This guide will go over configuring phones for Lync 2010/2013. Particularly, this is going to go over configuring phones for conference rooms or any other public area that you would like a phone, but the same steps can be used to force users to login/authenticate to a phone with their number/extension and pin. That being said, purchasing some Polycom CX3000 phones prompted me to write this guide, so if all goes well, your Polycom phones should work like a charm (Aastra phones should follow this guide as well) 😛
Making sure DHCP and DNS can dish out configurations to phones
The first thing to do is make sure you have your DHCP server setup to get your phones working (we will push settings out to the clients/phones so they can find your Lync server, pull down certificates, etc). In order to do this, you will have to complete the following tasks on your DHCP, DNS, and Lync Front End servers.
- Create a DNS record to point to your NTP servers (if you haven't already)
-
- Service: _ntp
- Protocol: _udp
- Port Number: 123
- Host: xxx.xxx.xxx (your time server (probably your DC))
- Copy the DHCPUtil.exe and DHCPConfigScript.bat from the paths below to the Desktop on your DHCP Server
- %ProgramFiles%\Common Files\Microsoft Lync Server 2010 or
- %ProgramFiles%\Common Files\Microsoft Lync Server 2013
- Open up a command prompt as Administrator on your DHCP server
- Execute the following commands on your DHCP Server
- DHCPUtil.exe -SipServer mylyncpoolorserver.mydomain.local –RunConfigScript
- If you receive the following
- The program can't start because MSVCR110.dll is missing from your computer. Try reinstalling the program to fix this problem.
- You can find MSVCR110.dll in the Lync 2013 media (D:\Setup\amd64 for example)
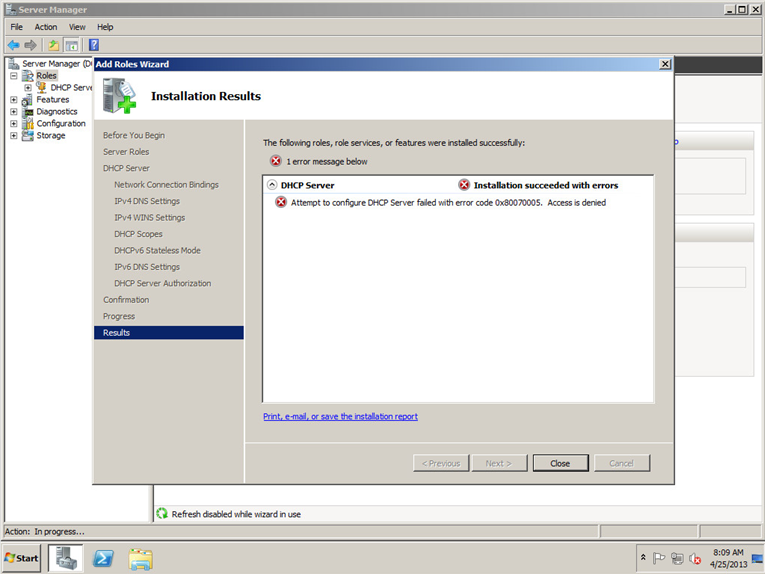
- To see if everything ran smoothly, open up the DHCP role and verify the entries were made in the IPv4 section
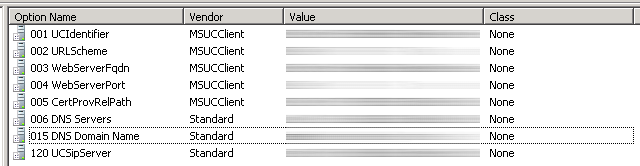
- Execute the following from your Lync Server to verify the DHCP settings are correct (Note, if you run this from your DHCP server, it will always come back with a failed result).
