Here is how to implement 802.1X authentication in a Windows Server 2008 R2 domain environment using Protected-EAP authentication. I have designed the tutorial to be worked on in the specific order to prevent downtime if deployed during the day. By creating the Network Policy server first, once we switch the authentication type from whatever to 802.1X via RADIUS, our Network Policy Server will immediately start processing requests and allowing machines on the domain. By configuring the Cisco Wireless LAN Controller or Group Policy first, clients will try connecting to a RADIUS server that doesn't exist or present invalid credentials. If you have any suggestions on how to better the implementation I demonstrate here, please drop a comment below to improve security/stability of these types of deployments. 🙂
Active Directory
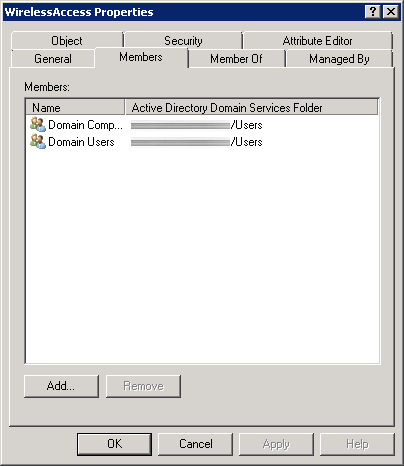
First, we need to create a security group in Active Directory to allow a list of specific users and computers to login to the domain. In this example, we will allow any authenticated user or machine on the domain to authenticate successfully to the RADIUS sever. In the screenshot below, we can see I have added both Domain Users and Domain Computers to a security group called WirelessAccess. Here is a screenshot with the above settings.
Network Policy Server
- Create a new Windows Server 2008 R2 or Windows Server 2012 machine
- Add the machine to the domain
- Give the machine a static IP: (I'll use 10.10.10.15 throughout this document as a reference to this server)
- Open up Server Manager, click Add Roles, click Next on the Before You Begin screen, check Network Policy and Access Services and click Next, click Next on the Introduction screen, check Network Policy Server (leave the rest unchecked) and click Next, click Install.
- Once Network Policy Server is installed, launch the Network Policy Server snap-in (via MMC or Administrative Tools)
- Inside of Network Policy Server, on NPC (Local), select RADIUS server for 802.1X Wireless or Wired Connections from the dropdown and click Configure 802.1X
- On the Select 802.1X Connections Type page, select Secure Wireless Connections, and enter My Company's Wireless. Click Next.
- Click on the Add... button. Enter the following settings:
- Friendly name: Cisco WLAN Controller
- Address: 10.10.10.10 (Enter your WLAN Controller's IP address)
- Select Generate, click the Genereate button, and then copy down the Shared Secret the wizard generated (we will use this later to get the WLAN Controller to talk to the RADIUS server). Click OK.
- Click Next.
- On the Configure an Authentication Method, select Microsoft: Protected EAP (PEAP). Click Next.
- Click Next on the Specify User Groups (we will come back to this).
- Click Next on the Configure Traffic Controls page.
- Click Finish
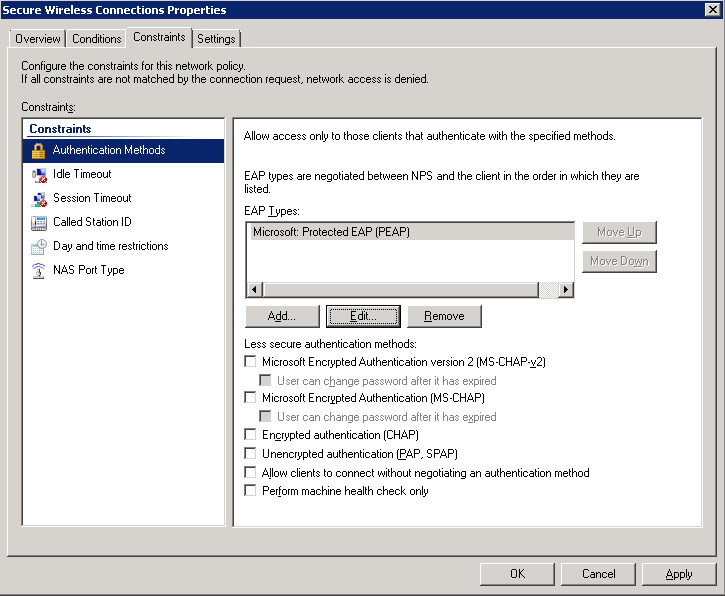
- Click on NPS (Local) -> Policies -> Network Policies. Right click Secure Wireless Connections and click Properties.
