Synopsis: When placing a Virtual Machine on the Azure Platform, by default it inherits time controls from the underlying hypervisor: Hyper-V. The default behavior for these VMs is to synchronize the system clock with the host via the Hyper-V TimeSync service (VMIC) for Hyper-V hosts and guests running prior operating systems to Windows Server 2016.
Windows 2016 guests will find the most accurate clock, rather than defaulting to the host. It was for this reason that we advised to manually disable Hyper-V Time Provider setting for machines participating in a domain in Windows 2012R2 and below. More information on Windows Server 2016 time can be found here: https://docs.microsoft.com/en-us/windows-server/identity/ad-ds/get-started/windows-time-service/windows-2016-accurate-time
To disable the Hyper-V Time Provider, we recommend creating a new Group Policy template and targeting your Azure VMs.
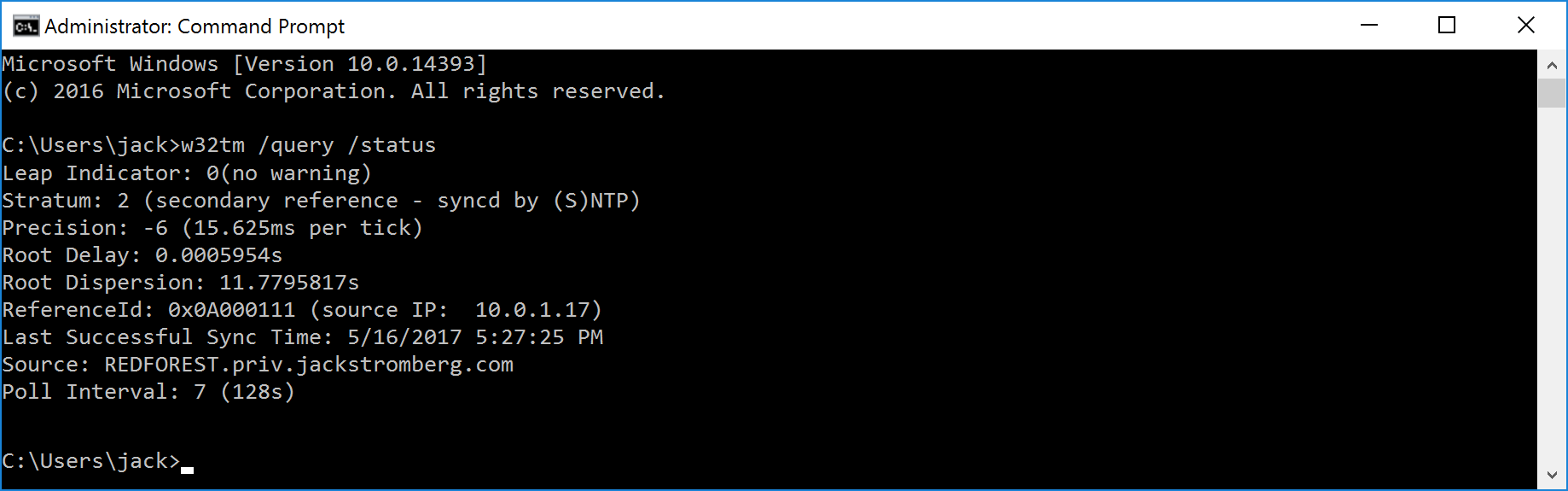
Validate that your machine is synchronized to the Hyper-V Time Provider
Open command prompt and execute the following command: w32tm /query /status
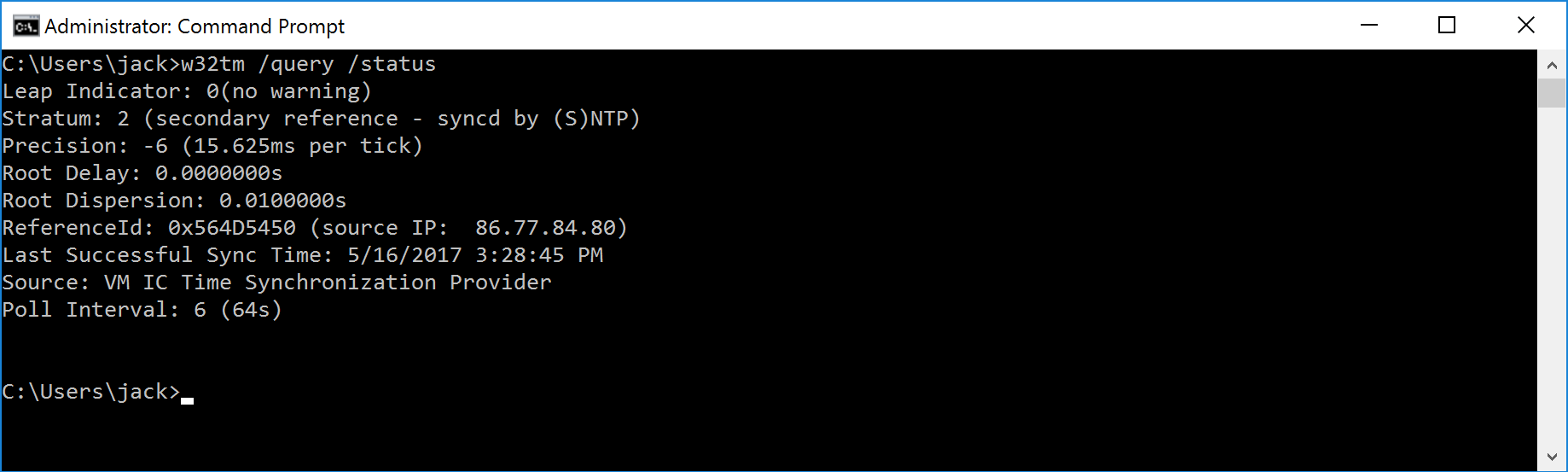
