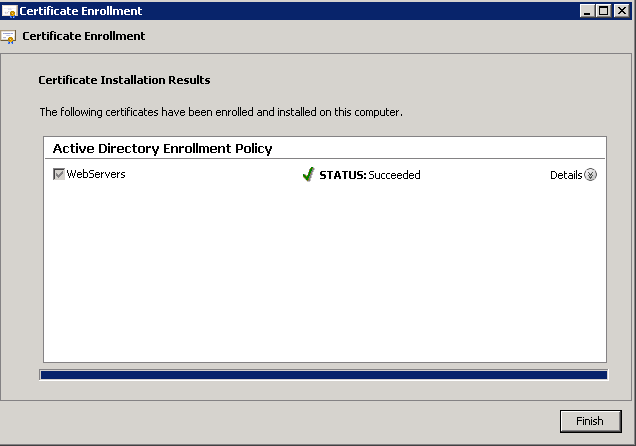
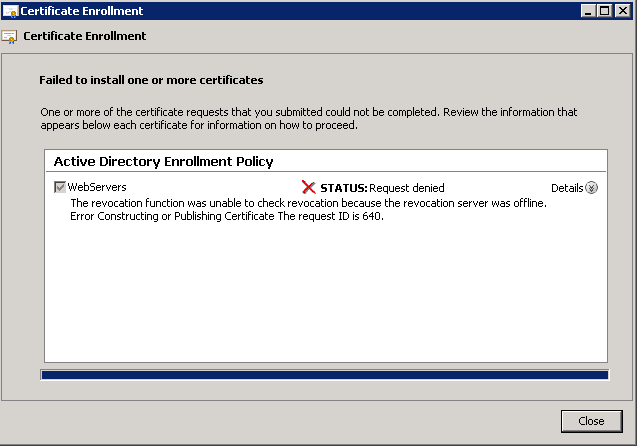
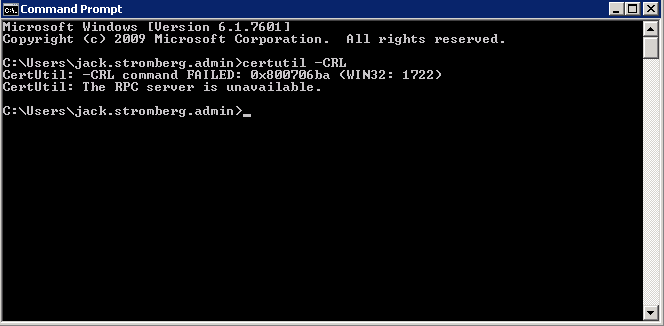
In this article, I have documented the steps I took to update our two domain controllers to Server 2012 R2 from Server 2008 R2. While this can be considered a tutorial, it is more a reflection of what I did during my migration process. This guide assumes you have already made backups of your environment, all Windows Active Directory Domain Controllers in the forest are running Server 2003 or later, and we will be recycling (reusing) the same two servers you deployed. Last, Microsoft strongly recommends we do a clean install and not directly upgrade each server, so we will decommission a DC, reinstall windows, and then redeploy the DC until the entire environment has been upgraded.
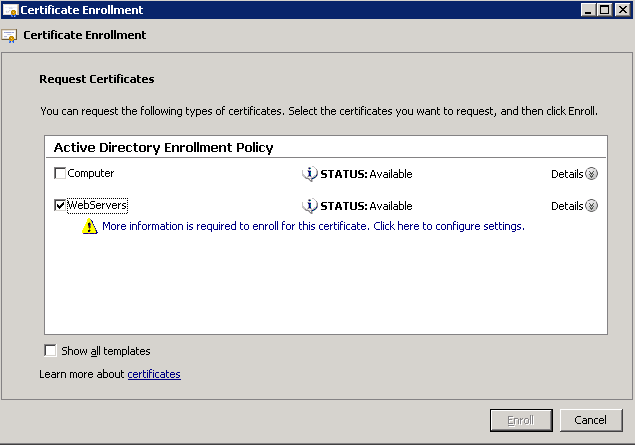