- Click on the Conditions tab, select NAS Port Type, and click Remove.
- Still on the Conditions tab, click Add..., select Windows Groups and click Add..., click Add Groups..., search for WirelessAccess and click OK. Click OK on the Windows Groups dialog box, click Apply on the Secure Wireless Connections Properties box. You should now have something like the image below:

- Click on the Constraints tab.
Cisco WLAN
- Login to your Cisco Wireless Lan Controller
- Add a RADIUS server to your controller
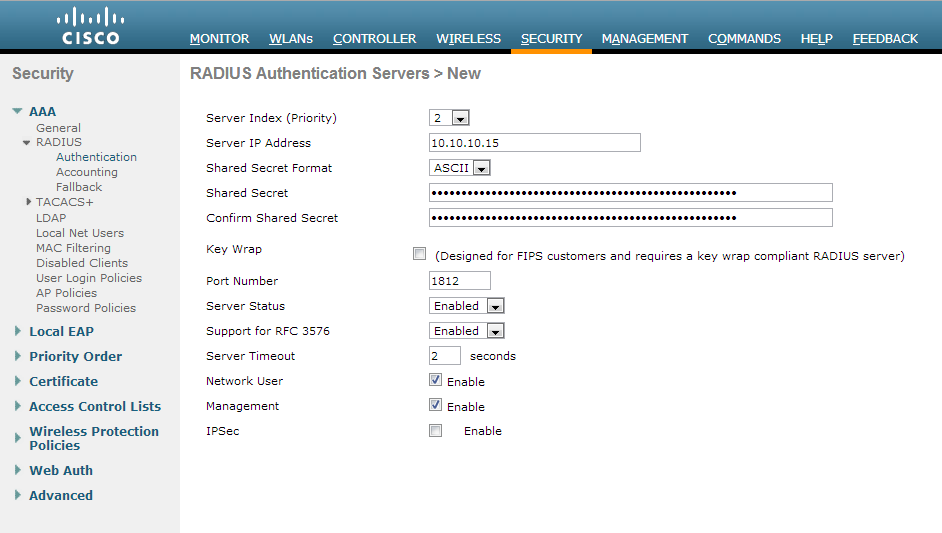
- Click on the Security tab
- Select AAA -> Radius -> Authentication on the left side
- Click the New... button in the top right
- Server IP Address: 10.10.10.15 (The IP address of your NPS server we setup earlier)
- Shared Secret Format: ASCII
- Shared Secret: The long generated password you wrote down when setting up the Network Policy Server
- Confirm Shared Secret: Same password in previous step
- Key Wrap: unchecked
- Port Number: 1812
- Server Status: Enabled
- Support for RFC 3576: Enabled
- Server Timeout: 2
- Network User: Checked
- Management: Checked
- IP Sec: Unchecked
- Here is a screenshot with the above settings
- Create or modify a wireless network to use 802.1X
- Click on the WLANs tab
- Create a new wireless network or select an existing WLAN ID to edit
- On the "WLANs > Add/Edit 'My SSID'" page, use the following settings
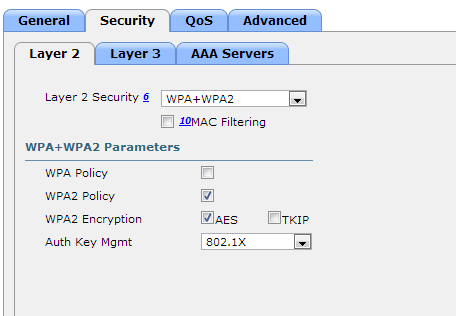
- Security Tab
- Layer 2 Tab
- Layer 2 Security: WPA+WPA2
- MAC Filtering: Unchecked
- WPA+WPA2 Parameters
- WPA Policy: Unchecked
- WPA2 Policy: Checked
- WPA2 Encryption: AES checked, TKIP unchecked
- Auth Key Mgmt: 802.1X
- Layer 3 Tab
- Layer 3 Security: none
- Web Policy: unchecked
- AAA Servers Tab
- Click Apply
- Layer 2 Tab
- Security Tab
Group Policy
- Go to your domain controller and open up the Group Policy Management console.
- Right click the Organizational Unit you want to apply to policy to and select Create a GPO in this domain, and Link it here...
- Note, the policy must be linked to the OU containing a group of machines you want to have WiFi access to or a parent of the OU.