If you see VM IC Time Synchronization Provider, the Guest OS is synchronized to the VM Host
Create a new group policy to disable the Hyper-V Time Provider (VM IC Time Synchronization)
- Create a new Group Policy and target it to an OU that contains the machines synchronized to the Hyper-V Time Provider
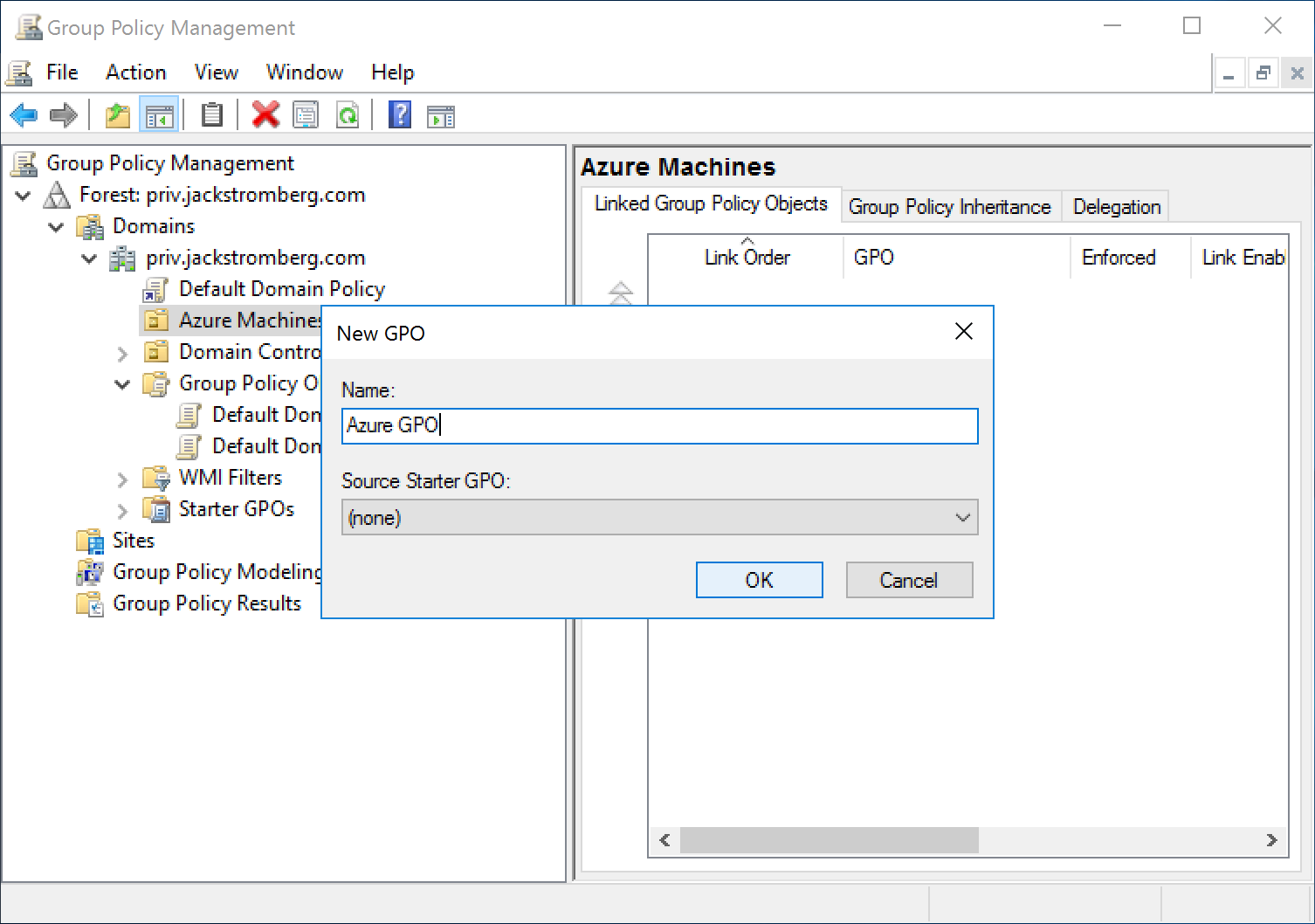
- Edit the new Group Policy Object
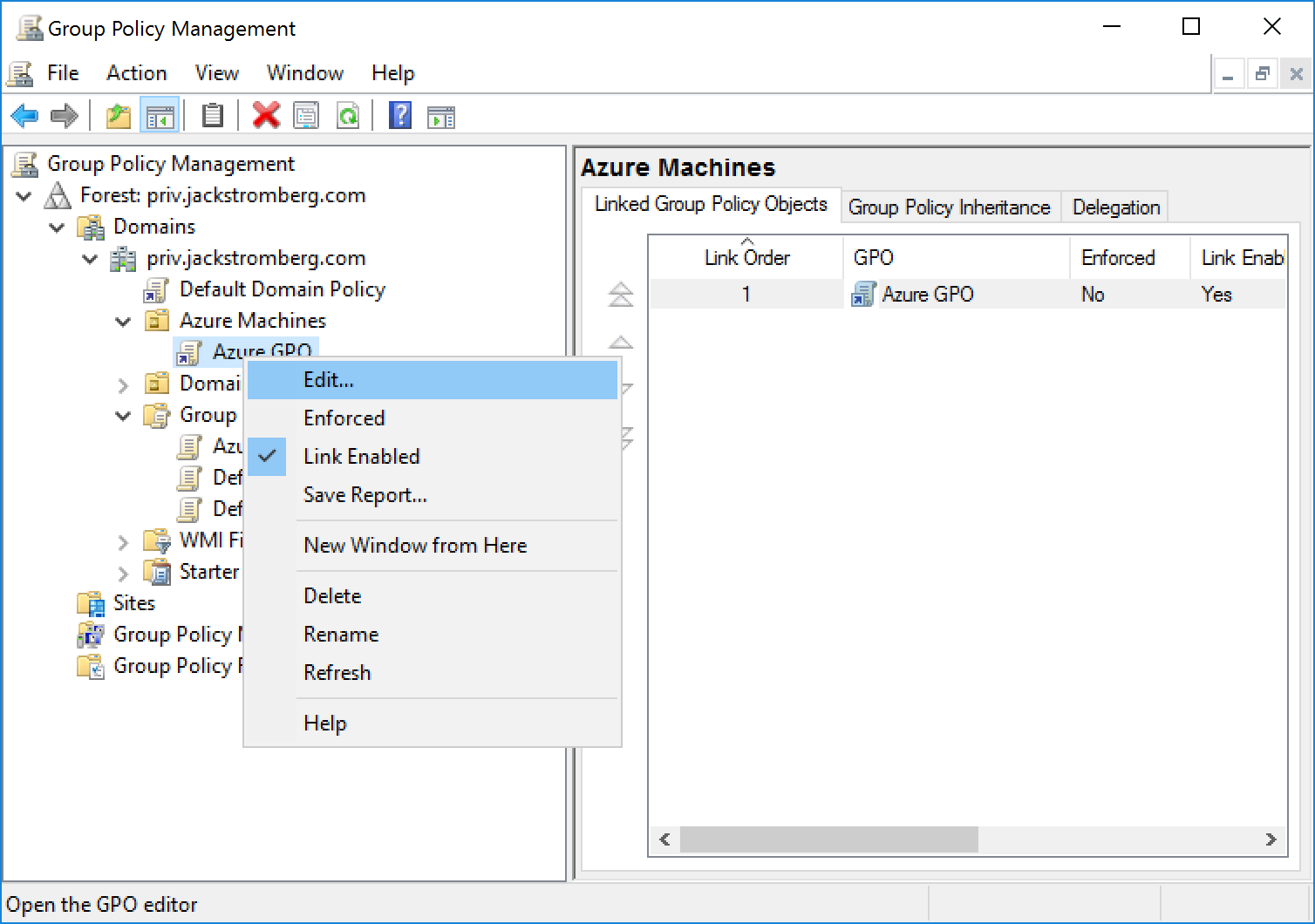