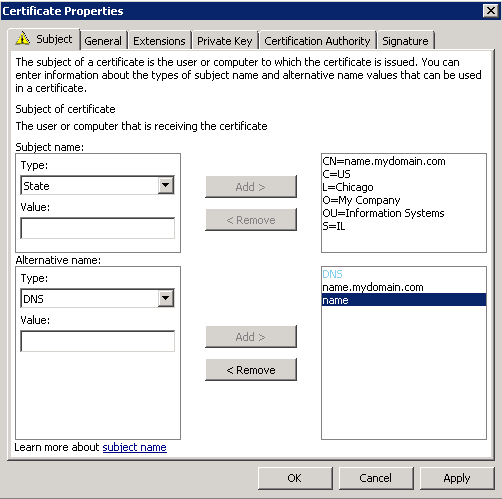
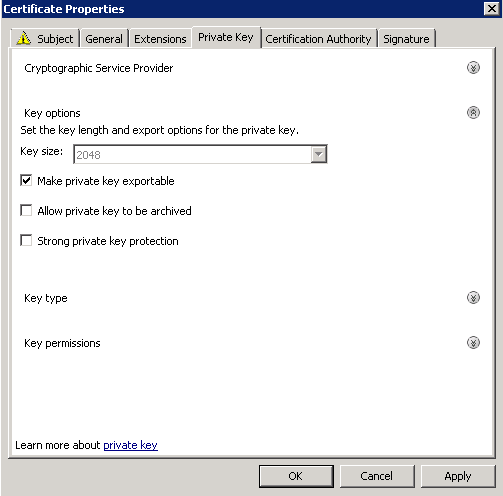
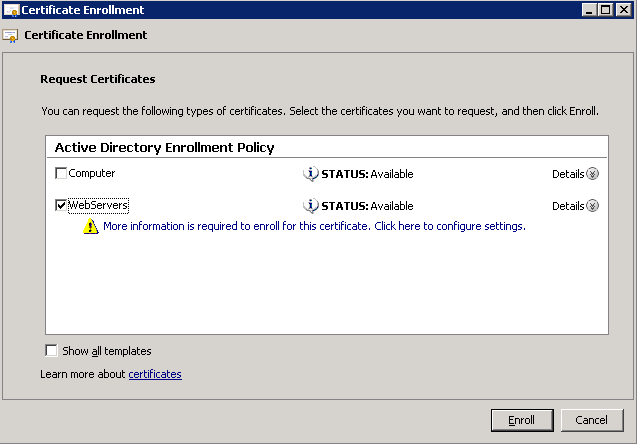
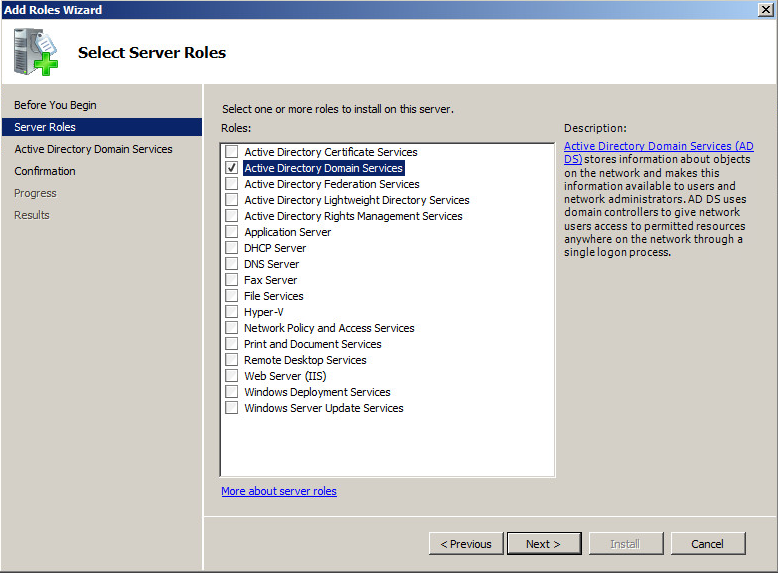
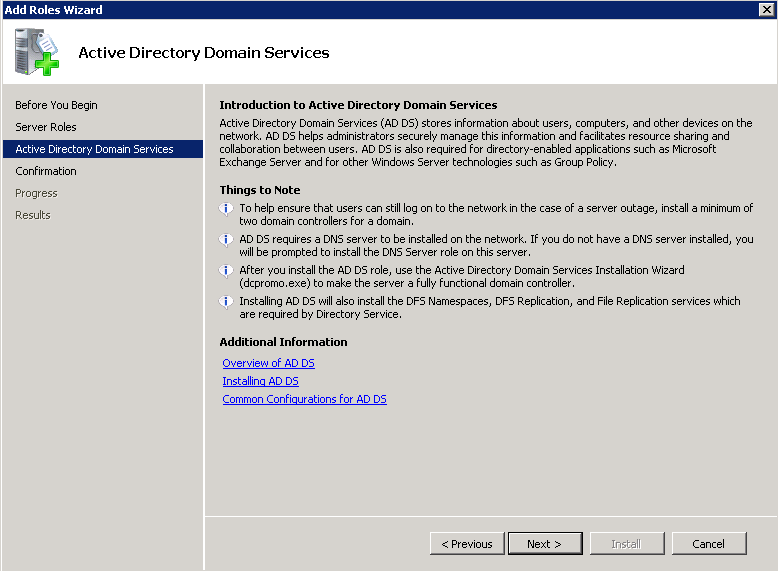
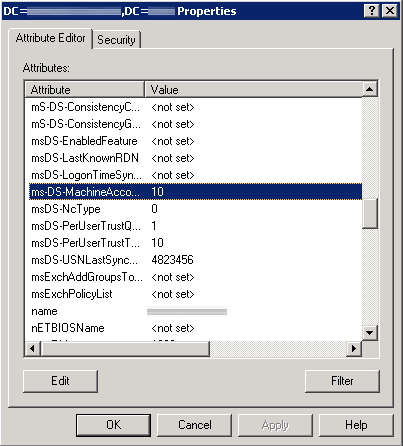
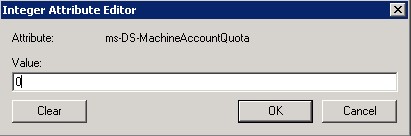
- Prepare the AD Schema for Server 2012 R2
- Mount the Server 2012 R2 installation disk on one of your Domain Controllers
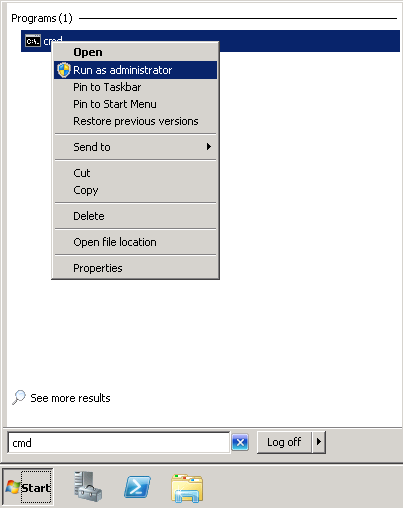
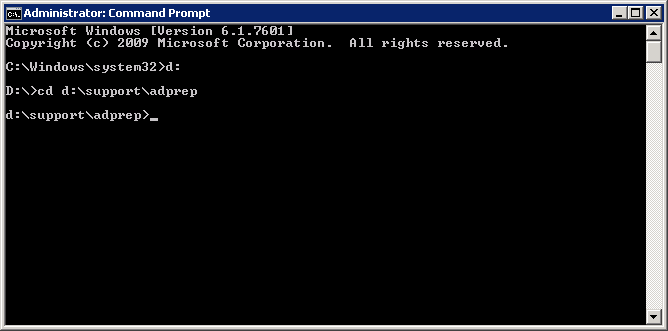
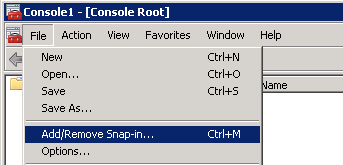
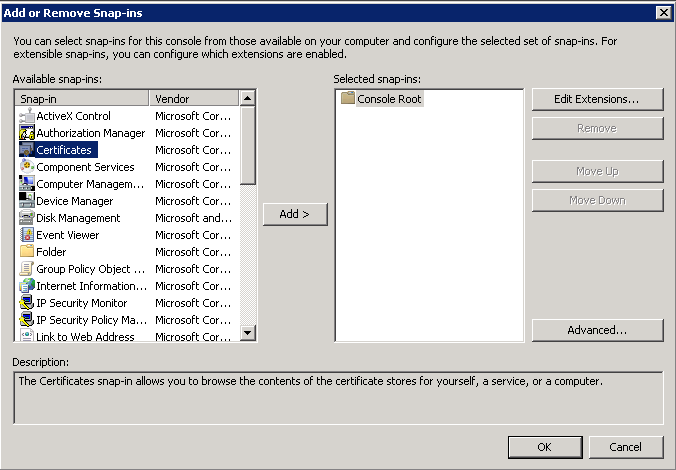
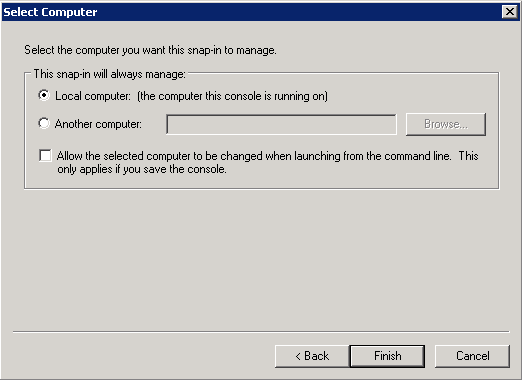
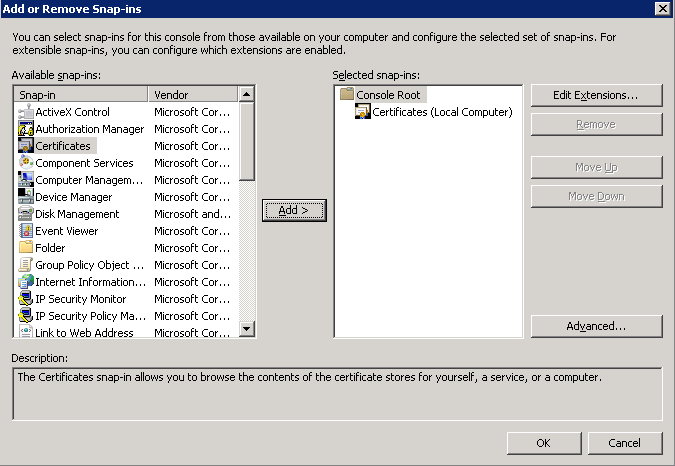
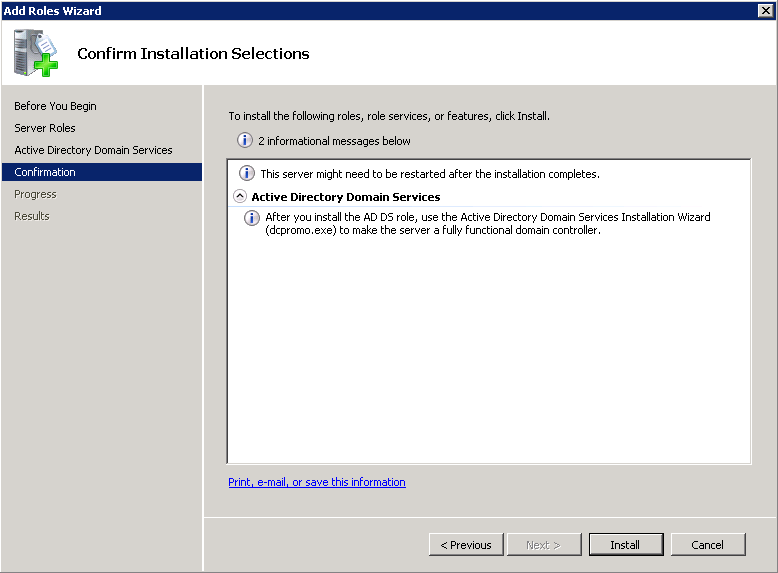
- Open up a command prompt with Administrative Privileges and navigate to the /support/adprep folder on the installation media.
