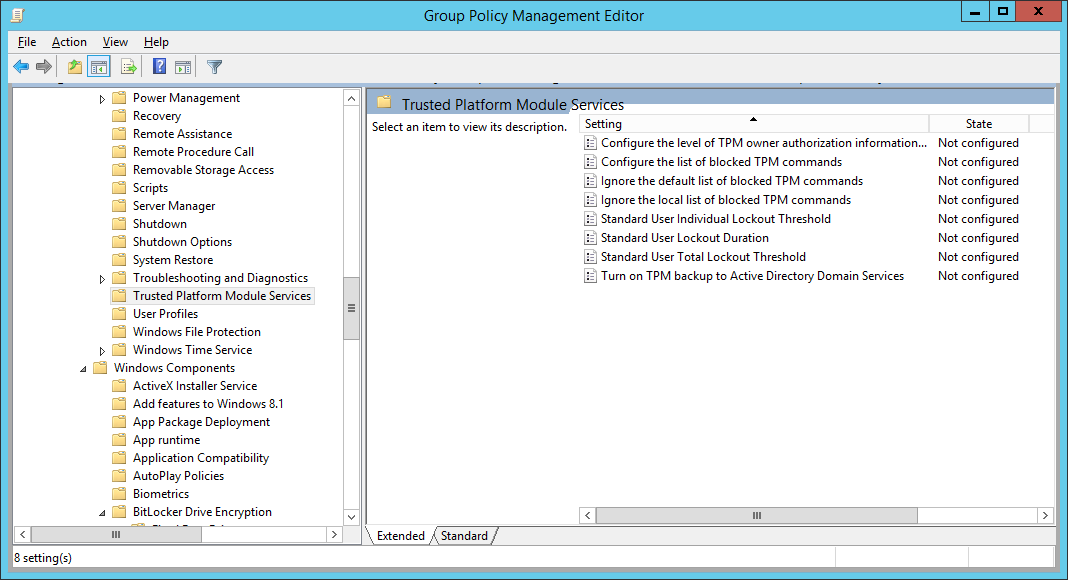
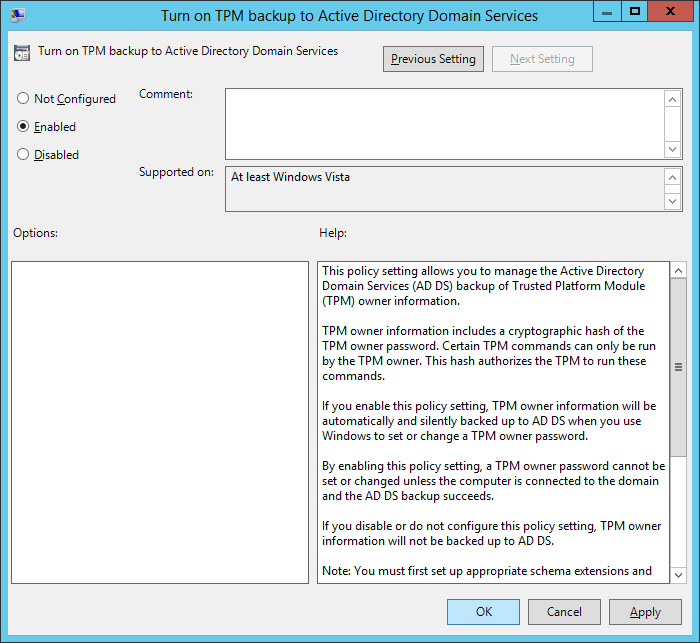
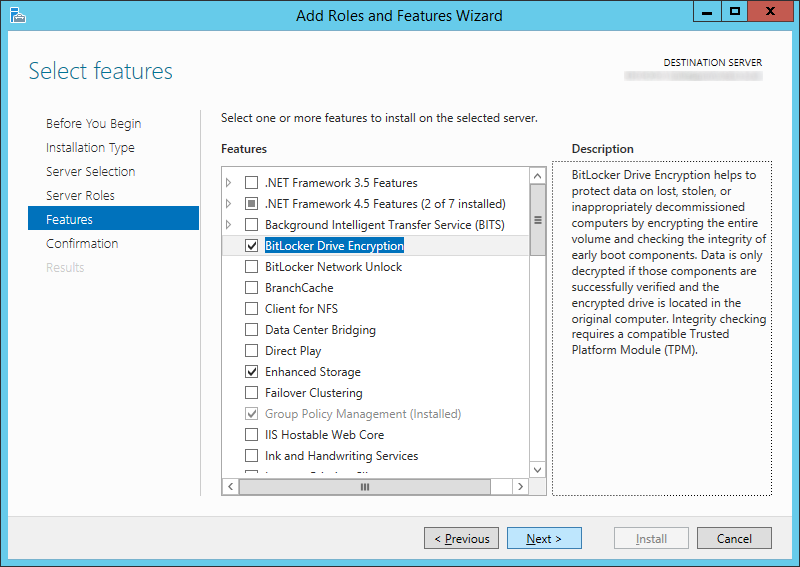
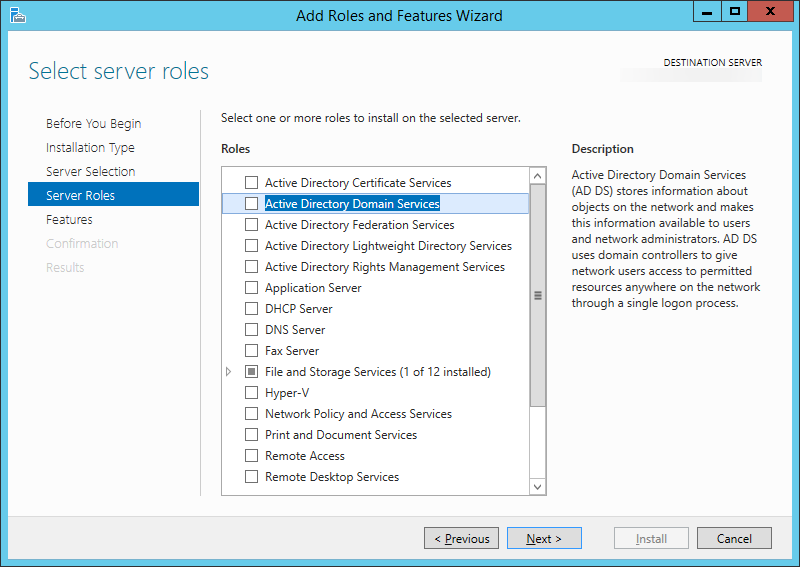
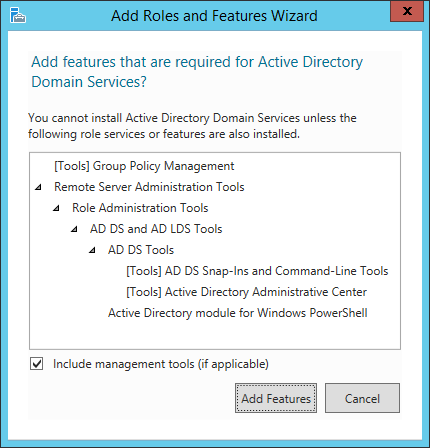
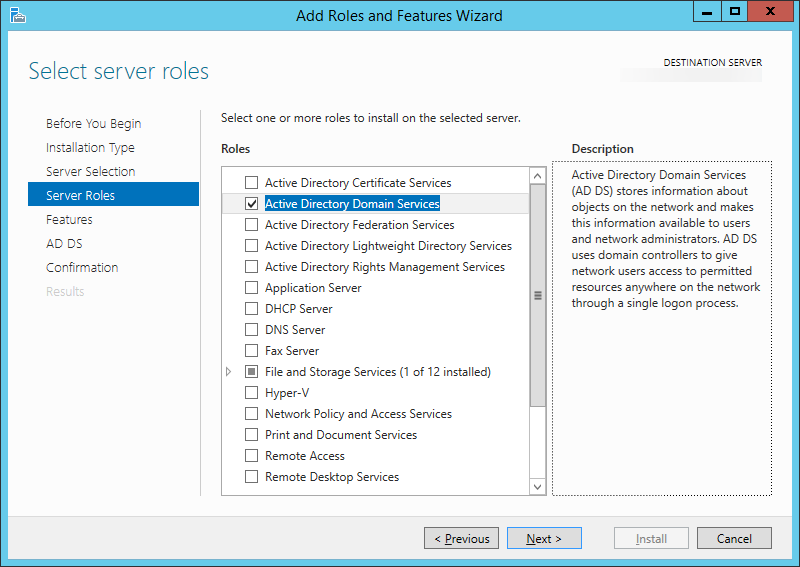
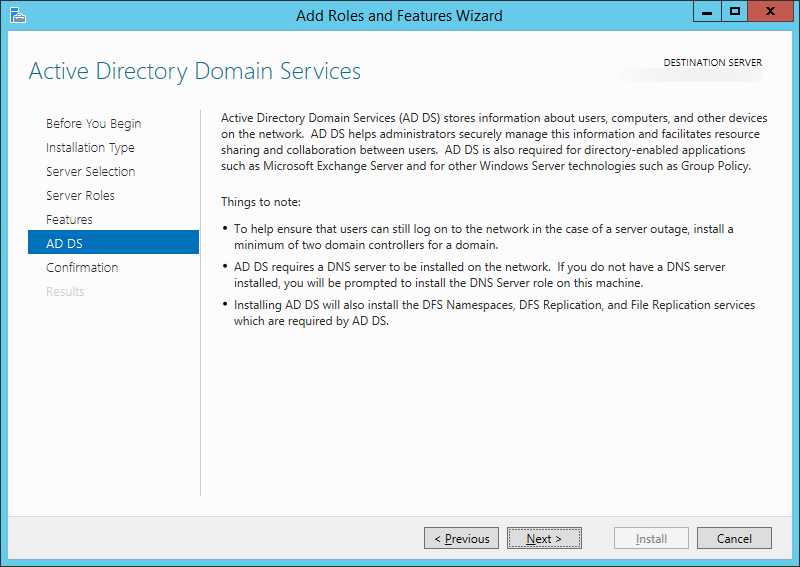
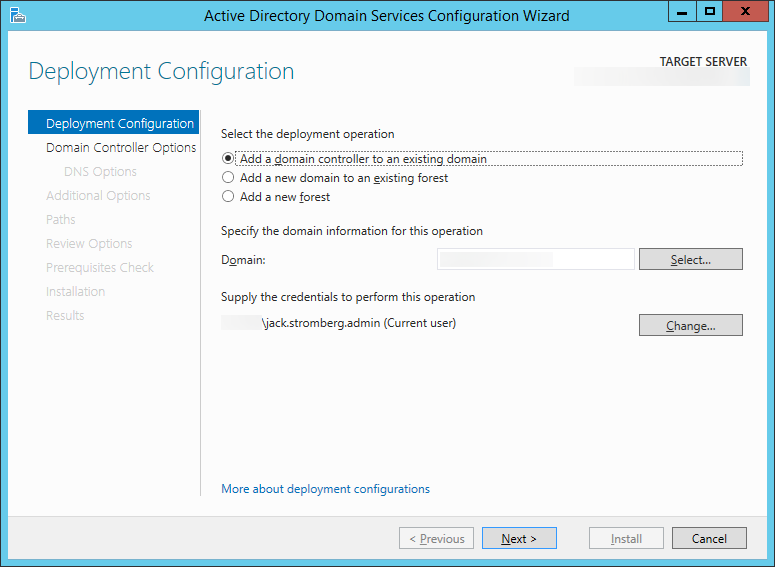
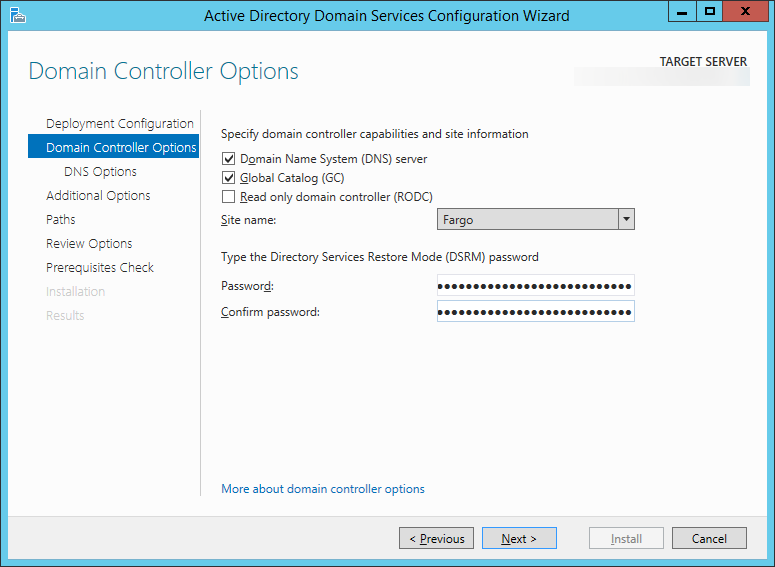
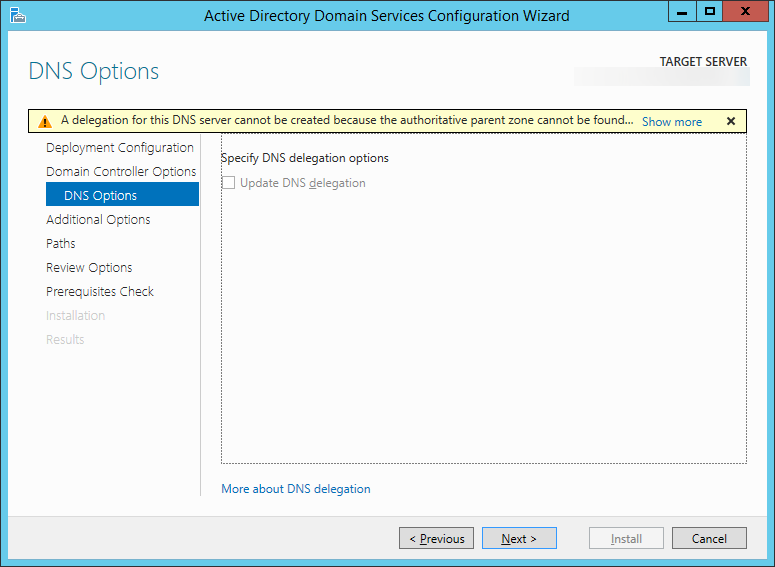
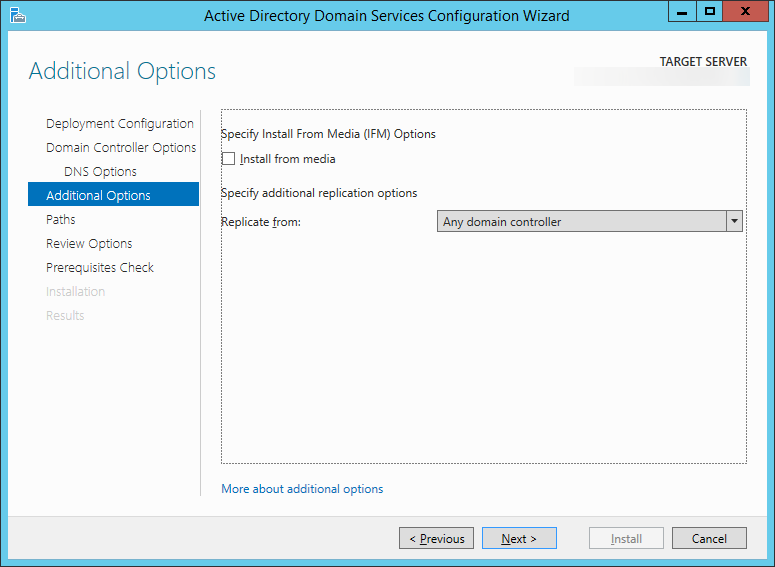
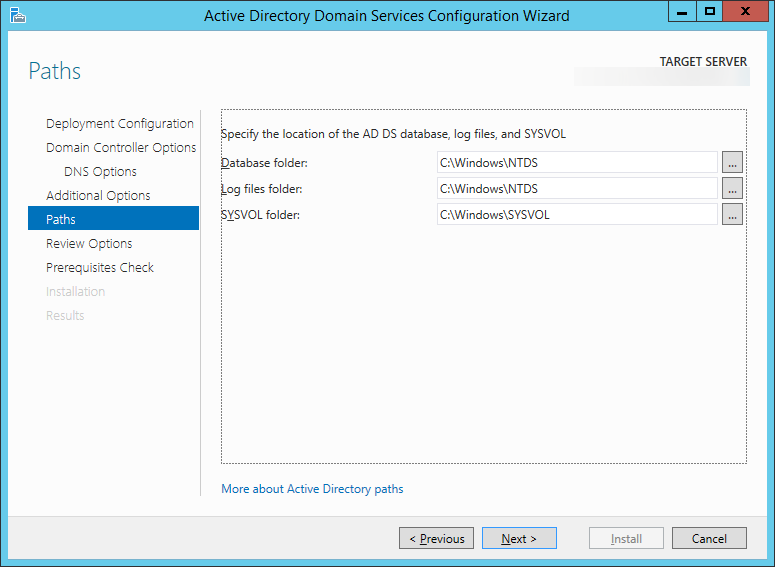
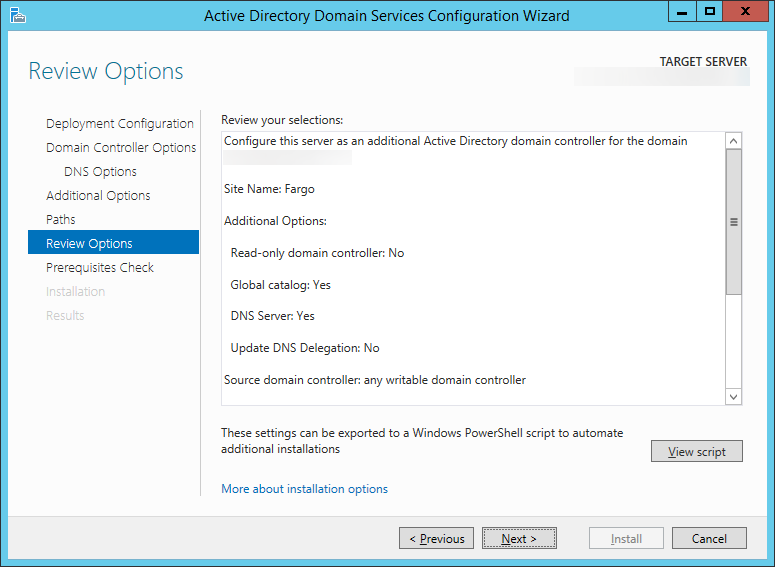
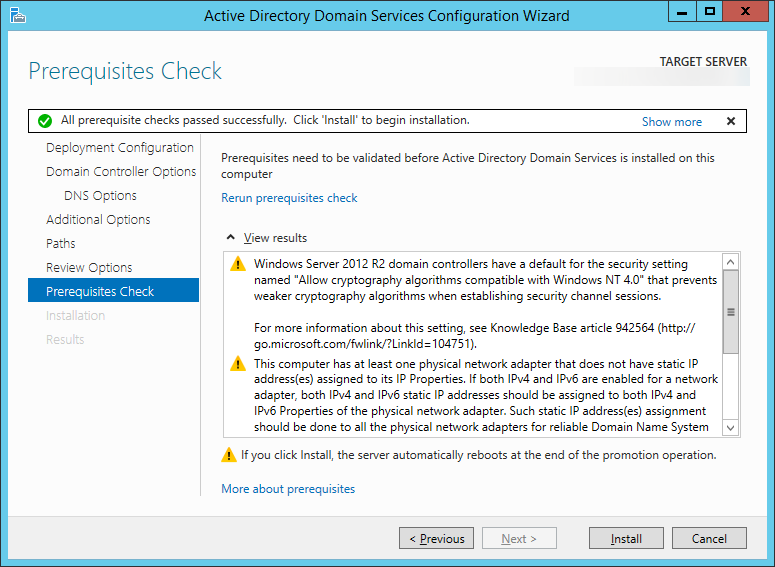
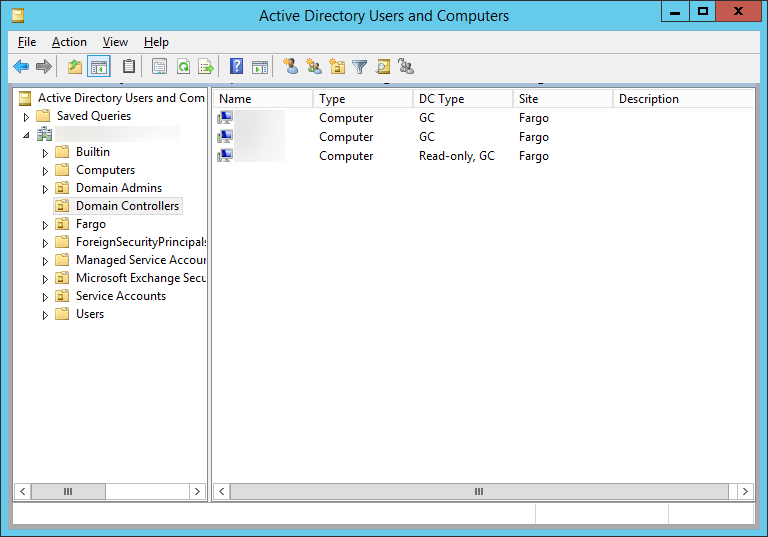
| Synced Object Attribute |
User |
Group |
Contact (Src) |
Description |
| assistant |
Read |
- |
Read |
The name of the assistant for an account. |
| authOrig |
Read |
Read |
Read |
Relationship that indicates that the mailbox for the target object is authorized to send mail to the source object. |
| C |
- |
- |
Read |
Two-letter ISO 3166 [ISO3166] country code. |
| cn |
Read |
Read |
Read |
The common name of the object. |
| co |
Read |
- |
Read |
The country/region in which the person (user or contact) or company is located. |
| company |
Read |
- |
Read |
The person's (user or contact) company name. |
| countryCode |
Read |
- |
Read |
The country code for person's (user or contact) language of choice. |
| department |
Read |
- |
Read |
The name of the person's (user or contact) department. |
| description |
Read |
Read |
Read |
Human-readable descriptive phrases about the object. |
| displayName |
Read |
Read |
Read |
The display name for an object, usually the combination of the person's first name, middle initial, and last name. |
| dLMemRejectPerms |