- DHCPUtil.exe -EmulateClient
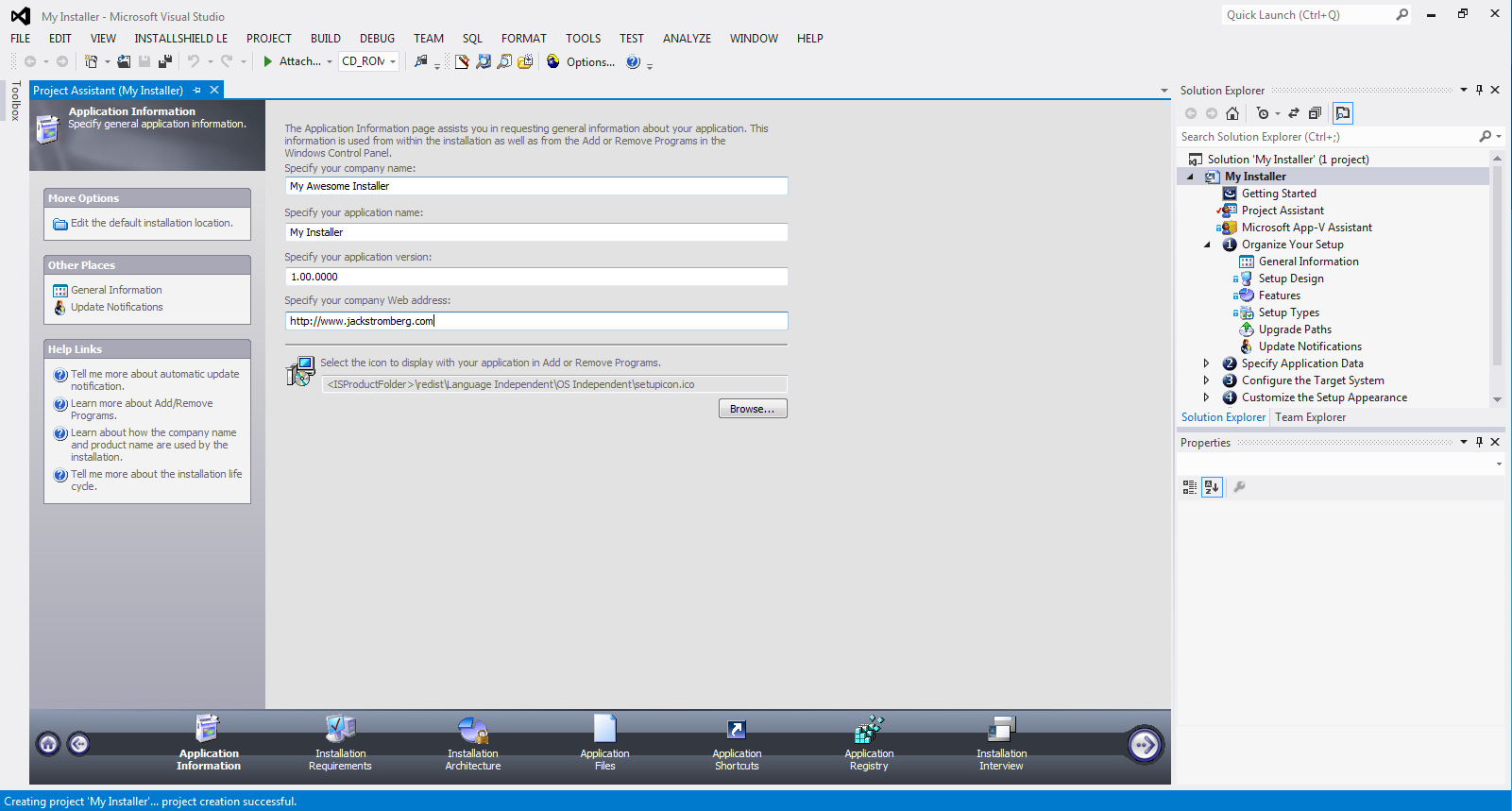
- Next, you will need to set a PIN policy for any users who will want to login. Open the Lync Control Panel and click on Security. Select the PIN Policy tab and double click on the Global policy. Change the PIN Length to at least 4 you want. Now click on Commit.
Creating the Common Area Phones Lync Policies
First, create a policy that will Enable Hotdesking. This will log out a user that may have signed in to the phone and revert the phone back to a Common Area phone after 10 minutes of timeout.