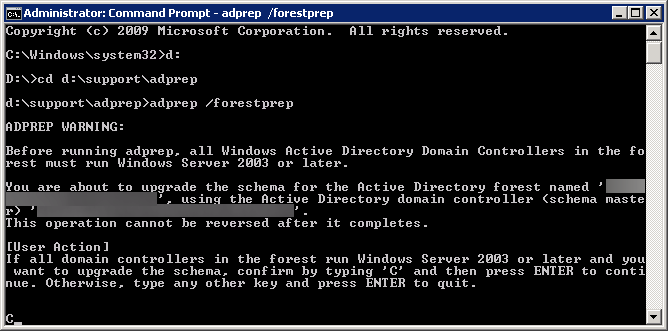
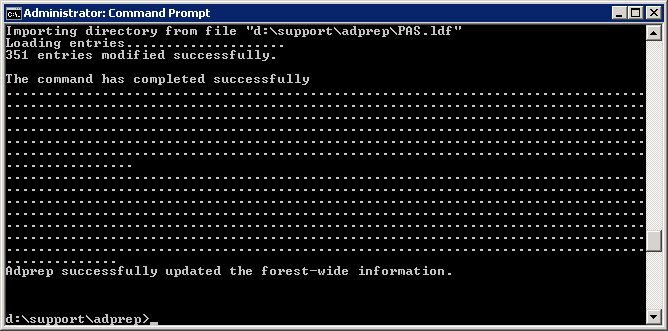
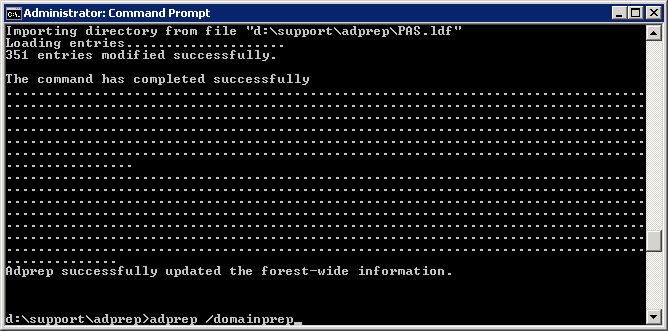
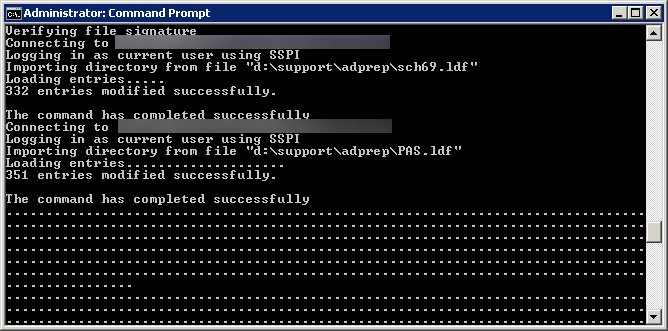
- Execute the following command (don't close out of this until after we verify the schema version in an upcoming step):
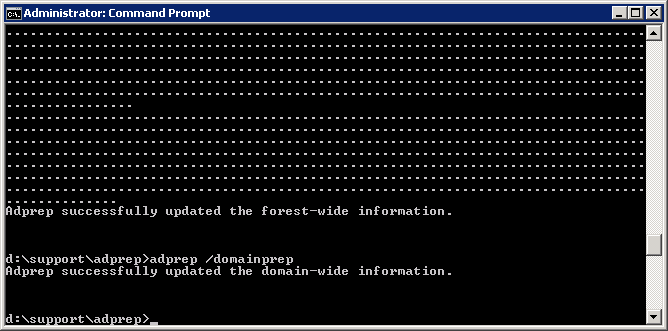
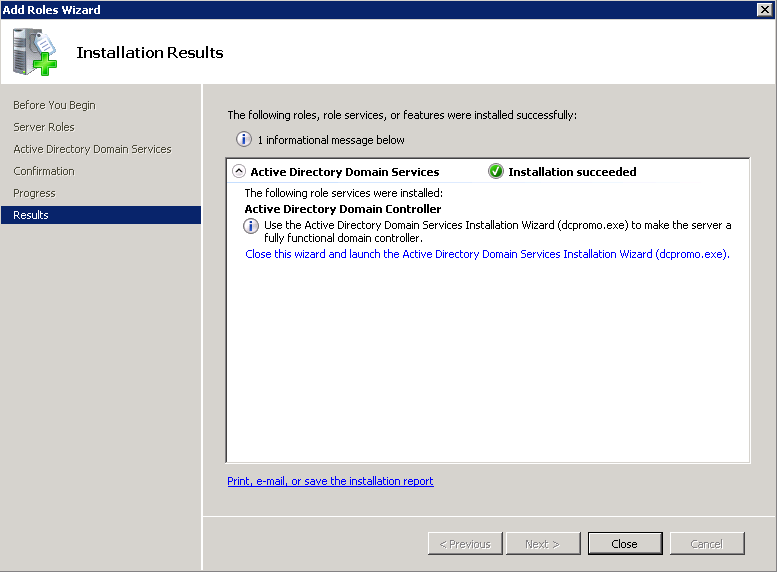
- Execute the following command:
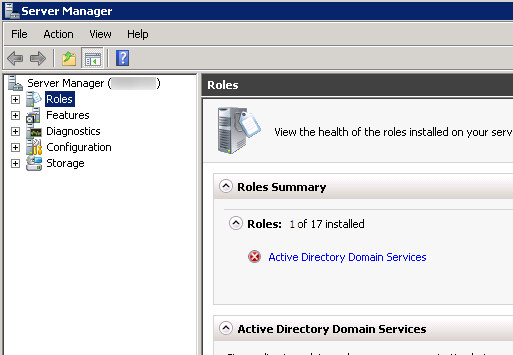
- Verify the schema version has been updated
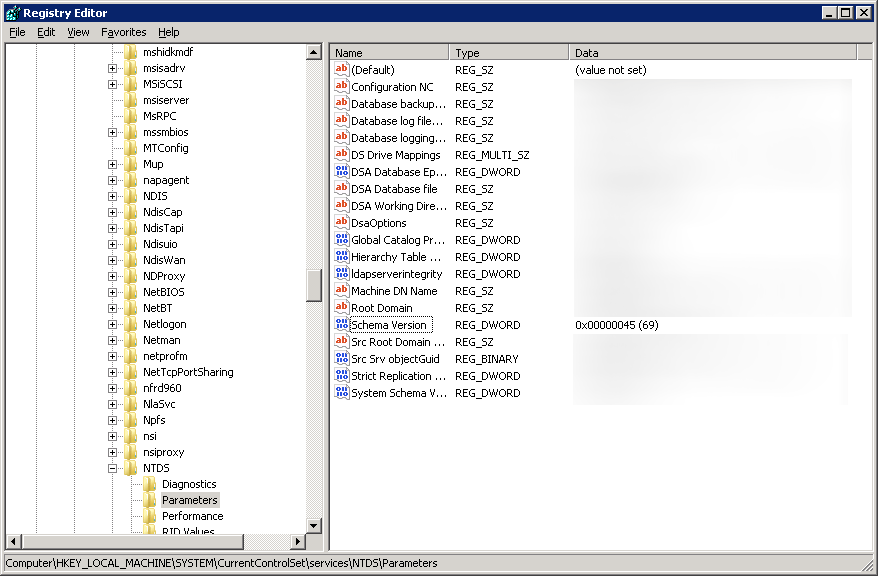
- Open up regedit and navigate to Computer\HKEY_LOCAL_MACHINE\SYSTEM\CurrentControlSet\services\NTDS\Parameters
- Verify the Schema Version value matches the last entry shown in your upgrade results. In my case, the Schema Version should be 69.
- Mount the Server 2012 R2 installation disk on one of your Domain Controllers
- Demote and decommission secondary domain controller
- Click Start, Run...

- Type dcpromo and click OK
- Click Next > on the Welcome page
- If the domain controller has the global catalog service, make sure your primary DC also has the service enabled and click OK. This can be done by opening up Active Directory Sites and Services and viewing the services for each domain controller.

