So strangely enough, I always thought submitting a 2048bit CSR to my CA and receiving a 256-bit SSL cert would automatically force connections to use a 256-bit cipher strength over the established SSL connection, however it turns out that most connections will stay at 128-bit unless you tell your server to utilize TLS 1.2. In this tutorial, we will go over how to enable TLS v1.2 for IIS to increase the cipher strength to 256-bits.
Here is what a certificate's connection info looked like before the tutorial
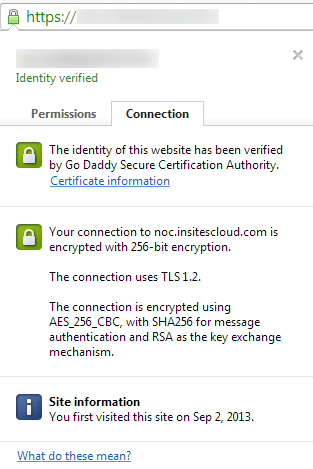
Here is what a certificate's connection info looks like after the tutorial
- Execute the following commands via an elevated PowerShell command prompt to enable TLS v1.2:
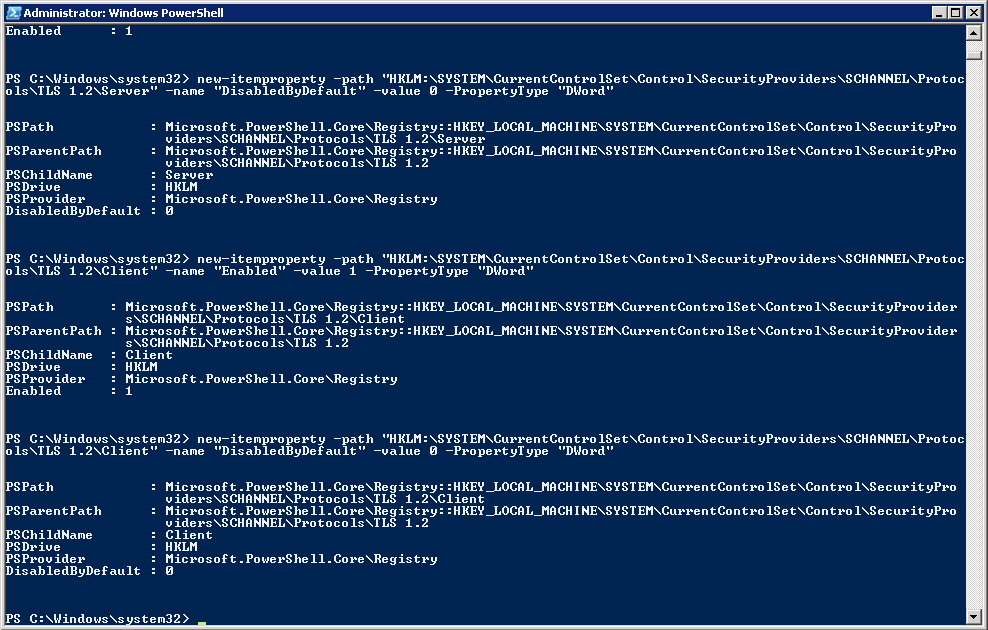
# Create keys in registry (not created by Windows out of the box)
md "HKLM:\SYSTEM\CurrentControlSet\Control\SecurityProviders\SCHANNEL\Protocols\TLS 1.2"
md "HKLM:\SYSTEM\CurrentControlSet\Control\SecurityProviders\SCHANNEL\Protocols\TLS 1.2\Server"
md "HKLM:\SYSTEM\CurrentControlSet\Control\SecurityProviders\SCHANNEL\Protocols\TLS 1.2\Client"