- Navigate to Computer configuration -> Preferences -> Windows Settings -> Registry and Add a new item
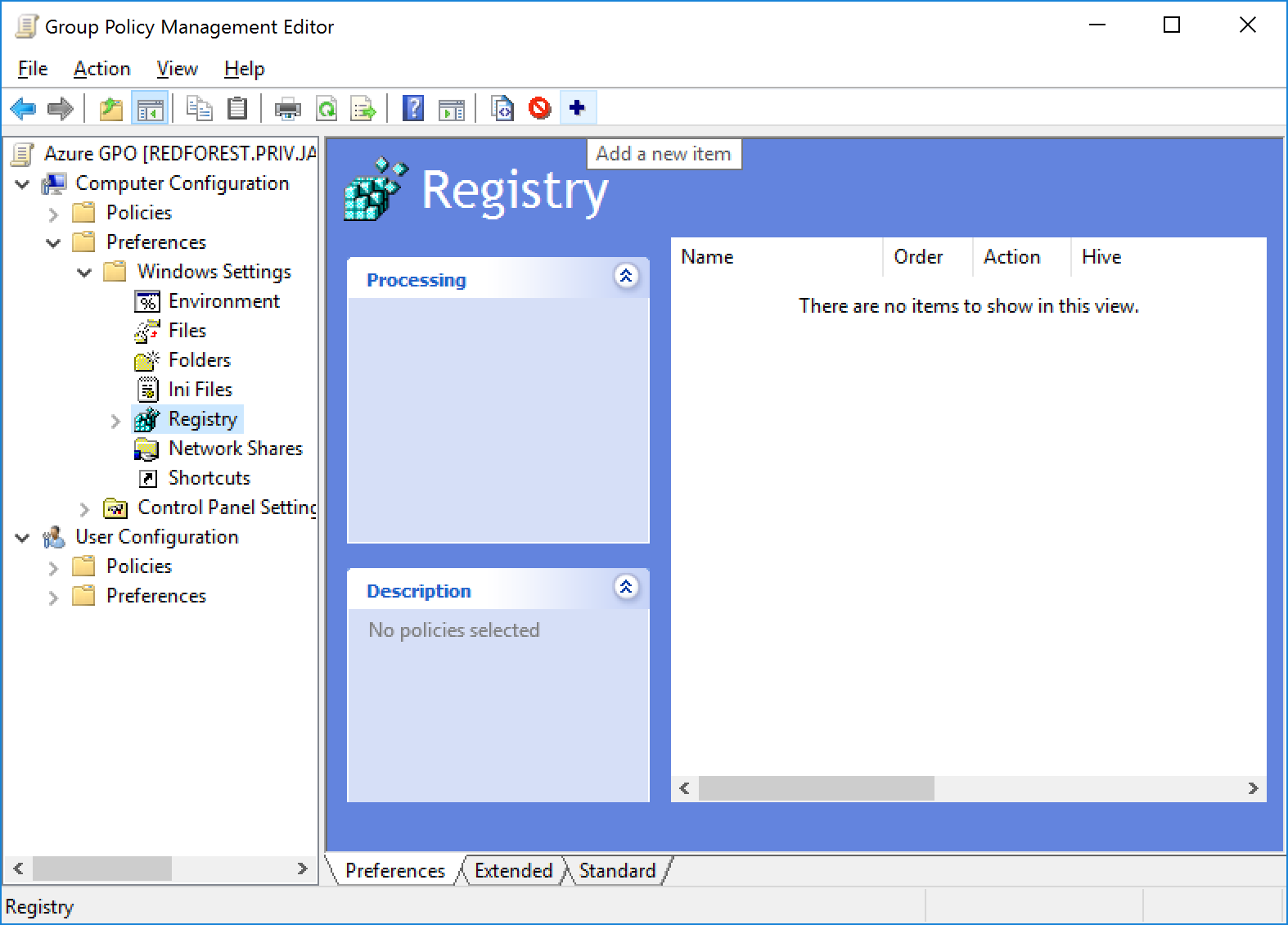
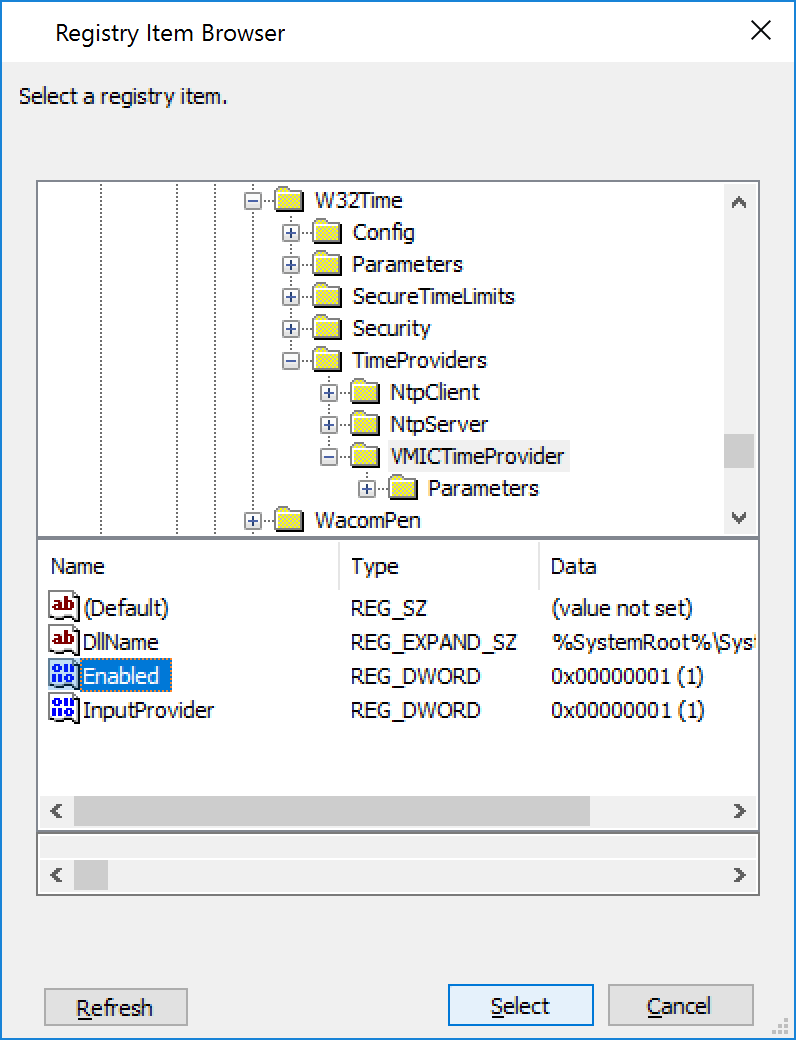
- Navigate to the following Key HKLM:SYSTEM\CurrentControlSet\Services\W32Time\TimeProviders\VMICTimeProvider and select the Enabled Value
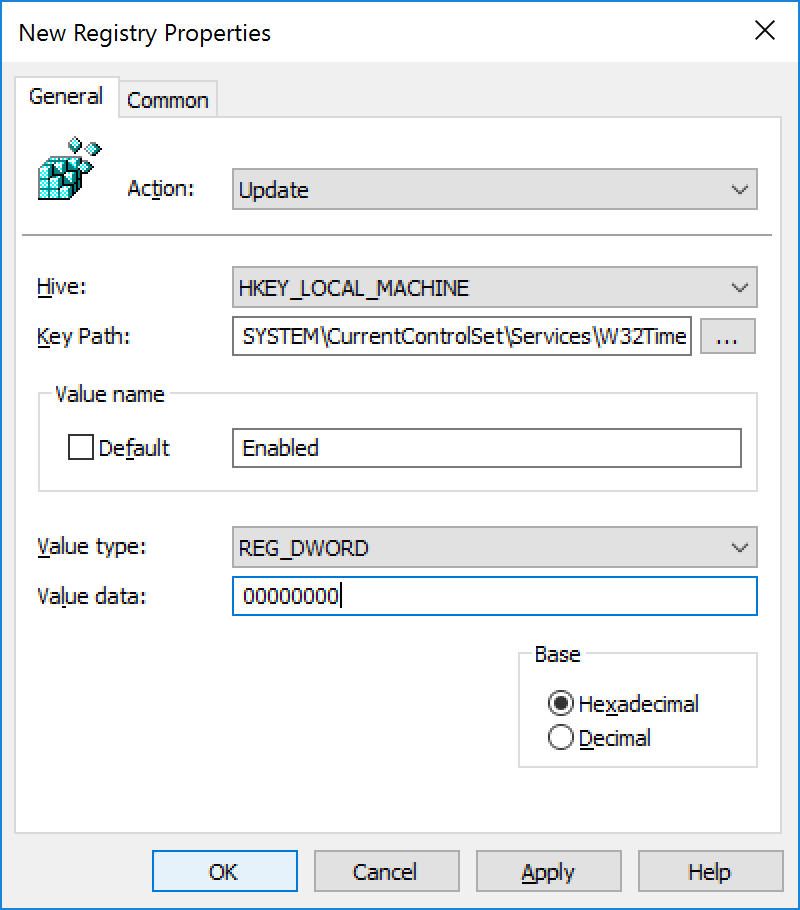