- Enter in 802.1X WiFi Policy for the Name and click OK
- Right click your new GPO and click Edit
- Navigate to Computer Configuration->Policies->Windows Settings->Security Settings->Wireless Network (IEEE 802.11) Policies
- Right click and select Create A New Wireless Network Policy for Windows Vista and Later Releases
- Ensure the following settings are set for your Windows Vista and Later Releases policy
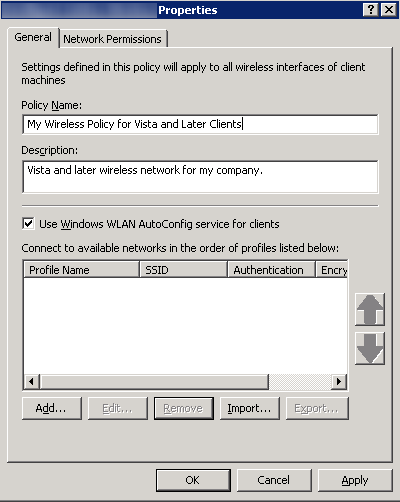
- General Tab
- Policy Name: My Wireless Policy for Vista and Later Clients
- Description: Vista and later wireless network for my company.
- Check Use Windows WLAN AutoConfig service for clients
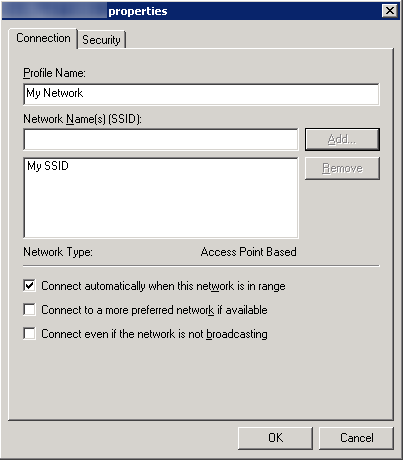
- Here is a screenshot with the above settings
- Click the Add... button and select Infrastructure
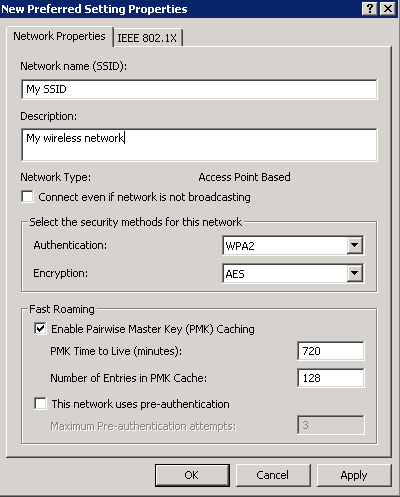
- Connection Tab
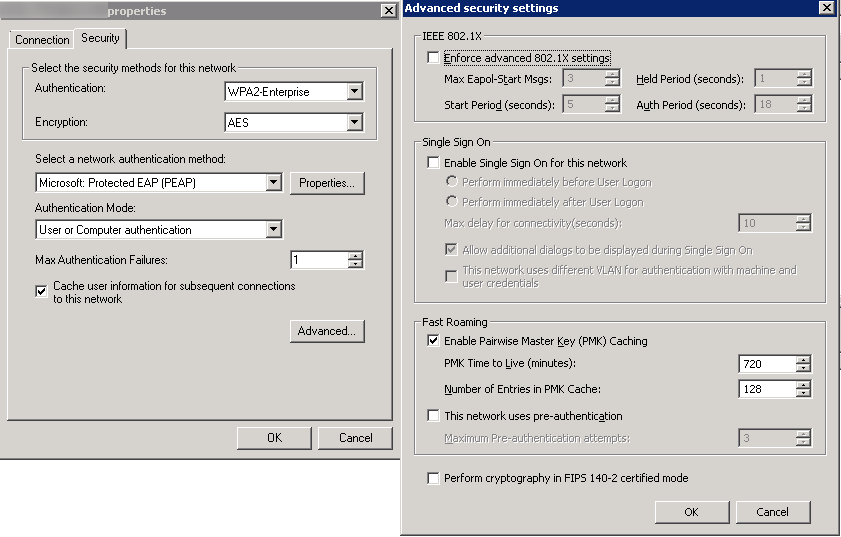
- Security Tab
- Authentication: WPA2-Enterprise
- Encryption: AES
- Select a network authentication method: Microsoft Protected EAP (PEAP)
- Authentication Mode: User or Computer authentication
- Max Authentication Failures: 1
- Check Cache user information for subsequent connections to this network
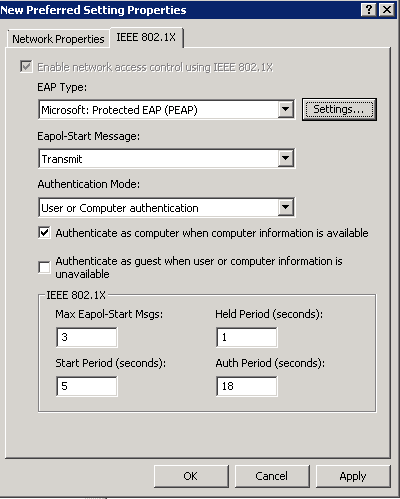
- Here is a screenshot of the above settings with the Advanced tab open as well
- Click OK
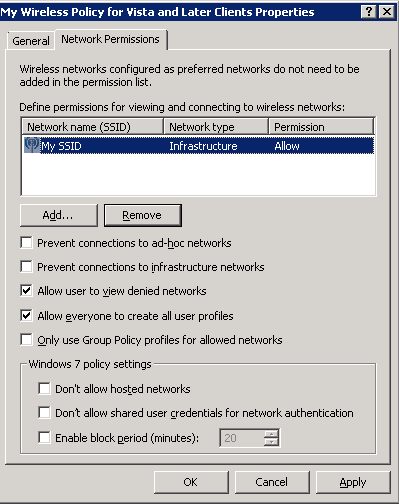
- Network Permissions Tab
- Enter your network into Define permissions for viewing and connection to wireless networks if it hasn't been added already.