Read |
Read |
Read |
Relationship that indicates that members of the target object are not authorized to send mail to the source object. |
| dLMemSubmitPerms |
Read |
Read |
Read |
Relationship that indicates that members of the target object are authorized to send mail to the source object. |
| ExtensionAttribute1 |
Read |
Read |
Read |
Custom attribute that is defined in the customer on-premises directory. |
| ExtensionAttribute10 |
Read |
Read |
Read |
Custom attribute that is defined in the customer on-premises directory. |
| ExtensionAttribute11 |
Read |
Read |
Read |
Custom attribute that is defined in the customer on-premises directory. |
| ExtensionAttribute12 |
Read |
Read |
Read |
Custom attribute that is defined in the customer on-premises directory. |
| ExtensionAttribute13 |
Read |
Read |
Read |
Custom attribute that is defined in the customer on-premises directory. |
| ExtensionAttribute14 |
Read |
Read |
Read |
Custom attribute that is defined in the customer on-premises directory. |
| ExtensionAttribute15 |
Read |
Read |
Read |
Custom attribute that is defined in the customer on-premises directory. |
| ExtensionAttribute2 |
Read |
Read |
Read |
Custom attribute that is defined in the customer on-premises directory. |
| ExtensionAttribute3 |
Read |
Read |
Read |
Custom attribute that is defined in the customer on-premises directory. |
| ExtensionAttribute4 |
Read |
Read |
Read |
Custom attribute that is defined in the customer on-premises directory. |
| ExtensionAttribute5 |
Read |
Read |
Read |
Custom attribute that is defined in the customer on-premises directory. |
| ExtensionAttribute6 |
Read |
Read |
Read |