- Make sure the Delete this domain because this server is the last domain controller in the domain is UNCHECKED, and click Next >
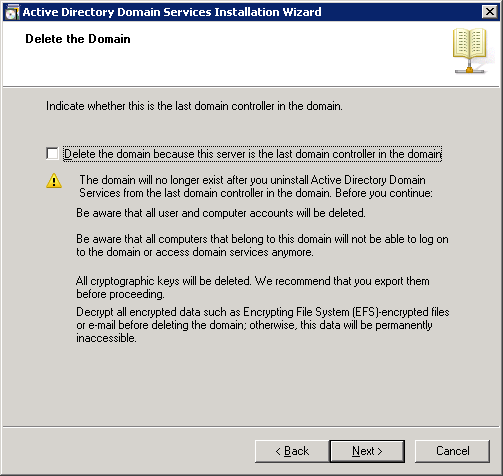
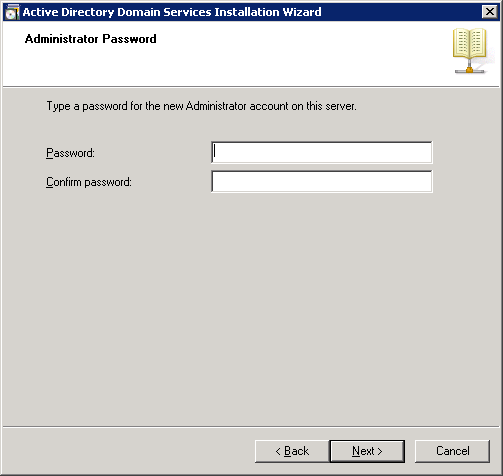
- Type in a new password to be used for the Local Administrator account the machine will contain after it is demoted.
- Click Next > on the Summary page
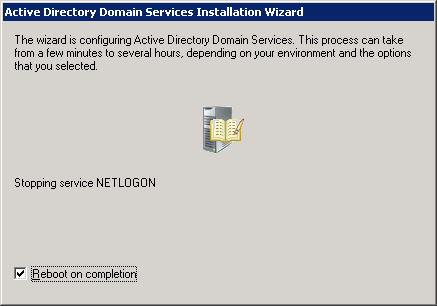
- Check the Reboot on completion box to restart the server after the service has been removed
- Log back into the DC upon reboot and open up Server Manager
- In Roles Summary, click Remove Roles

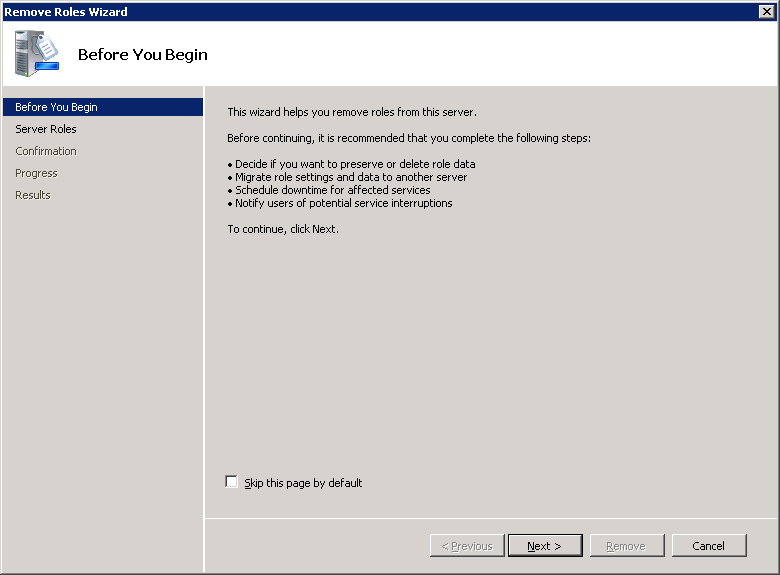
- Click Next > on the Before You Begin page
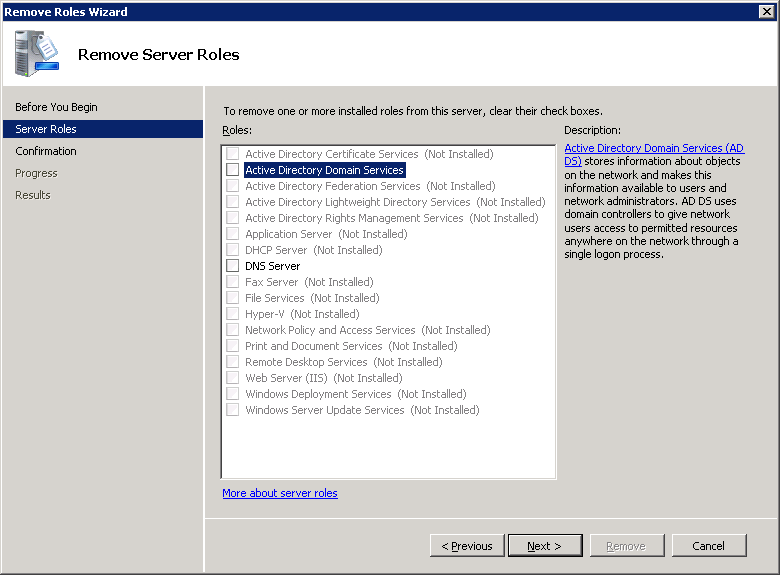
- Uncheck Active Directory Domain Services and DNS Server (if the role is installed) and click Next >
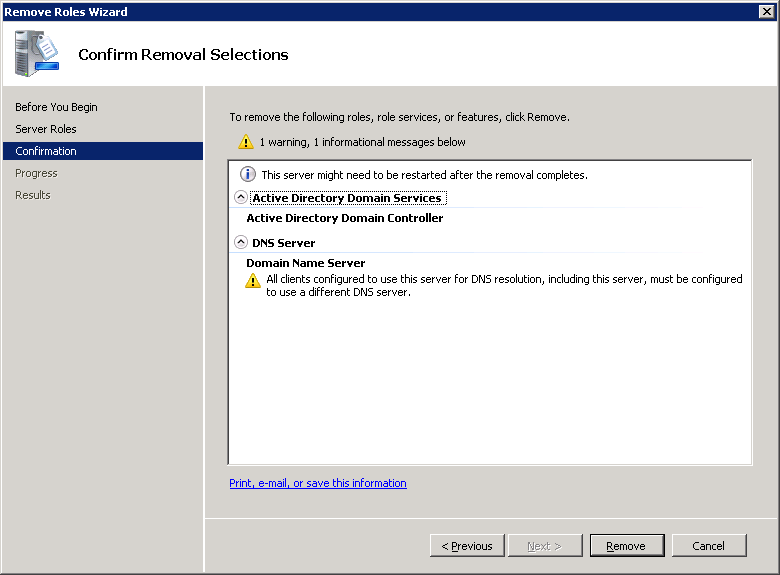
- Click Remove
- Click Close
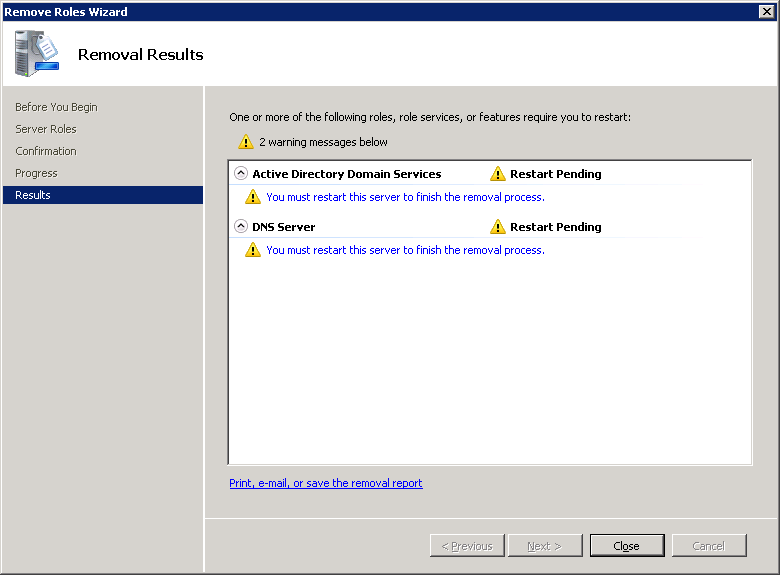
- Select Yes on the Do you want to restart now? dialog box
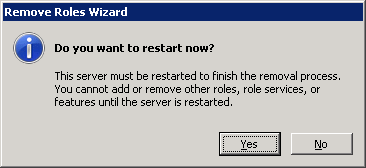
- Log back into the DC upon reboot and you should greeted by a Removal Results window. Let the process finish and select Close upon removal success.