- Uncheck Prevent connections to ad-hoc networks
- Uncheck Prevent connections to infrastructure networks
- Check Allow user to view denied networks
- Check Allow everyone to create all user profiles
- Uncheck Only use Group Policy profiles for allowed networks
- Leave all Windows 7 policy settings unchecked
- Here is a screenshot with the above settings (note, you may change the settings above to be in accordance to your policy. Just ensure you don't check Prevent connections to infrastructure networks).
- Click OK
- General Tab
- Right click and select Create A New Windows XP Policy
- Ensure the following settings are set for your Windows XP Policy
- General Tab
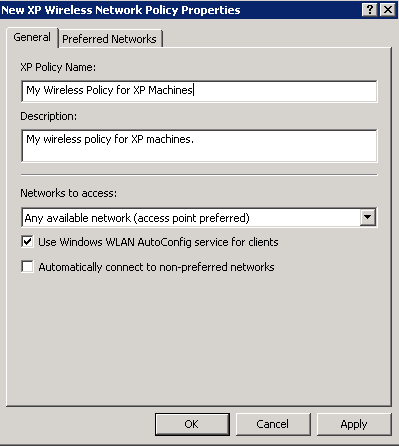
- XP Policy Name: My Wireless Policy for XP Machines
- Description: My wireless policy for XP machines.
- Networks to access: Any available network (access point preferred)
- Check Use Windows WLAN AutoConfig service for clients
- Uncheck Automatically connect to non-preferred networks
- Here is a screenshot of the above settings.
- Preferred Networks Tab
- Click the Add... button and select Infrastructure
- Network Properties Tab
- IEEE 802.1X Tab
- Click OK
- Click the Add... button and select Infrastructure
- Click OK
- General Tab

Hi,
i follow al the guide, but when i try to autenticate via wireless i cant
i enable the debug in the WLC and i have this error
Access-Reject received from RADIUS server 192.168.7.10 for mobile 00:1e:65:6c:ea:74 receiveId = 5
can you please help me?
Hi Alejandro,
It looks like you are having issues with the WLC communicating to the Radius/NPS server. I would verify your settings are correct for your NPS server in my guide above (Section "Network Policy Server"). I haven't seen this error before, but if I could take a guess from the error log, you either have the Shared Secret incorrect or have not added the IP of the WLC to the NPS server's approved RADIUS clients (Step 6 of the Network Policy Server section).
Hope this helps!
Jack
Phase 2 Authentication = ?
CA Certificate = ?
User Certificate = ?
Identity = ?
Anonymous Identity = ?
Are these all fields equal to "NONE" ???
Basing from the GPO you mentioned here, I've created a GPO from a parent OU, so the ComputerNames registered in the Active Directory are only the Computers that are being pushed with GPO you have created???
What about the Laptops that are not joined in the Domain??? Can I still join to the SSID using A.D Credentials???
Hi Lewy,
For your first post, where exactly are you finding those fields?
For your second question about the GPO, if you create a GPO and attach it to the parent OU, any Computers in Active Directory will probably be applied with your policy. The policy will not be pushed to any machines not registered to the domain or not under the parent the GPO was applied to.