Custom attribute that is defined in the customer on-premises directory. |
| ExtensionAttribute7 |
Read |
Read |
Read |
Custom attribute that is defined in the customer on-premises directory. |
| ExtensionAttribute8 |
Read |
Read |
Read |
Custom attribute that is defined in the customer on-premises directory. |
| ExtensionAttribute9 |
Read |
Read |
Read |
Custom attribute that is defined in the customer on-premises directory. |
| facsimiletelephonenumber |
Read |
- |
Read |
Telephone numbers (and, optionally, the parameters) for facsimile terminals. |
| givenName |
Read |
- |
Read |
Name strings that are the part of a person's (user or contact) name that is not their surname. |
| GroupType |
- |
Read |
- |
Flag attribute indicating the type of group (security, global, etc.) |
| hideDLMembership |
- |
Read |
- |
Hide the membership list on a distribution list from senders. |
| homephone |
Read |
- |
Read |
The person's (user or contact) main home telephone number. |
| info |
Read |
Read |
Read |
"Notes" field on "Telephone" tab of ADUC. |
| Initials |
Read |
- |
Read |
Strings of initials of some or all of an individual's names, except the surname(s). |
| ipPhone |
Read |
- |
Read |
The TCP/IP address for the telephone. |
| l |
Read |
- |
Read |
Names of a locality or place, such as a city, county, or other geographic region. |
| legacyExchangeDN |
Read |
Read |
Read |
|
| mail |
Read |
Read |
Read |
The list of email addresses for a person (user or contact). |
| mailnickname |
Read |
Read |
Read |
|
| managedBy |
- |
Read |
- |
Resource/owner relationship, where the source object (a group) is the resource, and the target object is the owner. |
| manager |
Read |
- |
Read |
