Today I tried upgrading VMware's View Connection and Security servers from 5.1 to 5.2. All went well, but when I browsed out to our security server, I noticed that the web client did not exist.
Solution:
Turns out that VMware View 5.2 itself doesn't contain the HTML5 interface to control your desktop through the browser. In order to enable this feature, you must download the VMware Horizon View Feature Pack on the connection server as well as install the Remote Experience Agent with the HTML Access component on the virtual desktops. All of these can be obtained from the "My VMware" center.
First, I navigated to the VMware Horizon View 5.2 Feature Pack downloads and downloaded the VMware-Horizon-View-HTML-Access_x64-1.0.0-1049726.exe (Click here to go to the VMware download portal). Once downloaded, I installed this on my Connection Servers. This can be installed while the Connection server is running, no downtime neccessary.
Next, I downloaded the Remote Experience Agent for 64-bit desktops (VMware-Horizon-View-5.2-Remote-Experience-Agent-x64-1.0-1046150.msi) file (Same download portal as mentioned above) and installed that on the client machines I wanted to be accessible via the HTML5 page.
Next, I opened up the VMware Horizon View Administrator web GUI and navigated to View Configuration -> Servers -> Connection Servers. Right click on the connection server and ensure the Blast Server URL has been configured properly.
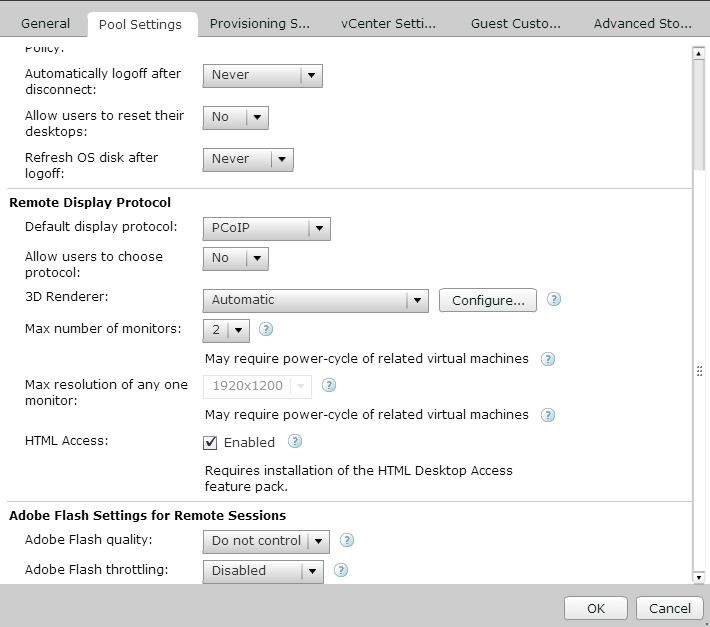
Next, still inside of the VMware Horizon View Administrator web GUI, I navigated to Pools, selected the Pool I wanted to allow HTML5 Web Access to, hit Edit..., selected the Pools Settings tab, and checked HTML Access.
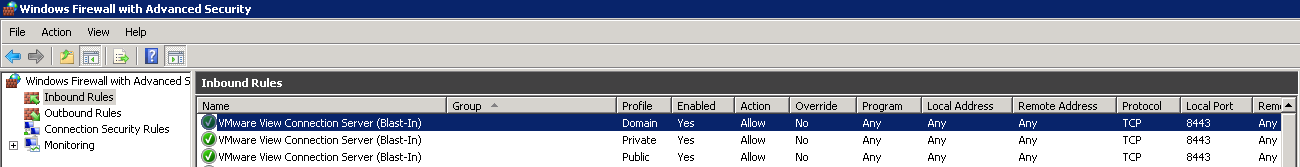
Last, you need to open port 8443 (or whatever External Blast URL port number you used) on your security server (when installing the Security Server, by default the rules are added to Windows Firewall but are not enabled). To do enable the rules, remote to your security server, open up your firewall (in my example, Windows Firewall with Advanced Security), and enable the VMware View Connection Server (Blast-In) rules.
Some errors you may come across
Problem: When you try to login to your desktop via the HTML5 GUI, you receive the following error:
You are not entitled to use the system.
Solution: You need to make sure you entitle the user to the pool or make sure you have checked the HTML Access checkbox for the pool as mentioned above.
-------------------------------------------------------------------------------------------------------------------------
Problem: When connecting to the View Desktop you receive the following error message:
The display protocol for this desktop is currently not available. Please contact your system administrator.
Solution: Make sure the VMware Blast service is running on your virtual desktop/you have installed the Remote Experience Agent as mentioned above.
-------------------------------------------------------------------------------------------------------------------------
Problem: When connecting to the View Desktop you receive the following error message:
All available desktop sources for this desktop are currently busy. Please try connecting to this desktop again later, contact your system administrator.
Solution: Log out of the Web GUI and log back in.
-------------------------------------------------------------------------------------------------------------------------
Problem: When connecting to the View Desktop you receive the following error message:
Unable to connect to desktop: There is no available gateway for the display protocol. Try again, or contact your administrator if this problem persists.
Solution: Log out of the Web GUI and log back in.
-------------------------------------------------------------------------------------------------------------------------
Problem: When connecting to the View Desktop, you are redirected to a page and are given a 404 page cannot be displayed.
Solution: Make sure you have enabled the ports on your external firewall for the Security Servers as well as the firewall on the host running the security server (Windows Firewall as mentioned above).
-------------------------------------------------------------------------------------------------------------------------
Known Issues
Please note, there is a list of published Known Issues by VMware. I would recommend giving the following article a peruse to be familiar with those issues: http://www.vmware.com/support/viewclients/doc/horizon-view-html-access-release-notes.html