I noticed today that a large shipment of Polycom phones we were going to deploy were using the RTM version of Lync Phone Edition and were outdated compared to Microsoft's latest version. That being said, here is a guide on how to update the firmware for your phones.
At the time of this writing, it appears there are only a few different manufacturers that distribute the Microsoft Lync Phone Edition phones. For reference, here are the Microsoft URLs for each of those phone types:
- Microsoft Lync Phone Edition for Aastra 6721ip and Aastra 6725ip
- Microsoft Lync Phone Edition for Polycom CX700 and LG-Nortel IP Phone 8540
- Microsoft Lync Phone Edition for Polycom CX500, Polycom CX600 and Polycom CX3000
- Microsoft Lync Phone Edition for HP 4110 and HP 4120
Deploying latest firmware for the Microsoft Lync Phone Edition
- Download the latest firmware for the Lync Phone Edition device.
- In my case, I want to push out the latest firmware for the Polycom CX600s, which can be found here (links to the firmware of other phones can be found above in this same article): http://www.microsoft.com/en-us/download/details.aspx?id=23866
- Double click on the downloaded file (UCUpdates.exe), and run through the wizard.
- Select your language:
- Accept the EULA
- On this step, extract the files to a folder you can recognize. All firmware downloads are called UCUpdates.exe and ucupdates.cab, so I highly recommend you sort out each firmware to a corresponding folder.
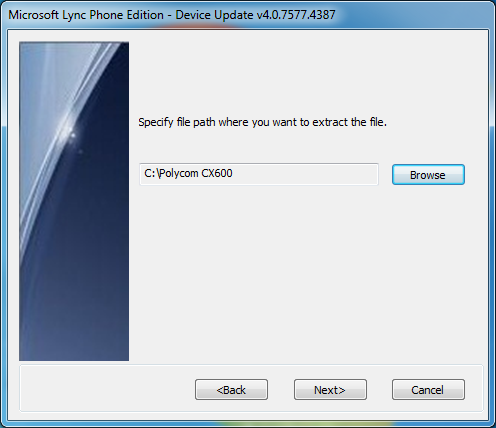
- Click the "Click this link to open folder in Windows Explorer." and verify you see the ucupdates.cab file.
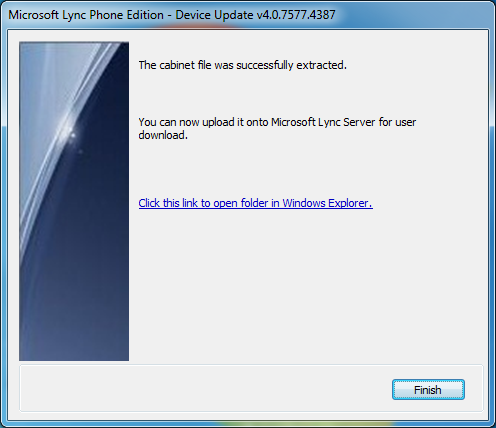
- Here we see the ucupdates.cab file.
- Select your language:
- Copy the ucupdates.cab file over to your Lync Front End Server if you didn't in the first step.
- Execute the following powershell command (where the WebServer is the Front End Pool or Front End Server in a standalone instance):
- Import-CsDeviceUpdate -Identity service:WebServer:lync.mydomain.local -FileName "C:\Polycom CX600\ucupdates.cab" -Verbose
- Note: I added the optional -Verbose parameter to show the output of what the PowerShell command is doing behind the scenes. Some people have mentioned this step taking awhile to complete, this will at least give you some comfort if things are moving forward or not.
- Import-CsDeviceUpdate -Identity service:WebServer:lync.mydomain.local -FileName "C:\Polycom CX600\ucupdates.cab" -Verbose
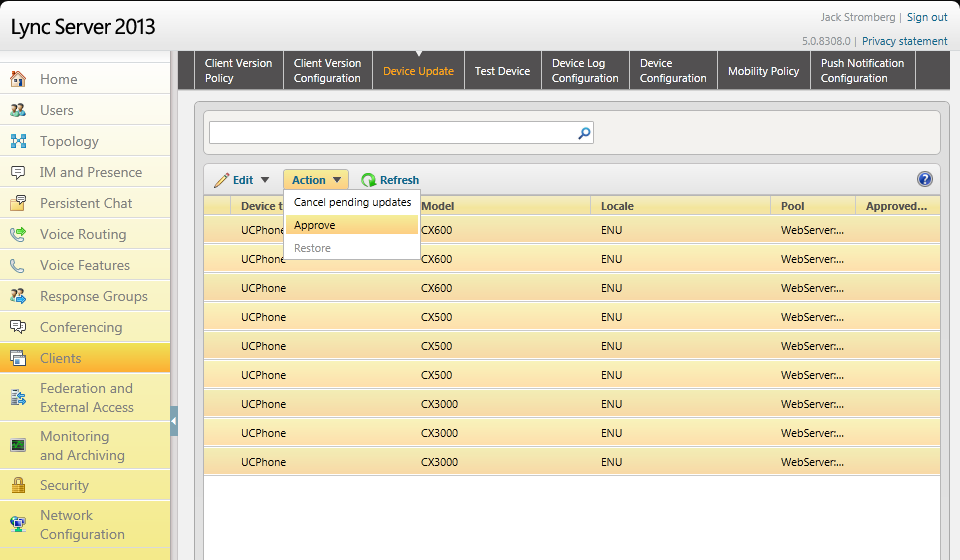
- Once the command has completed successfully, head over to the Lync Server Control Panel (LSCP) (Web GUI), and navigate to Clients > Device Update. Here you should see the firmware for your device and you should notice that the version shows up under the "Pending Version" column. This means that the firmware will NOT be pushed until we manually approve it.