Manager/direct report relationship between two individuals, where the source object is the direct report, and the target object is the manager. |
| member |
- |
Read |
- |
Membership of the target object (of class User, Contact, or Group) in the group that is identified as the source object. |
| middleName |
Read |
- |
Read |
Additional names for a person (user or contact), for example, middle name, patronymic, matronymic, or other names. |
| mobile |
Read |
- |
Read |
The primary mobile phone number for a person (user or contact). |
| msDS-HABSeniorityIndex |
Read |
Read |
Read |
|
| msDS-PhoneticDisplayName |
Read |
Read |
Read |
|
| MsExchArchiveGUID |
Read |
- |
- |
|
| MsExchArchiveName |
Read |
- |
- |
|
| msExchArchiveStatus |
Read/Write |
- |
- |
Created in the Exchange cloud for "write back" to on-premises when the customer has a cloud archive. |
| msExchAssistantName |
Read |
- |
Read |
The name of the assistant for an account. |
| msExchAuditAdmin |
Read |
- |
- |
|
| msExchAuditDelegate |
Read |
- |
- |
|
| msExchAuditDelegateAdmin |
Read |
- |
- |
|
| msExchAuditOwner |
Read |
- |
- |
|
| MsExchBlockedSendersHash |
Read/Write |
- |
Read |
Populated through an upgrade from Business Productivity Online Standard Suite. Not synced from on-premises. |
| msExchBypassAudit |
Read |
- |
- |
|
| MsExchBypassModerationFromDLMembersLink |
Read |
Read |
Read |
|
| MsExchBypassModerationLink |
Read |
Read |
Read |
|
| msExchCoManagedByLink |
- |
Read |
- |
|
| msExchDelegateListLink |
Read |
- |
- |
|
| msExchELCExpirySuspensionEnd |
Read |
- |
- |
|
| msExchELCExpirySuspensionStart |
Read |
- |
- |
|
| msExchELCMailboxFlags |
Read |
- |
- |
|