- Disjoin the machine from the domain
- Click Start, right click Computer, select Properties
- Click Change settings
- Click Change... on the System Properties page
- Check Workgroup, type in a workgroup name, and click OK
- Click OK on the warning dialog
- Click OK on the Welcome to the workgroup dialog
- Click OK on the restart dialog
- Click Close on the System Properties window
(oops, forgot to make a screenshot!) - Click Restart Later on the Microsoft Windows dialog box
- Shutdown the machine
- Click Start, right click Computer, select Properties
- Format the decommissioned machine, reinstall a clean copy of Server 2012 R2, and join the machine to the domain.
- Click Start, Run...
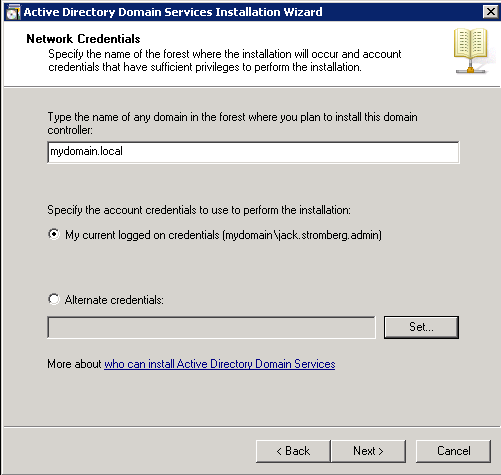
- Add first Server 2012 R2 Domain Controller
- At this point, you should have one Server 2008 R2 Domain Controller and a blank Server 2012 R2 machine joined to the domain ready for the Active Directory services. If you are at this point, continue on, if not, you might want to read back a couple steps and see where things ventured off course.
- Start Server Manager on your new Server 2012 R2 machine.