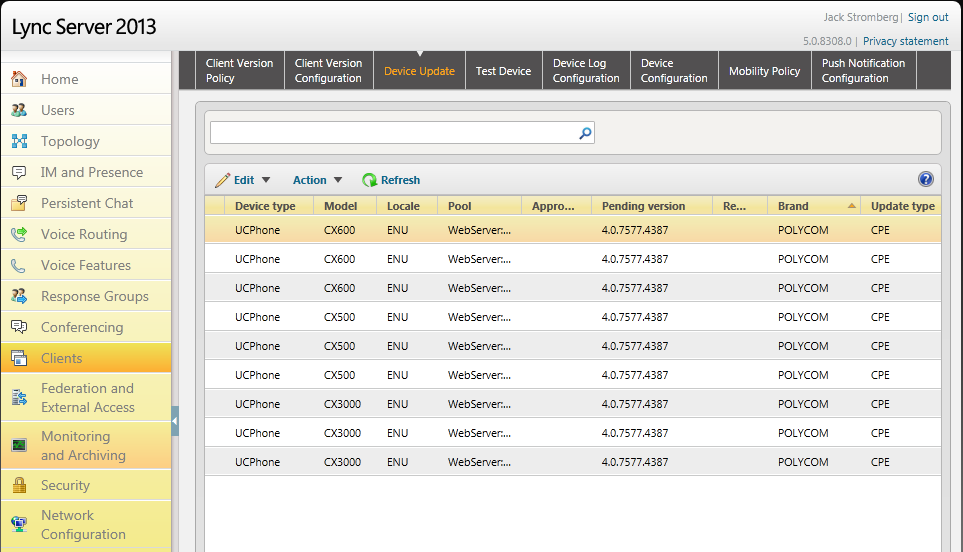
- Now we will push out the firmware to one device to ensure the firmware actually works. Inside of the Lync Server Control Panel, click on the Test Device tab.
- Click the New... button and then select Global test device
- For Device Name, type in something like Polycom CX600 to identify what will be pushed to it, and then enter in the MAC address of the phone in the Unique identifier field.
- Note: if you use the MAC address as the Unique identifier, make sure you leave out any special characters, it should be only the hex address.
- Here is a screenshot below of my test device:
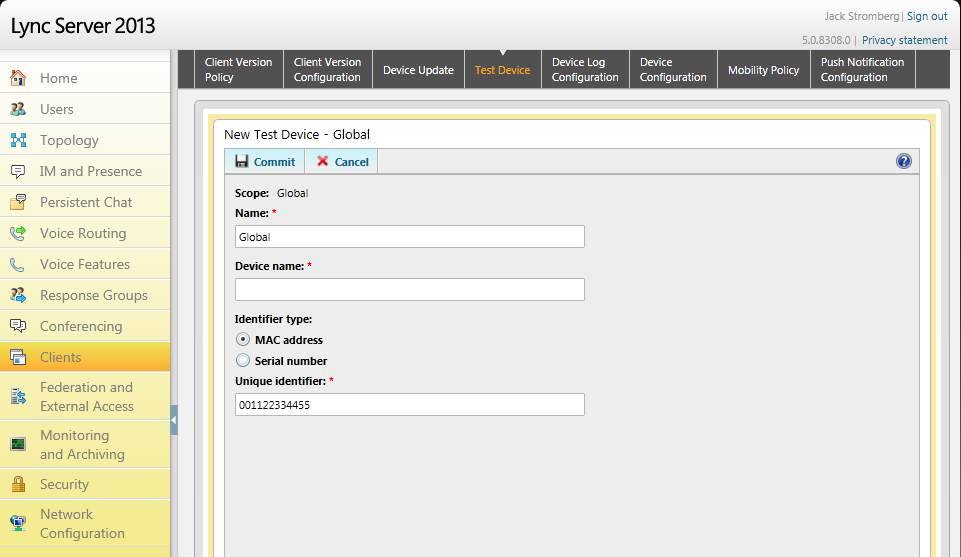
- At this point, all you need to do is wait until the phone reboots and applies the update automatically (you don't need to approve the firmware or anything like that, it just starts to deploy to the test device).