| MsExchEnableModeration |
Read |
Read |
- |
|
| msExchExtensionCustomAttribute1 |
Read |
Read |
Read |
|
| msExchExtensionCustomAttribute2 |
Read |
Read |
Read |
|
| msExchExtensionCustomAttribute3 |
Read |
Read |
Read |
|
| msExchExtensionCustomAttribute4 |
Read |
Read |
Read |
|
| msExchExtensionCustomAttribute5 |
Read |
Read |
Read |
|
| MsExchGroupDepartRestriction |
- |
Read |
- |
|
| MsExchGroupJoinRestriction |
- |
Read |
- |
|
| msExchHideFromAddressLists |
Read |
Read |
Read |
Indicator to control the visibility of a mail recipient for name resolution. |
| MsExchImmutableID |
Read |
- |
- |
|
| msExchLitigationHoldDate |
Read |
Read |
Read |
|
| msExchLitigationHoldOwner |
Read |
Read |
Read |
|
| MsExchMailboxGuid |
Read |
- |
- |
The GUID of the user’s mailbox. |
| msExchMailboxAuditEnable |
Read |
- |
- |
|
| msExchMailboxAuditLogAgeLimit |
Read |
- |
- |
|
| MsExchModeratedByLink |
Read |
Read |
Read |
|
| MsExchModerationFlags |
Read |
Read |
Read |
|
| MsExchRecipientDisplayType |
Read |
Read |
Read |
|
| msExchRecipientTypeDetails |
Read |
Read |
Read |
|
| MsExchRemoteRecipientType |
Read |
- |
- |
|
| msExchRequireAuthToSendTo |
Read |
Read |
Read |
When enabled for a distribution list (DL), unauthenticated users are rejected. |
| MsExchResourceCapacity |
Read |
- |
- |
|
| MsExchResourceDisplay |
Read |
- |
- |
|
| MsExchResourceMetaData |
Read |
- |
- |
|
| MsExchResourceSearchProperties |
Read |
- |
- |
|
| msExchRetentionComment |
Read |
Read |
Read |
|
| msExchRetentionURL |
Read |
Read |
Read |
|
| MsExchSafeRecipientsHash |
Read/Write |
- |
Read |
Populated through an upgrade from Business Productivity Online Standard Suite. Not synced from on-premises. |