As for the laptops that are not apart of the domain, you can join devices to the domain, but in this case, the machines will need to accept the certificate of the RADIUS server. So unless you use a public certificate or manually import your certificate authority's certificate onto the machine to establish trust, the machines will probably not join.
Hope this helps!
Jack
Thanks a lot. Regarding for my First Post, I see this when I use Android Mobile Devices like HTC Celphones, etc...
Regarding my 2nd question, I can see this after I input my A.D. Credentials,
The Credentials provided by the server could not be validated. We recommend that you terminate the connection and contact your administrator with the information provided in the details. You may still connect but doing so exposes you to security risk by a possible rouge server.
Details
Radius Server: OUR_A.D._COMPUTERNAME.domain
Root CA: tsada-tsada-tsada-CA
The server "OUR_A.D._COMPUTERNAME.domain" is not configured as a valid NPS server to connect to for this profile..
Do you have any idea to get rid of this???
Thanks in advance !
This guide is immense, many thanks!
I solved my 2nd concern. I'm now figuring out my 1st concern , I'm using now a Android Tablet for my testing. Laptop is already working now with no Alerts on certificates. Please help with my 1st concern.
Thanks a lot. Have a gread day ahead.
May the force be with you ! =)
To connect your Android device to the wireless network, use the following settings:
EAP Method: PEAP
Phase 2 Authentication: MSCHAPV2
CA Certificate: (unspecified)
User Certificate: (unspecified)
Identity: Active Directory Username
Anonymous Identity: leave blank
Password: Your Active Directory Password for the user
Hope this helps!
Jack
Yeah !!! Thank you very much !!! Everything's working now !!!
I really apprectiate it. Thanks a lot once again. =)
Regards,
Lewy
Hi Sir,
Can this support Global Catalog Search ???
Not quite sure what you mean. Can you elaborate what exactly you are trying to achieve?
Jack
Hi Sir
It's because when you do LDAP Search you are only contained in the Domain, but when you do Global Catalog search, you are contained in the entire forest.
Thanks
You are specifying which security groups that are allowed to login; so yes, you could support this for users in different domains, provided this is being managed from the parent domain.
Jack
Yes Sir . I've just tried it and it's also working now.
Thanks a lot.
Hi Sir,
It seems Windows 7 , Android tablets are working but this windows XP is not working it's always been acquring network address. It seems a Windows XP issue/LAN Card issue ? I think it cannot support WPA2(Enterprise) when using Windows XP.
Did you already try this in Windows XP?
Hi Lewy,
You will need to create a policy for Windows XP clients. In the Group Policy section above, instead of doing:
Right click and select Create A New Wireless Network Policy for Windows Vista and Later Releases
Try the following:
Right click and select Create A New Windows XP Policy
Jack
I've already created a Windows XP Policy but I believe that this is a WiFi Card driver issue. I will find a portable USB WiFi LAN Card and plug it in the Windows XP PC and I will test if this will work.
Thanks a lot for your kind response.
Regards,
Lewy
Hi Sir,
Just wanna ask another question.
What are you using under the Group Policy - Security Filtering???
Are you using "Authenticated Users" or the name of the "Security Group"??? e.g. Wireless_Users
Where is the option for Group Policy - Security Filtering? Inside of a group policy template you are editing or on the NPS server? The exact configuration above works; you should not have to be making one off tweaks.
Jack
This option is under the GPO itself, when you right-click the GPO and press edit. You will find Security Filtering in which the default value is "Authenticated Users".
OK, so as you said, I will leave it as it is(Authenticated Users).
Thanks a lot.
Regards,
Lewy
Hi Sir,
Regarding the PEAP Properties, did you check the "Validate Server Certificate"???
This will be viewed when you click the "Settings" beside the Microsoft PEAP in the IEEE 802.11x Tab.
Hi Lewy,
Yes, this is checked. If you have further questions, at this point, I would highly encourage you to contact a consultant to help you configure settings outside the scope of this article.
Jack
Question here,
Windows XP/Vista Users need some kind of Policy being pushed to them, what if this Windows Laptop connects to the SSID for the very first time???(assuming policy has not yet been pushed)
How do you do this? Do you hardwire the Windows Laptop? Then you issue, gpupdate???
Thanks a lot.
Hi John,
You are correct; you will need to hardware the machine and connect it to the domain for it to push the policies to be pushed down for the first time.
Jack
Great tutorial. Question, in our environment, we have non-domain computers (product development department) that will need to use the corporate wireless, as well as domain computers. How would you set this up? Does NPS on Server 2008 R2 require the user/computer GPO or can I simply use Windows Groups or User Groups (under conditions) and add the Domain Users OU?
