Symptom: When upgrading from ADFS v2.0 to ADFS v3 built natively into Server 2012 R2, I noticed Chrome stopped auto-logging in people when trying to hit the ADFS server from inside the corporate network.
Solution: We need to allow NTLM authentication for the Google Chrome useragent.
- Login to your primary ADFS server
- NOTE: This step is no longer applicable on newer versions of Chrome.
This is only applicable if running extremely old versions of Chrome (v50 or lower) -- the fix has been added in Chrome v51 and higher.
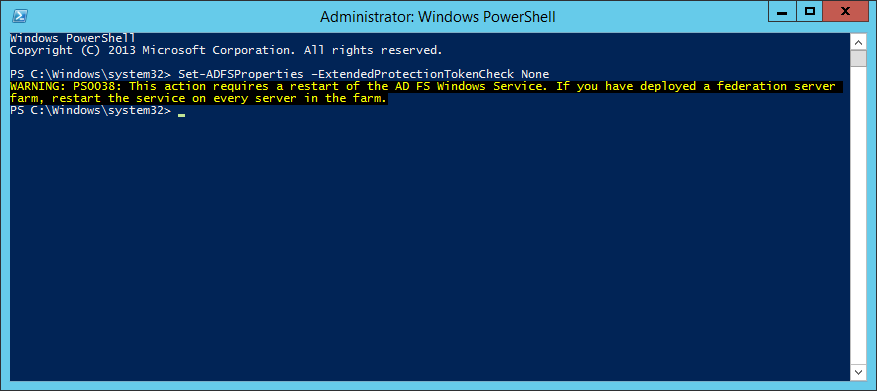
Execute the following command to disable Extended Protection TokenCheck (See notes for what this is at the bottom of this article) - Execute the following command to get the current list of supported user-agents for NTLM authentication
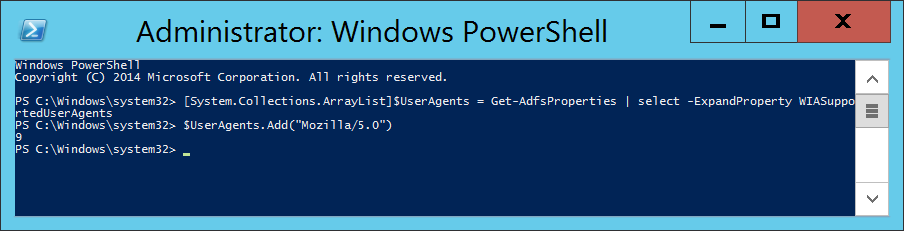
- Execute the following command to inject the user agent into a temporary array of user agents already added to ADFS.
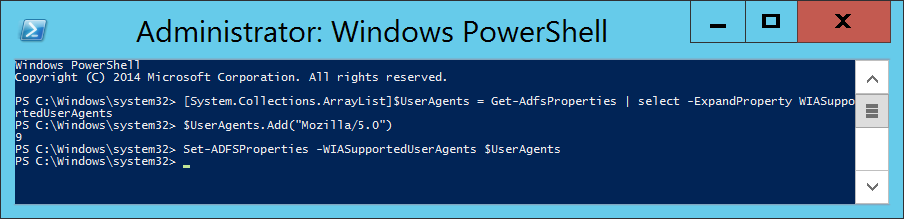
- Execute the following command to commit the change.
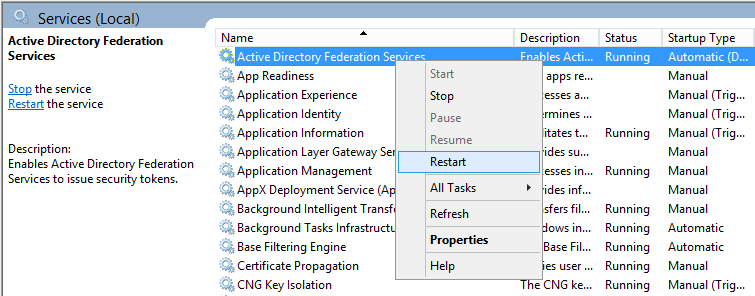
- Restart the Active Directory Federation Services service on each of the ADFS farm servers for the changes to take effect. You do not need to make any changes to the proxy servers.
Notes
Shout out to Jon Payne in the comments section below for the idea of putting all the values into an ArrayList and then committing the arraylist to ADFS vs adding in all the strings manually.
ExtendedProtectionTokenCheck - Copied directly from technet - Specifies the level of extended protection for authentication supported by the federation server. Extended Protection for Authentication helps protect against man-in-the-middle (MITM) attacks, in which an attacker intercepts a client's credentials and forwards them to a server. Protection against such attacks is made possible through a Channel Binding Token (CBT) which can be either required, allowed or not required by the server when establishing communications with clients. http://technet.microsoft.com/en-us/library/ee892317.aspx