- If you want to check what is going on, if you login to your front end server and navigate to C:\inetpub\logs\LogFiles\<randomID>, you can see the process of the phone trying to pull the update files and then reconnecting with the updates. In my case, I could see the phone boot, pull the new firmware files, and then reboot and make new requests with the latest version in the headers.
- 2013-05-16 15:43:13 192.168.1.21 POST /locationinformation/liservice.svc/mex - 443 - 192.168.2.2 OCPhone/4.0.7577.4066+(Microsoft+Lync+2010+Phone+Edition) - 200 0 0 114
2013-05-16 15:43:13 192.168.1.21 POST /RequestHandler/ucdevice.upx - 443 - 192.168.2.2 Microsoft+UCPhone+Device+(lcs_se_w14_main:1077577:2012/02/18:16:44:15) - 200 0 0 219
2013-05-16 15:43:13 192.168.1.21 GET /RequestHandler/Files/UCPhone/POLYCOM/CX600/Rev-5/ENU/4.0.7577.4387/CPE/CPE.nbt - 80 - 192.168.2.2 Microsoft+UCPhone+Device+(lcs_se_w14_main:1077577:2012/02/18:16:44:15) - 200 0 995 240
2013-05-16 15:43:13 192.168.1.21 POST /groupexpansion/service.svc/mex - 443 - 192.168.2.2 OCPhone/4.0.7577.4066+(Microsoft+Lync+2010+Phone+Edition) - 200 0 0 30
2013-05-16 15:43:15 192.168.1.21 POST /WebTicket/WebTicketService.svc/mex - 443 - 192.168.2.2 OCPhone/4.0.7577.4066+(Microsoft+Lync+2010+Phone+Edition) - 200 0 0 129
2013-05-16 15:43:17 192.168.1.21 POST /WebTicket/WebTicketService.svc/cert - 443 - 192.168.2.2 OCPhone/4.0.7577.4066+(Microsoft+Lync+2010+Phone+Edition) - 200 0 0 68
2013-05-16 15:43:17 192.168.1.21 POST /locationinformation/liservice.svc/WebTicket_Bearer - 443 - 192.168.2.2 OCPhone/4.0.7577.4066+(Microsoft+Lync+2010+Phone+Edition) - 200 0 0 197
..........Some random logs here..........
2013-05-16 15:44:16 192.168.1.21 GET /RequestHandler/Files/UCPhone/POLYCOM/CX600/Rev-5/ENU/4.0.7577.4387/CPE/CPE.nbt - 80 - 192.168.2.2 Microsoft+UCPhone+Device+(lcs_se_w14_main:1077577:2012/02/18:16:44:15) - 200 0 0 61951
2013-05-16 15:44:16 192.168.1.21 GET /RequestHandler/Files/UCPhone/POLYCOM/CX600/Rev-5/ENU/4.0.7577.4387/CPE/CPE.cat - 80 - 192.168.2.2 Microsoft+UCPhone+Device+(lcs_se_w14_main:1077577:2012/02/18:16:44:15) - 200 0 0 44
2013-05-16 15:44:16 192.168.1.21 GET /RequestHandler/Files/UCPhone/POLYCOM/CX600/Rev-5/ENU/4.0.7577.4387/CPE/CPE.cat - 80 - 192.168.2.2 Microsoft+UCPhone+Device+(lcs_se_w14_main:1077577:2012/02/18:16:44:15) - 200 0 0 10
..........Some random logs here..........
2013-05-16 15:51:55 192.168.1.21 POST /groupexpansion/service.svc/mex - 443 - 192.168.2.2 OCPhone/4.0.7577.4387+(Microsoft+Lync+Phone+Edition) - 200 0 0 11
2013-05-16 15:51:55 192.168.1.21 POST /locationinformation/liservice.svc/mex - 443 - 192.168.2.2 OCPhone/4.0.7577.4387+(Microsoft+Lync+Phone+Edition) - 200 0 0 8
2013-05-16 15:51:56 192.168.1.21 POST /WebTicket/WebTicketService.svc/mex - 443 - 192.168.2.2 OCPhone/4.0.7577.4387+(Microsoft+Lync+Phone+Edition) - 200 0 0 10
- Once the firmware has been applied to your test device and all is well, we need to approve the firmware for all phones in the organization. To do so, follow the steps below.