- Select Manage in the top right and select Add Roles and Features
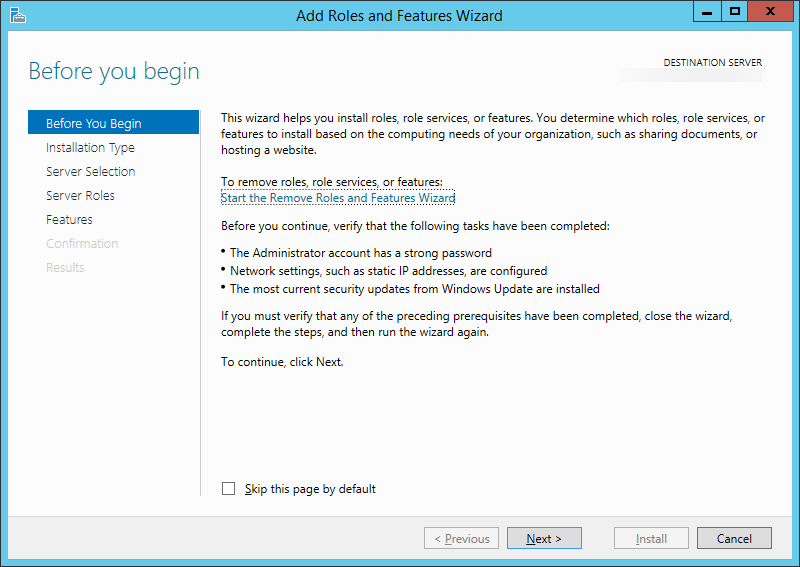
- Click Next > on the Before you begin screen
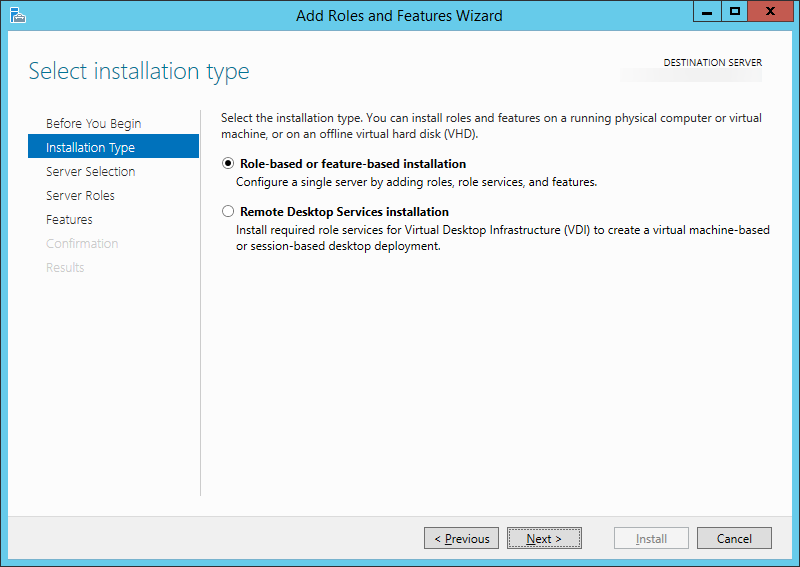
- Click Next > on the Select installation type screen
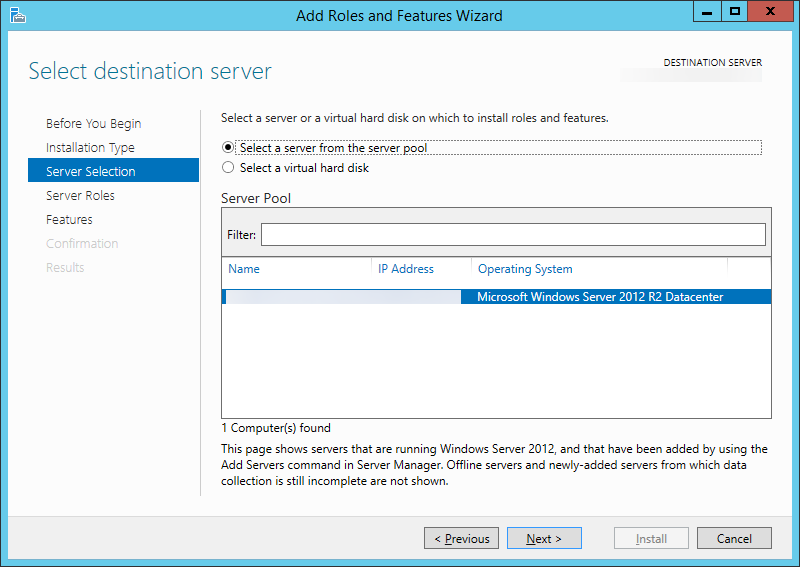
- Ensure your new server is selected and click Next >
- Check the box next to Active Directory Domain Services
- On the Add features that are required for Active Directory Domain Services? dialog, click the Add Features button
- Click Next >
- Click Next >
- Check the box that says Restart the destination server automatically if required
(Click Yes on the restart dialog if it pops up)
- Click the Install button
- Once the install is done, click the Close button
- Next, head back to the Server Manager screen and select the warning icon with the flag; then select Promote this server to a domain controller.
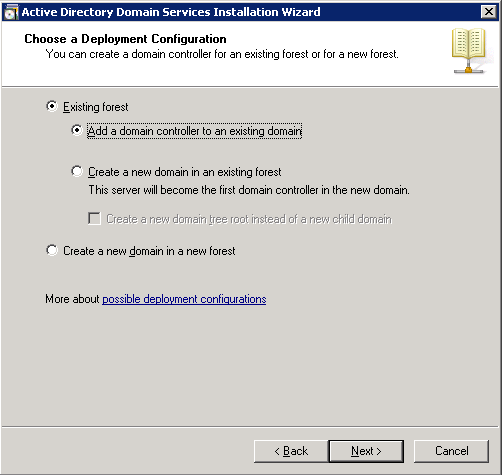
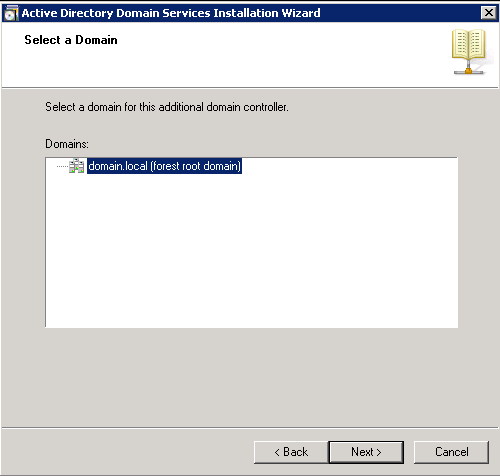