| MsExchSafeSendersHash |
Read/Write |
- |
Read |
Populated through an upgrade from Business Productivity Online Standard Suite. Not synced from on premises. |
| MsExchSenderHintTranslations |
Read |
Read |
Read |
|
| msExchTeamMailboxExpiration |
Read |
- |
- |
|
| msExchTeamMailboxOwners |
Read |
- |
- |
|
| msExchTeamMailboxSharePointLinkedBy |
Read |
- |
- |
|
| msExchTeamMailboxSharePointUrl |
Read |
- |
- |
|
| msExchUCVoiceMailSettings |
Read/Write |
- |
- |
|
| msExchUsageLocation |
Read |
- |
- |
|
| msExchUserHoldPolicies |
Read/Write |
- |
- |
Litigation Hold allows cloud services to determine which users are under Litigation Hold |
| msOrg-IsOrganizational |
- |
Read |
- |
|
| msRTCSIP-ApplicationOptions |
Read |
- |
- |
|
| msRTCSIP-DeploymentLocator |
Read |
- |
Read |
Fully qualified DNS name of the Microsoft Lync Server 2010 deployment, as specified in the authoritative (customer, on-premises) directory. |
| msRTCSIP-Line |
Read |
- |
Read |
The device ID (either the Session Initiation Protocol (SIP) uniform resource identifier (URI) or the TEL URI) of the telephone that the user controls. |
| msRTCSIP-OwnerUrn |
Read |
- |
- |
|
| msRTCSIP-PrimaryUserAddress |
Read |
- |
Read |
SIP URI for instant messaging, as specified in the authoritative (customer, on-premise) directory. |
| msRTCSIP-UserEnabled |
Read |
- |
Read |
Indicates whether the user is currently enabled for SIP instant messaging, as specified in the authoritative (customer, on-premises) directory. |
| msRTCSIP-OptionFlags |
Read |
- |
Read |
|
| objectGUID |
Read |
Read |
Read |
Key for the object: this key is immutable, even if the object moves from one context to another, for example, as a result of a company merge or split. |