# Enable TLS 1.2 for client and server SCHANNEL communications
new-itemproperty -path "HKLM:\SYSTEM\CurrentControlSet\Control\SecurityProviders\SCHANNEL\Protocols\TLS 1.2\Server" -name "Enabled" -value 1 -PropertyType "DWord"
new-itemproperty -path "HKLM:\SYSTEM\CurrentControlSet\Control\SecurityProviders\SCHANNEL\Protocols\TLS 1.2\Server" -name "DisabledByDefault" -value 0 -PropertyType "DWord"
new-itemproperty -path "HKLM:\SYSTEM\CurrentControlSet\Control\SecurityProviders\SCHANNEL\Protocols\TLS 1.2\Client" -name "Enabled" -value 1 -PropertyType "DWord"
new-itemproperty -path "HKLM:\SYSTEM\CurrentControlSet\Control\SecurityProviders\SCHANNEL\Protocols\TLS 1.2\Client" -name "DisabledByDefault" -value 0 -PropertyType "DWord"
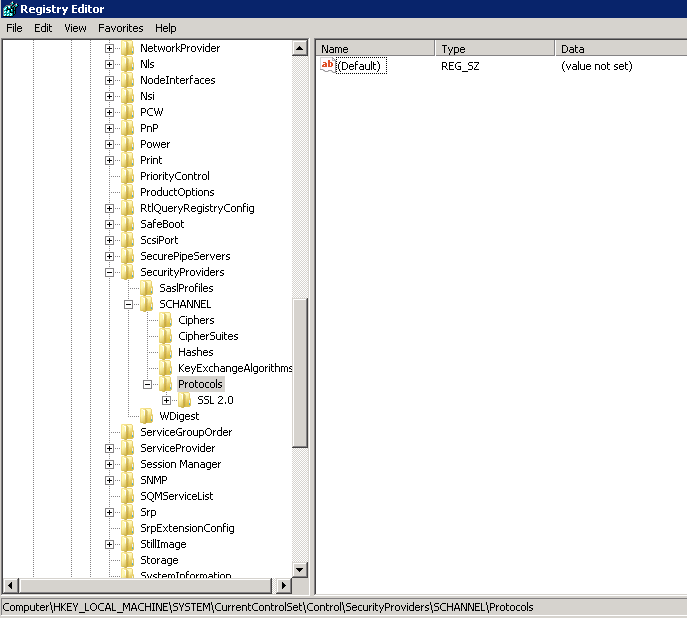
- Registry before powershell commands
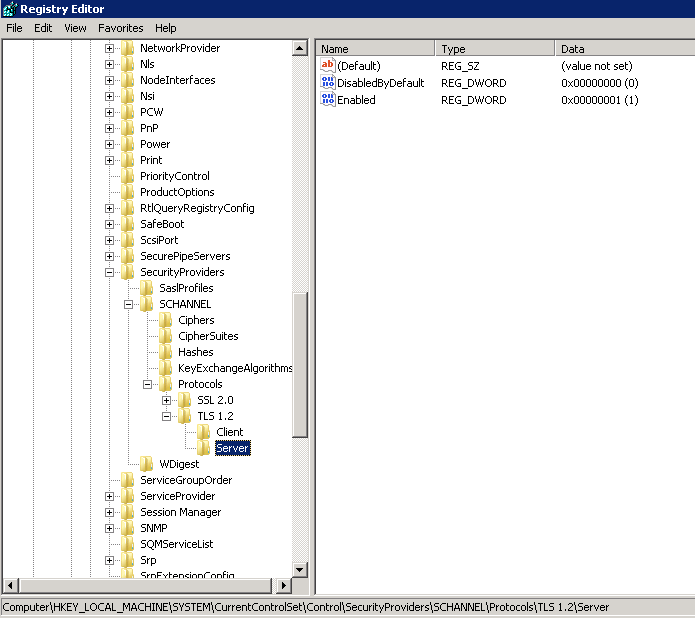
- Registry after powershell commands
- Next, we need to edit the server to default the use of the 256-bit ciphers
- Click Start->gpedit.msc
- Expand Computer Configuration -> Administrative Templates -> Network and select SSL Configuration Settings
- Double click SSL Cipher Suite Order and check Enabled
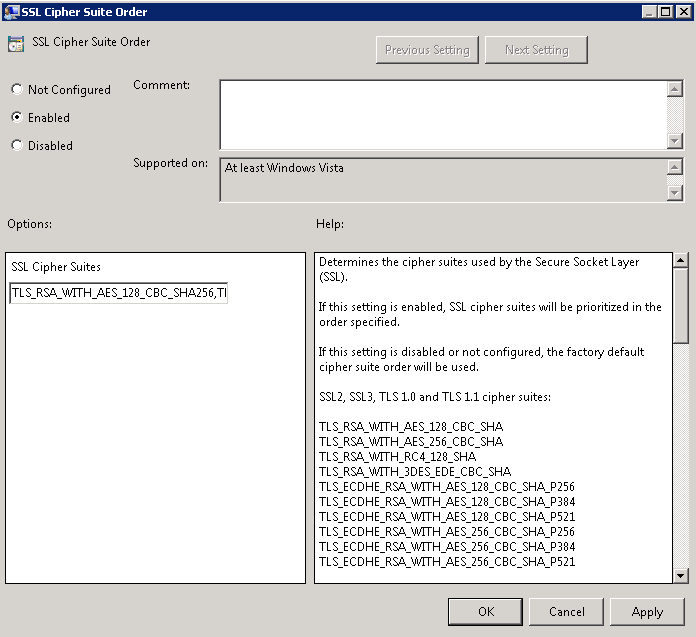
- Copy the text from the SSL Cipher Suites and paste it into notepad.