- On the Deployment Configuration page, make sure Add a domain controller to an existing domain is checked and hit Next >
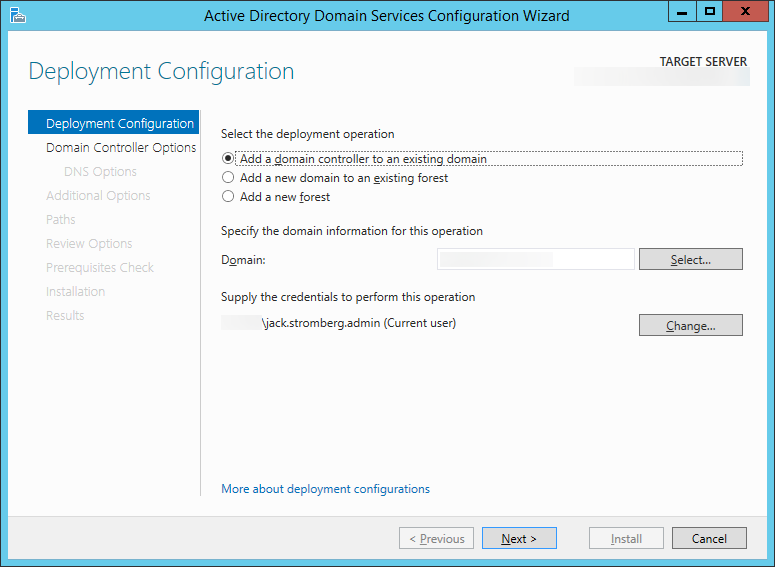
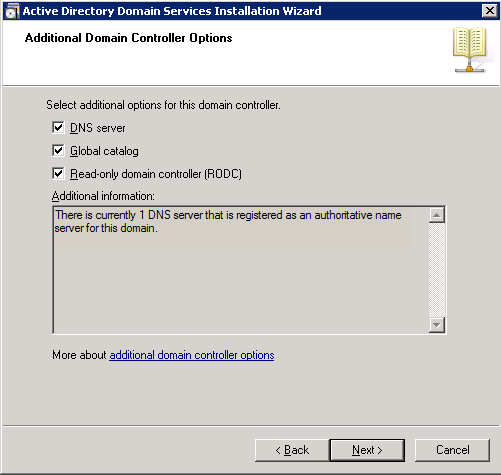
- Check Domain Name System (DNS) server, Check Global Catalog (GC), and uncheck Read only domain controller (RODC). Enter a strong password to be used to access Directory Services Restore Mode and click Next >
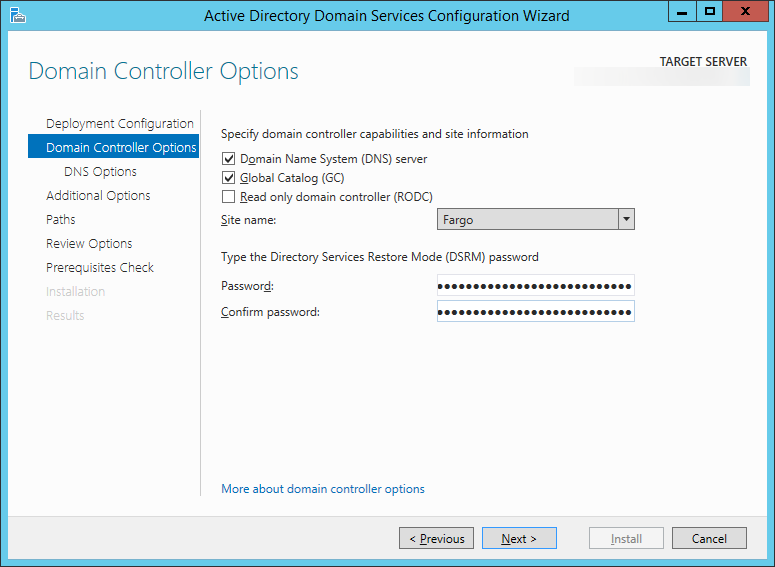
- Click Next > on the DNS Options page
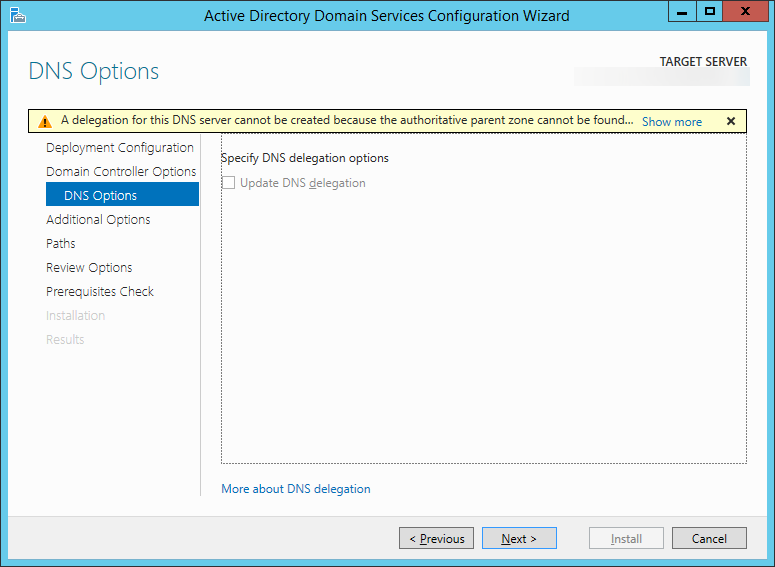
- Click Next > on the Additional Options page, or if you would like, you can manually select a domain controller to replicate data from and then hit Next >.
- Click Next > on the Paths page
- Click Next > on the Review Options page
- Click Install on the Prerequisites Check page
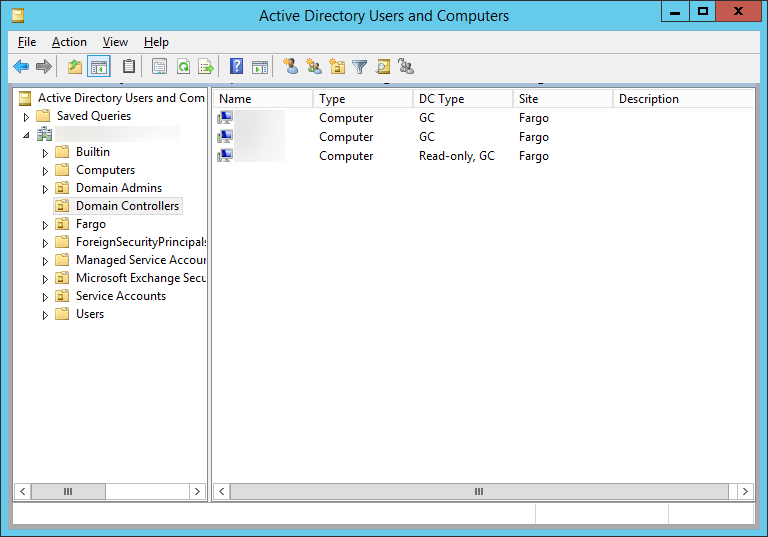
- Once the domain controller reboots after installation, open up Server Manager and select Tools, Active Directory Users and Computers
- Expand your Domain and select Domain Controllers; ensure your new machine shows up here.