| oOFReplyToOriginator |
- |
Read |
- |
Governs whether out-of-office notifications should be sent to a sender of a message to this distribution list (DL). |
| otherFacsimileTelephone |
Read |
- |
Read |
A list of alternative facsimile numbers. |
| otherHomePhone |
Read |
- |
Read |
A list of alternative home telephone numbers. |
| otherIpPhone |
Read |
- |
Read |
A list of alternative TCP/IP addresses for the telephone. |
| otherMobile |
Read |
- |
Read |
A list of alternative mobile phone numbers. |
| otherPager |
Read |
- |
Read |
A list of alternative pager numbers. |
| otherTelephone |
Read |
- |
Read |
A list of alternative office telephone numbers. |
| pager |
Read |
- |
Read |
The primary pager number. |
| photo |
Read |
- |
- |
|
| physicalDeliveryOfficeName |
Read |
- |
Read |
Names that a postal service uses to identify a post office. |
| postalCode |
Read |
- |
Read |
Codes that a postal service uses to identify postal service zones. |
| postOfficeBox |
Read |
- |
Read |
Postal box identifiers that a postal service uses when a customer arranges to receive mail at a box on the premises of the postal service. |
| PreferredLanguage |
Read |
- |
- |
The preferred written or spoken language for a user. |
| proxyAddresses |
Read/Write |
Read/Write |
Read/Write |
The address by which a Microsoft Exchange Server recipient object is recognized in a foreign mail system. |
| PublicDelegates |
Read/Write |
Read |
Read |
Cross-premises public delegation: allows users to specify delegates for their mailbox. |
| reportToOriginator |
- |
Read |
- |