Thank you,
John Woods
Hi John,
For the non-domain joined machine, I believe you will need to import your root CA's certificate onto the non-domain joined machine so it trusts your local network/the NPS server when it authenticates. Additionally, depending on your configuration, you may need to generate machine certificates if you require the machines to use certificate based authentication. The GPO will help with automatically connecting up to the network, but I don't think it will help too awful much when it comes to certificate auto-enrollment as the machine is not apart of the domain.
Hope this helps!
Jack
Hello,
I have followed the steps outlined in this tutorial but I'm unable to proceed further on this as whenever I connect the client it prompt for the username and password when I supply the username I get Warning in the IAS which is wrong username/password.
I quoted in this tutorial "The first time you connect, you’ll be asked to accept the RADIUS server’s certificate." Does that mean the certificate has to be installed on the client machines in order for them to authenticate and connect to the WiFi network?
Also I can see the client machine Event Error 36882 "SChannel" which is stated that the Certificate received from the remote server was issued by an Untrusted Certificate Authority and none of the data contained can be validated. Connection request failed.
In my environment I have WLC 5508 and IAS 2003. Any help can be provided to achieve this?
Thanks,
I quoted in this tutorial “The first time you connect, you’ll be asked to accept the RADIUS server’s certificate.” Does that mean the certificate has to be installed on the client machines in order for them to authenticate and connect to the WiFi network?
Also I can see the client machine Event Error 36882 “SChannel” which is stated that the Certificate received from the remote server was issued by an Untrusted Certificate Authority and none of the data contained can be validated. Connection request failed.
The client machines will need the root certificate installed on the machines to trust the RADIUS server if you use your own self-signed certificate. This is recommended to be pushed out via Group Policy on your domain.
I'm not sure about this setup using IAS. I have only done a deployment using its successor (NPS) in Server 2008.
Hope this helps!
Jack
Hello,
Thanks for your reply, but majority of my clients' computer are not joined to the domain. Is there a way I can make success of this without worrying about the cert?
I need the "User or Computer Authentication" on the Security tab of the GPO to be enforced, but this does not get enforced. I need user and computer authentication to be authorised by RADIUS.
However, that setting within the Wireless SSID on a laptop does not change after the GPO is applied.
I have the GPO with permissions for both a group of users and a group of computers and the GPO is applied to OUs that the users and computers are in.
It seems to apply the rest of the GPO but not that part.
Any Ideas? Thanks
Do you have any filters applied to your GPO? Also, are you sure that the computer objects fall underneath the hierarchy of the policy?
Jack
Hi Jack,
Thanks for this guide. I still have issue, the Radius server still does not want to authenticate my user account.
I have the account inside the security group but still when I tried to authenticate using my iPhone it said wrong password.
For PEAP, (NPS->Network Policies->Authentication Method) do we need to configure the certificate on the Certificate Authority server? If yes how to configure that.
Thanks.
Hi Jimmy,
You will need to configure a certificate authority if you are using PEAP. Configuring your own internal CA is outside the scope of this document unfortunately. You can read more in configuring your own PKI environment here: http://technet.microsoft.com/en-us/library/gg682023.aspx
Hope this helps,
Jack
Hi Jack,
If we do not want to use the certificate is there any option? We have followed the steps above but still it does not work.
Thanks.
Jimmy
You can choose to use a less secure authentication mechanism on the network policy server (not PEAP or EAP), that doesn't use certificates. However, this is not covered in the scope of this tutorial. You can find out about which protocols use certificates here: http://technet.microsoft.com/en-us/library/dd348505(v=ws.10).aspx
Jack
Thank you so much for the tutorial, it is very useful. Our environment is a mixture of win 7 & win 8 clients. My question is why are some of my users are Not prompted for the user credentials (especially First time Users)? Is there a way to actually force all users to be authenticated every-time they connect to an AP? the reason I ask is that I noticed that once a client is authenticated, the next time the user tries to connect to the AP, they are automatically authenticated and I not sure if that it is safe.
The user's should be authenticated each time they login. You may want to look at what options you have inside your policies. Have you allowed people to sign into the network only if the machine presents a certificate?
Jack
TIP - just reading your tutorial Jack which should all work correctly, however I had to call CISCO for support (and go through quite a few levels) when configuring mine (which was a while ago) it turns out that i needed to use the "domain users" or "domain computers" built in groups specifically, if I wanted to use group that I created say "wireless users" and add users to the group from a specific OU the user would not authenticate as soon as I added the domain computers group, hey presto...