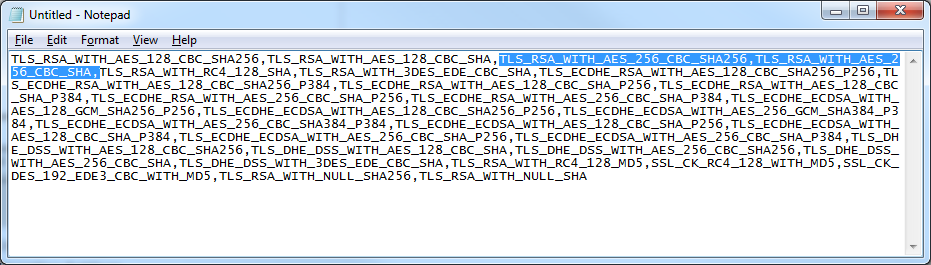
- Move the following to the beginning of the text document: TLS_RSA_WITH_AES_256_CBC_SHA256,TLS_RSA_WITH_AES_256_CBC_SHA (Note: here you could remove lower strength ciphers from the order to prevent the server from accepting those connections).

- Paste the Cipher Suites back into the SSL Cipher Suites box in Group Policy and click OK
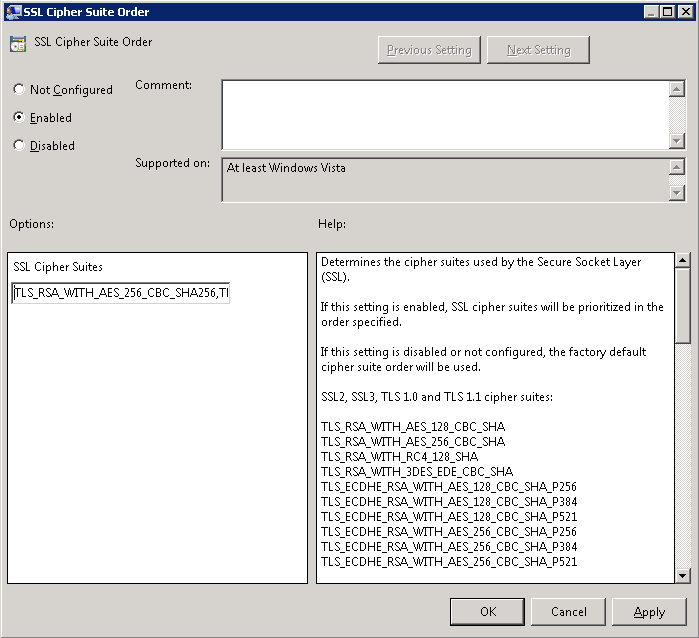
- Restart the server for the changes to take effect
- Click Start->gpedit.msc
References:
Changing the order of the Cipher Strengths:
http://social.technet.microsoft.com/Forums/forefront/en-US/ec033ff6-091d-441d-8ad3-7ea411100009/ssl-with-256bit-strength
Original source I found for the quick powershell commands to enable TLS v1.2:
http://www.derekseaman.com/2010/06/enable-tls-12-aes-256-and-sha-256-in.html

Thanking You so much. it saves my time today. Thanks
Arumugam M
thank you!
We still receives the "The server supports only older protocols, but not the current best TLS 1.2. Grade capped to B." on ssllabs ssl test, even though we enabled TLS 1.2 and disabled the old protocols.
We ran the IISCrypto tool and all seems to be in place. Still we see the above message.
Could it be that we are exposing our Exchange 2010 through an ISA Server 2006 running on a 2003 server system (which doesn't support TLS 1.2)?
We have some apache servers behind this ISA server which have no problems using TLS 1.2 though.
Thanks!
Hi Personlig,
While Exchange may support the higher level encryption, if the OS it is installed on doesn't (which I believe you are correct in that Server 2003 does not), you will need to upgrade the OS.
Jack
very helpfull thanks
A few more notes on this. The behavior differs based on the operating system. As provided here, Windows 2008 does not support TLS 1.1 or 1.2, which is very disappointing. 2008 R2 requires the registry keys and cipher order modifications, however 2012 and 2012 are a little different. In addition, browser configurations may be required. Furthermore, RDP requires a few patches and an rdp client in order to support TLS 1.2. Windows is unable to self-sign a sha2 RDP certificate, however MS does support SHA2 TLS 1.2 if you issue an RDP cert via an issued certificate.
SHA2 support for RDP requires https://support.microsoft.com/en-us/kb/3033929
https://support.microsoft.com/en-us/kb/3080079
OS compatibility and support matrix for ciphers - https://blogs.technet.microsoft.com/askds/2015/12/08/speaking-in-ciphers-and-other-enigmatic-tonguesupdate/
A link for a useful crypto utility https://www.nartac.com/Products/IISCrypto/
Appreciate the info Keith!
Pingback: 苹果ATS证书的选择及配置_苹果ATS证书的选择及配置_证书部署到Web服务器上的相关问题_常见问题_SSL证书 | 阿里云百科网