Governs whether to send delivery reports to the message originator when a message that is sent to a group is not delivered. The delivery report lets the group owner know that the message was not delivered. |
| ReportToOwner |
- |
Read |
- |
|
| samAccountName |
Read |
- |
- |
|
| sn |
Read |
- |
Read |
Name strings for the family names of a person (user or contact). |
| st |
Read |
- |
Read |
The full names of states or provinces. |
| streetAddress |
Read |
- |
Read |
The person's (user or contact) address. |
| targetAddress |
Read |
- |
Read |
The destination address for the person (user or contact). |
| TelephoneAssistant |
Read |
- |
Read |
|
| telephoneNumber |
Read |
- |
Read |
Telephone numbers that comply with the ITU Recommendation E.123. |
| thumbnailphoto |
Read |
- |
Read |
Persons Photo - 10kb maximum size limit |
| title |
Read |
- |
Read |
The title of a person (user or contact) in the person's organizational context. |
| unauthOrig |
Read |
Read |
Read |
Relationship that indicates that the mailbox for the target object is not authorized to send mail to the source object. |
| url |
Read |
- |
Read |
The list of alternative web pages. |
| userAccountControl |
Read |
- |
- |
Flag attribute to indicate settings. |
| userCertificate |
Read |
Read |
- |
Contains certificates used as part of the Exchange SMIME feature set. |
| UserPrincipalName |
Read |
- |
- |
The user principal name (UPN) that is an Internet-style logon name for a user, as specified in RFC 822. |
| userSMIMECertificate |
Read |
Read |
- |
Contains certificates used as part of the Exchange SMIME feature set. |
| wWWHomePage |
Read |
- |
Read |
The primary web page. |
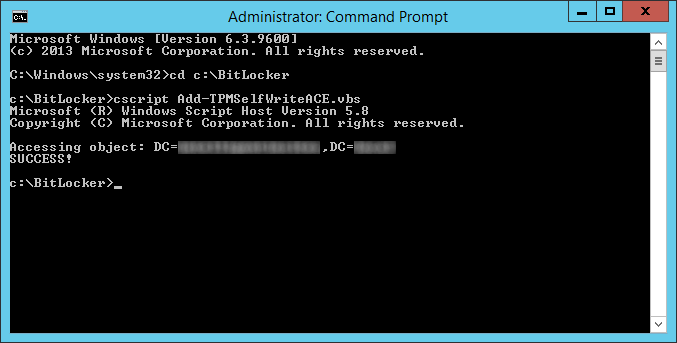

 NOTE
NOTE