Hi Matt,
The tutorial does cover adding both the users and computers into a single group for the NPS server to allow the clients to authenticate. You don't have to use domain users or computers neccessarily, they can be changed to be much more granular. These policies should be configured inside of Active Directory and the NPS server, rather than on Cisco's end.
Hope this helps!
Jack
Hi,
I'm try to get my company to work with the 802.1X. when i followed the instructions above i can see my wifi, but when i try to connect i get an error 'Windows was unable to connect to my wifi'
I had a psk key before and i updated the WLC to the above instructions. do i have to remove any settings or anything?
Any ideas ??
Regards
Steven
Hi Steven,
If you are using PEAP authentication, have you deployed an internal PKI (public key infrastructure) in your environment to provide computer authentication? You will need this before you will be granted access to the network. Additionally, you may want to go over the Network Policy Server steps again to ensure your RADIUS server is accepting authentication requests.
Hope this helps!
Jack
Is it necessary to run IAS on another Windows Server or can it run on the same server as the Domain Controller?
Hi Hoss,
This guide does not cover the use of IAS. You could install the NPS role on your DC, but I wouldn't recommend it.
Jack
Hi Jack.. Thanks for the wonderful guide. Quick question. If I wanted to enable single sign on, where the user will be automatically logged onto the wireless profile during the domain authentication, all I would need to do is select the "Enable single sign on for this network" under the 802.11 properties > advanced security settings tab right? Is there anything else that would need to be enabled?
Hi tc132,
You will need to check Connect Automatically when this network is in range for the machine to connect automatically. See step 5.1.3.
Jack
Hello Jack,
This is a very good article and very informative.
In my environment some clients who actually connected before are sometimes unable to connect to the WPA2-Enterprise SSID, a message triggers "Windows is unable to connect to "SSID". However, the same client is able to connect to another SSID (Pre-Shared) which is being broadcast by the Wireless Controller. When I check the client side the GPO settings are successfully added and the WPA2-Enterprise profiles listed under Manage Wireless Networks window.
What will be the best method to troubleshoot this kind behavior?
I hope to know the troubleshooting methods and reason for the behavior I discussed above.
Hi Kishan,
This sounds like the machine has not been authenticated to the network. I would verify your NPS policies are configured properly.
Jack
Hi Jack,
Very useful sharing. Thanks a lot.
1. On both joined domain machine and unjoined domain machine, we still have to install CA cert?
2. my domain is ABC.COM and machine 01 is already joined to the domain but when i try to connect, there is a pop up windows ask me to use windows logon account (windows 8). When i stick that option, it fills in ABC\username password which is great but it did not work, i have to fill in ABC.COM\username password and it works. Seems like my logon windows is different to this ABC.COM\username password. i don't know why. Should be the same.
Thanks Jack
Hi Mark,
For question one, have you configured auto-enrollment/pushing out your CA certificate through group policy to the machines?
For question two, have you disabled netbios on your clients? The short name ABC is a netbios alias whereas abc.com would be the fully qualified domain name of your domain.
Hope this helps,
Jack
Hi Jack,
Now, it is working perfectly for those joined domain machines.
The non joined domain is still not working, i did install the cert and im getting " Authentication failed due to a user credentials mismatch. Either the user name provided does not map to an existing user account or the password was incorrect". i was trying like ABC\username password and username password, pretty sure that it's correct.
BTW, there are like 3 or 4 Certs in my CA server, which one i should use to export to install onto the non joined domain machine. First i did not know so i just stall all of them and i get rid of " certificate chain was issued by authority that is not trusted". After that i got the above error. 3 or 4 Cert have the same name so that's why i do not know i should use which one.
Thank you, Jack
Hoang
You need to import the root certificate authority and any intermediate certificates (if you have them), into the non-domain machines. Go to your NPS server and look at what certificate you imported. When you view the certificiate, you should be able to see the certificates that are needed to establish the trust as well as export them as a .cer/.crt file to import into the non-domain machines.
Hope this helps,
Jack
The Issue you are experiencing is related to the mechanism the Microsoft NPS uses.
Check this article here:
https://social.technet.microsoft.com/Forums/windowsserver/en-US/d51b56b1-6d1d-4e4f-9888-9cb3a2ad27dc/nondomain-computer-certificate-authentication-in-nps?forum=winserverNAP
Can it also be used on Windows 2003 Active Directory with HP MSM760 Controller??
Regards
Erneeraq
Hi Erneeraq,
That configuration is out of the scope of this tutorial. Based on little research though, it appears your HP MSM760 controller will support 802.1X, so you could integrate that with NPS.