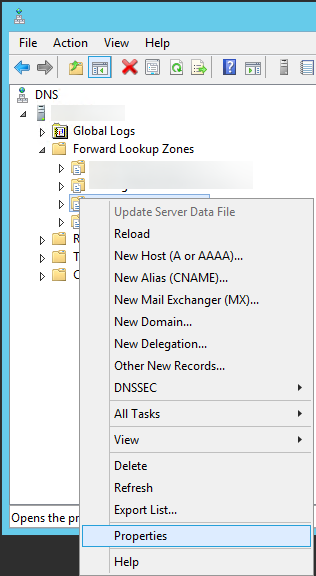
- Next, verify DNS works properly
- Next, we need to verify the FSMO (Flexible Single Master Operations) roles are stored on our other server 2008 DC
- Next, we need to transfer the FSMO roles from our primary DC to our new one
- Execute the following command using the same command prompt in the previous steps: ntdsutil
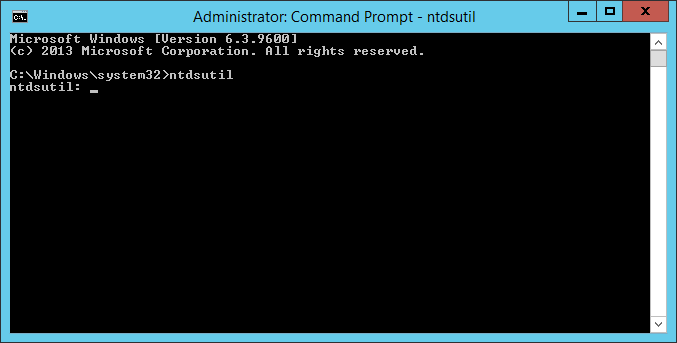
- Type roles when prompted and hit enter
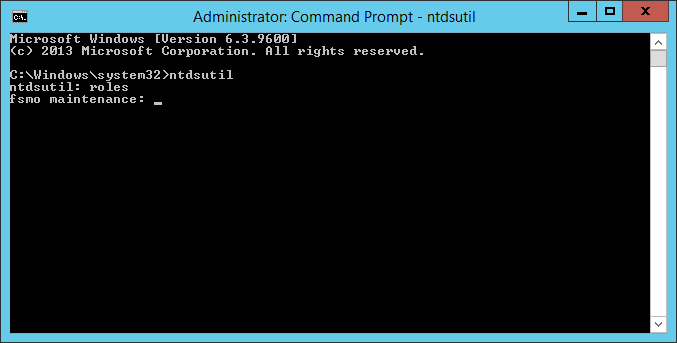
- Type connections when prompted and hit enter
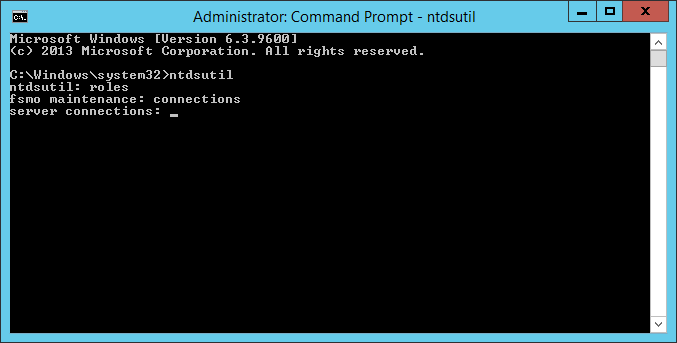
- Type connect to server server2012DC.mydomain.com, where server2012DC is the new DC we just deployed, when prompted and hit enter
- Type quit and hit enter
- Type transfer schema master and hit enter
- Click Yes on the Role Transfer Dialog for the Schema Master role

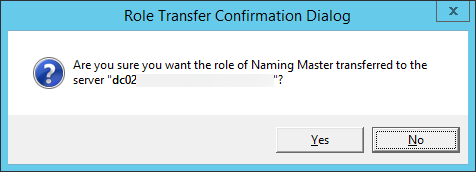
- Type transfer naming master and hit enter
- Click Yes on the Role Transfer Confirmation Dialog for the Naming Master role
- Type transfer PDC and hit enter
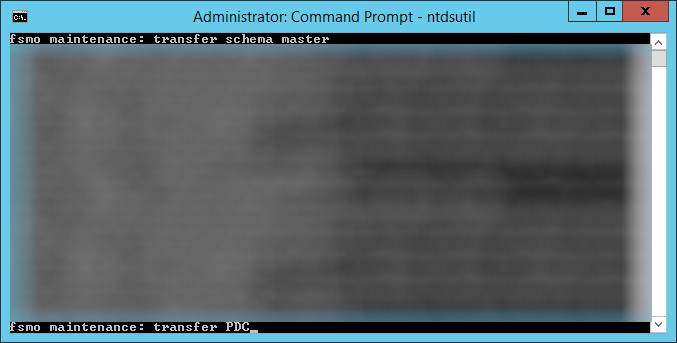
- Click Yes on the Role Transfer Configuration Dialog for the Primary Domain Controller role
- Type transfer RID master and hit enter
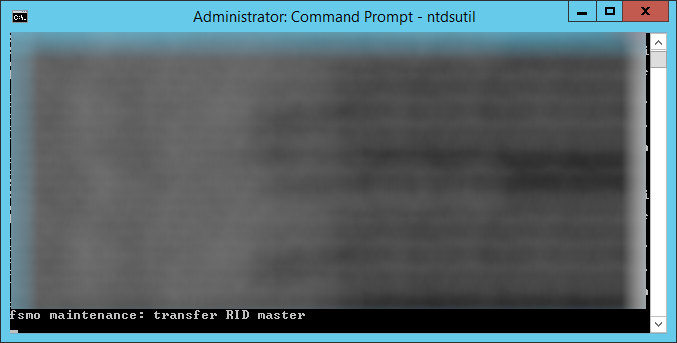
- Click Yes on the Role Transfer Configuration Dialog for the RID master role
- Type transfer infrastructure master and hit enter
- Click Yes on the Role Transfer Configuration Dialog for the Infrastructure Master role

- Type quit and hit enter
- Type quit and hit enter
- Execute the following command to ensure the FSMO services are on the new Server 2012 R2 machine: netdom query fsmo
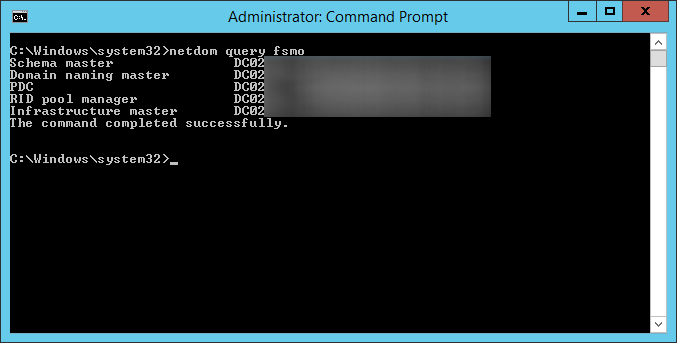
- Execute the following command using the same command prompt in the previous steps: ntdsutil
- At this point, you should have a Server 2012 R2 DC with the FSMO roles and a secondary 2008 R2 Domain Controller. If not, please go back and complete the steps to get to this point.
- Optional Step: After upgrading the first DC, you may want to reconfigure the machine to keep its time in sync with an external source. To do this, please follow my guide here: http://jackstromberg.com/2013/10/configuring-external-time-source-on-your-primary-domain-controller/
- Next, decommission the last Server 2008 R2 domain controller that used to function as the primary DC.
- Follow the same instructions in Step 2 above called Demote and decommission secondary domain controller
- Next, add the machine back to the domain
- Follow the same instructions in Step 3 above called Add first Server 2012 R2 Domain Controller
- At this point, your environment should be up and running with Windows Server 2012 R2! You can optionally transfer the FSMO roles back to your "primary" DC that you had before, or continue on with the roles left on the current DC.
Notes
Official information on removing a domain controller from the domain can be found on Microsoft's website here: http://technet.microsoft.com/en-us/library/cc771844(v=ws.10).aspx