New-CsClientPolicy -Identity CommonAreaClient -EnableHotdesking $True -HotdeskingTimeout 00:10:00
Next, we create a new voice policy to lockdown what the phone can do. This will prevent users from setting the phone to do call forwarding, delegation, call transfer, etc. Alternatively, if you don't want to run the PowerShell command, you can browse use the Lync Server Control Panel web GUI to create a new Voice Policy. Go to the Lync Control Panel, click on Voice Routing, and then the Voice Policy tab. The command below will add the Internal policy, you can add others if you desire.
New-CsVoicePolicy -Identity CommonAreaVoice -PstnUsages @{add="Internal"} -AllowSimulRing $FALSE -AllowCallForwarding $FALSE -Name CommonAreaVoice -EnableDelegation $FALSE -EnableTeamCall $FALSE -EnableCallTransfer $FALSE -AllowPSTNReRouting $FALSE -Description "Feature-Restricted Common Area Phone Policy"
Next, we create a policy to restrict what the Common Area phone can do in conferences. Execute the following command to create a new Conferencing Policy. Alternatively, we could create this using the Lync Server Control Panel web GUI by clicking on Conferencing and then selecting the Conferencing Policy tab.
New-CsConferencingPolicy -Identity CommonAreaConf -AllowIPAudio $FALSE -AllowIPVideo $FALSE -EnableFileTransfer $FALSE -EnableP2PFileTransfer $FALSE -EnableDataCollaboration $FALSE
Last, we need to create a PIN policy for these guys to login. I suppose you could use the global one for this step, but we could set this rule to be stricter for just these phones. This will require all CommonArea phones to use a 4 digit pin to login.
New-CsPINPolicy -Identity CommonAreaPIN -Description "Common Area Phone
Authentication PIN Policy" -MinPasswordLength 6 -AllowCommonPatterns $TRUE
Creating the Common Area Phones With Our policies
Next, create the commonarea phone:
New-CsCommonAreaPhone -LineUri "tel:+15555555555" -RegistrarPool "lync.mydomain.local" -OU "OU=CommonAreaPhones,DC=mydomain,DC=local" -Description "Batline 1" -DisplayName "Conference Room Batline" -DisplayNumber "1 (555) 555-5555"
Next, we need to set the new account we created with a PIN policy. To do so, execute the following command (keeping in mind you need this to be at least 4 digits or longer depending on your policy you created earlier).
Set-CsClientPin –Identity “Batline 1” -Pin 123123
Lastly, we need to assign all of the polices we created earlier to this Common Area Phone account. To do so, execute the following commands:
Grant-CsClientPolicy -PolicyName CommonAreaClient -Identity "Batline 1”
Grant-CsConferencingPolicy -PolicyName CommonAreaConf -Identity "Batline 1”
Grant-CsPINPolicy -PolicyName CommonAreaPIN -Identity "Batline 1”
Grant-CsVoicePolicy -PolicyName CommonAreaVoice -Identity "Batline 1”
Last, you can execute the following powershell command on your Lync Front End server to try and emulate logging in to the phone. This is great for debugging where the Lync Phone login would fail:
Test-CsPhoneBootstrap -PhoneOrExt 5555 -Pin 12345 -Verbose
Notes: If you have a polycom phone and you receive the following error "Certificate web service cannot be found. Please contact your support team." -- You need to configure the DHCP options as noted above in the "Making sure DHCP and DNS can dish out configurations to phones" section.
When executing the New-CsCommonAreaPhone command above, you receive the following powershell error "New-CsCommonAreaPhone : Management object not found for identity." I saw this error being an issue with your distinguishedName attribute. Make sure you spelled your OU correctly, and that you are not using an OU that is built into AD like Users.
Good resources that explain exactly what is going on in greater detail.
http://blog.schertz.name/2010/12/configuring-lync-server-for-phone-edition-devices/
http://blog.schertz.name/2011/04/common-area-phone-configuration-in-lync/
http://www.graham-walsh.com/blog/?p=593