- Change the Value data to 00000000 and click OK
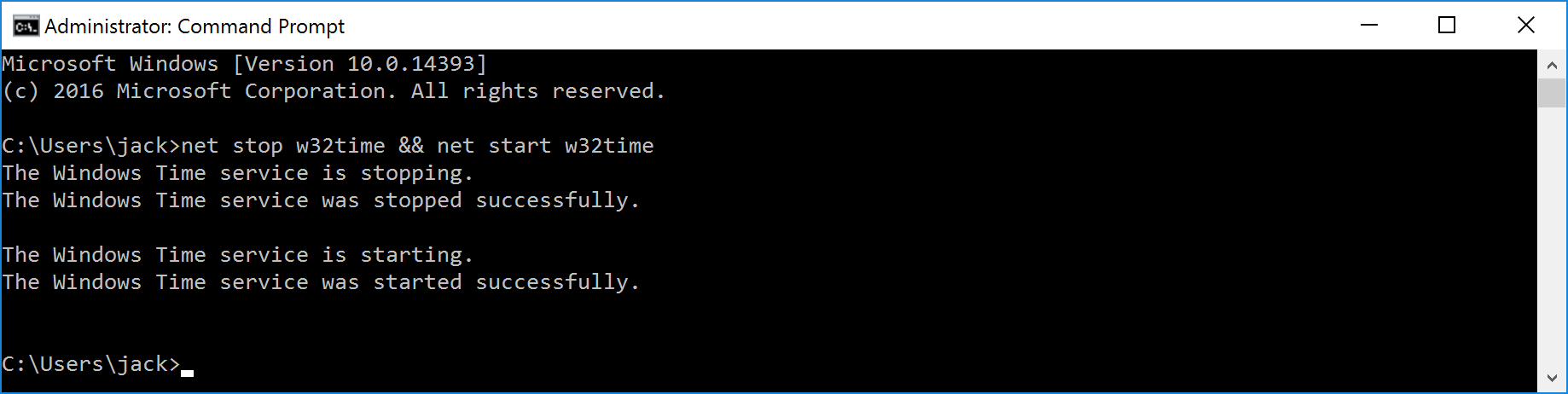
- Restart each of the Azure Virtual Machines or login to each machine and execute the following command to restart the Windows Time service: net stop w32time && net start w32time
- Validate that the Source is now pointing to your NTP server/domain by running the following command: w32tm /query /status