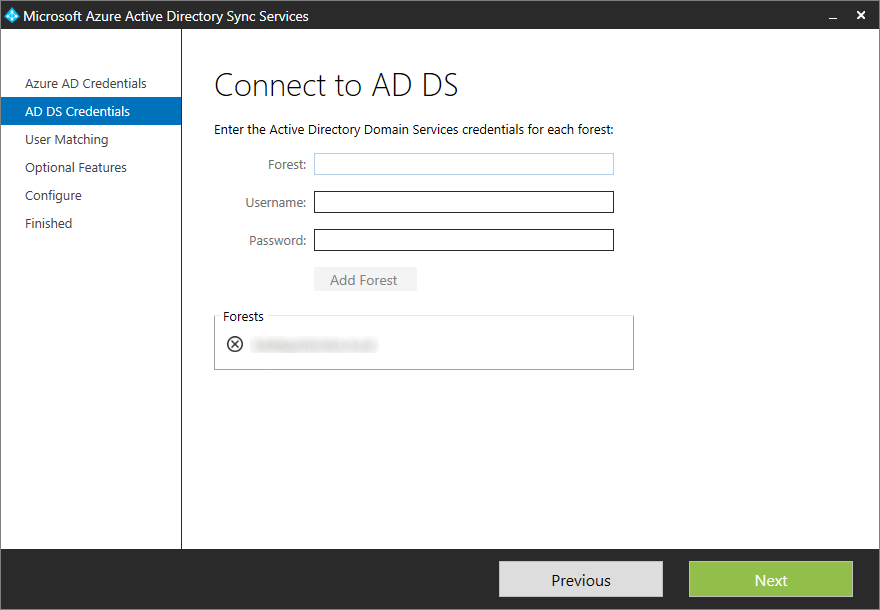
- Enter in your forest name, username (must be in domain\username format), and password (Active Directory on-premise credentials) and click Add Forest

- Note: If you are unsure what your forest name is, login to your domain controller and execute the following powershell command to list all forests in your deployment:
Get-AdForest | FT Name
- Note: If you are unsure what your forest name is, login to your domain controller and execute the following powershell command to list all forests in your deployment:
- Click Next once your forest has been validated
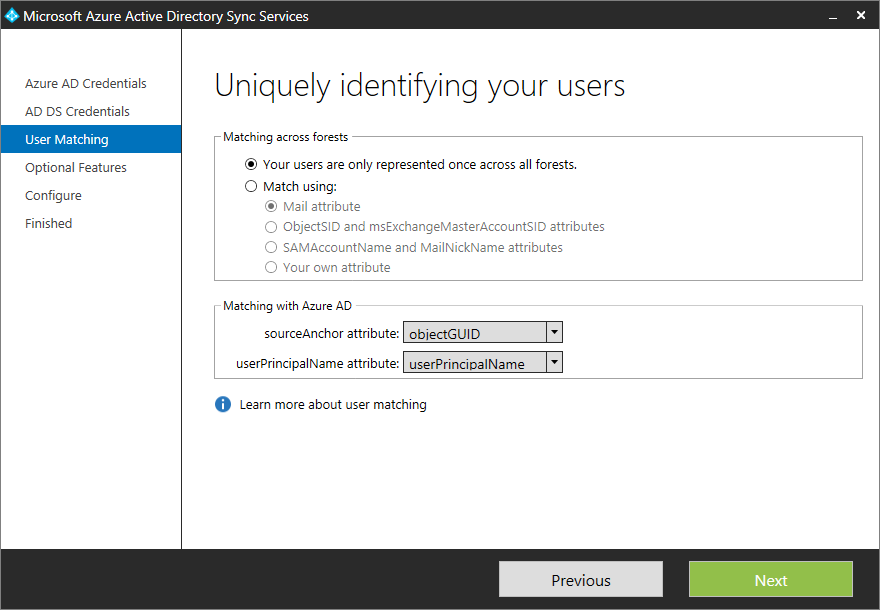
- Click Next on User Matching
- Check the boxes that are applicable to your deployment and click Next
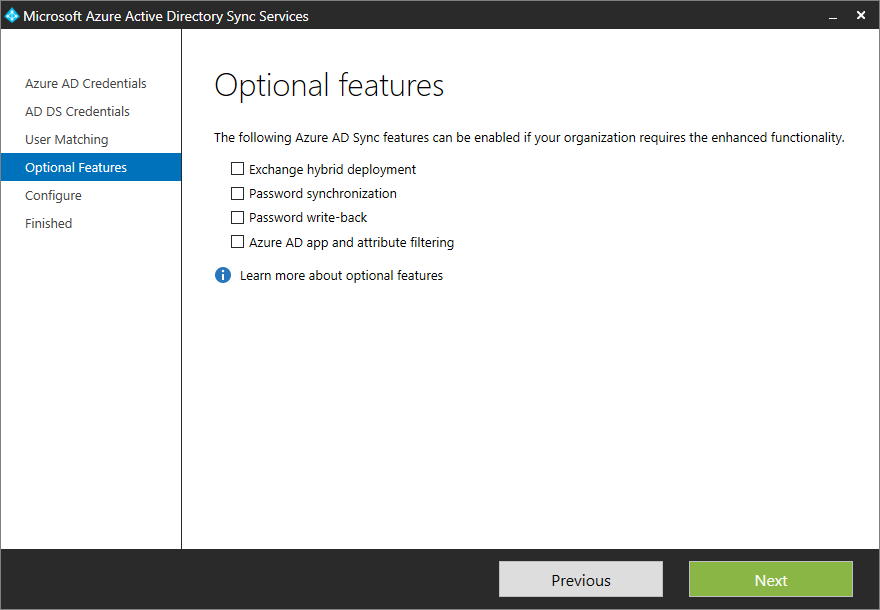
- Click Configure
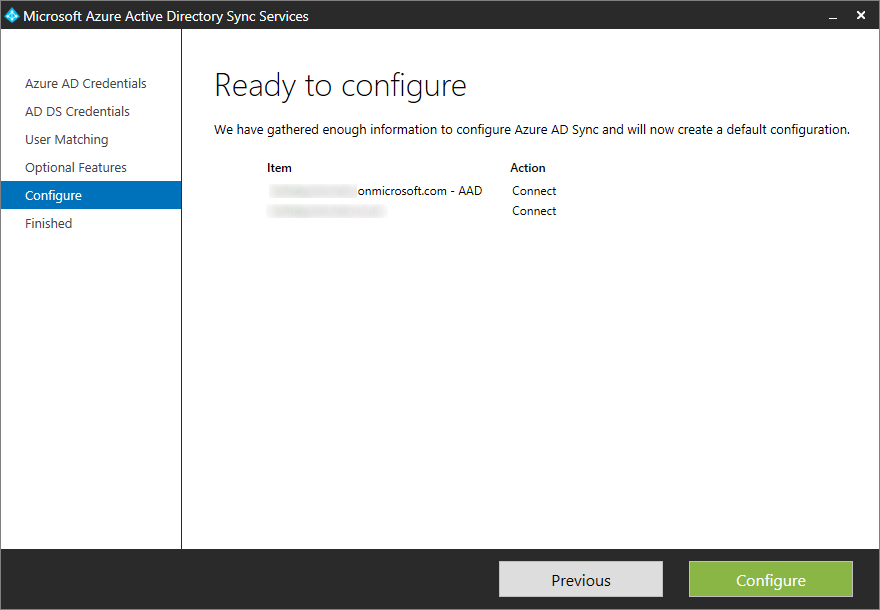
- Click Finish