Jack
Hi Jack
Once again thank you for the post. I have a situation where all my windows 8, & 8.1 clients are authenticated and they connect without any issues, this includes MacBook, Android & iPhones, it just works however None of my Windows 7 clients are able to connect to the SSID. What could be wrong or what is that i might have done wrong?
Hello,
This could be caused from multiple things, but I would check the following:
1. Are the Windows 7 machines receiving your certificate authority certs
2. Are the Windows 7 machines receiving group policy settings to connect to the network (can you connect manaully)
3. On your NPS server, have you added an exclusion to Windows 7 clients.
Hope this helps,
Jack
Pingback: Konfigurera Cisco Wlan Active Directory | angsknarren
Jack, great tutorial. How does one get away from the certificate drama and the self-generated certificates? Buy a public CA issued certificate I get it. However this ISN'T a an SSL type of certificate as that wouldn't import into NPS. Where does one purchase such certificate. Go Daddy has no clue and their support would want to you to get an SSL one which would not import into NPS.
The objective with this public CA issued certificate is to avoid any and all issues of having to import root before a client could authenticate. Otherwise this is a nightmare with iPhones; tablets; all non-Microsoft and non-domain devices!
Hi Bubba198,
You can use a SSL certificate issued by a public certificate authority (such as GoDaddy, Comodo, VeriSign, etc.). You will need to import this into the machine's certificate store so that you can select it as an option.
Jack
Thanks Jack
Tried that already; The request; issuance and import works just fine. The SSL gets imported just as you said into the NPS' machine certificate store. However NPS does NOT see it as a viable choice. I am guessing that is because a special type of certificate is required with EKU extension marked as Client Authentication purpose 1.3.6.1.5.5.7.3.2
As the KB states: One such requirement is that the certificate is configured with one or more purposes in EKU extensions that correlate to the certificate use
http://technet.microsoft.com/en-us/library/cc772401(v=ws.10).aspx
Actually, looks like you are right Bubba, GoDaddy will not issue an EKU certificate, so you will not be able to go with them. According to the techNet article above though, it looks like VeriSign might be able to issue your organization one though.
In this case, the only cost effective route, in my option, would be to look at implementing your own PKI environment using Active Directory Certificate Services (AD CS). While it does take some planning and setup, the additional setup will allow your organization to meet the requirements in more complex security configurations, such as this.
Hope this helps!
Jack
P.S. Thanks for the response on this, definitely good to know for future reference! You learn something new everyday! 🙂
Great article, all works as explained.
Q: How can I limit number of Wi-Fi connections that user can gain. I would like to have maximum 1 at the time. I don't want one user to simultaneously connect all his devices on Wi-Fi, mobile, tablet, lap-top,....
Tnx, once again
Hi Zvonimir,
That is a very good question. I don't believe there is a simple option to limit concurrent sessions by user in the Microsoft realm of things. If you are looking for a simple way to achieve this, there is a product called UserLock that can be used: http://www.isdecisions.com/products/userlock.
I did find a KB article from Microsoft where there is a script to limit the user's concurrent connections in older versions of Server, but I would highly highly highly recommend you try this in a test environment first. This tool will try to extend the AD schema, so I wouldn't recommend just testing this against your production AD environment (especially since it isn't officially supported for newer server versions): http://support.microsoft.com/kb/237282
Hope this helps!
Jack
Dear Jack,
Thanks for your article. Nice to see and reed the questions and reply's.
Very, very informative!
We found your article in the process of trying to enhance our setup, which is more or less identical to your description, in our schools, in use for more then 4 years now.
Started with Cisco APs in a W2k3 server environment with Radius on the DC's.
Now with Cisco and Aruba APs (+300) with NPS on a W2k12R2 DC on a w2k12R2 domain.
From the start we didn't succeed in our main goal:
giving (this) WiFi to only domain users working on domain devices (our laptops). And we are left with the NPS rule: domain users OR domain devices.
So having an account on our domain gives all of them access to this WiFi SSID on all of the devices brought in. And that is by now quite a number of realy unwanted devices on the target VLAN they are entering.
We can't get things working with both groups seperately added in the ruleset and thus seen as AND which means both conditions must be satisfied.
If we do so nothing works!! No one gets the WiFi.
In your setup you use a group with both these default groups mentioned as a member.
Think that works the same way ..... as OR user or computer.
We will give your group idea a test.
We will let you know but maybe in the meantime you can emphasise on our problem and goal with your expertise.
Thanks in advance,
Willem
The settings I have in this tutorial will allow authentication via the machine OR the user.
Please let me know how the group scenario goes,
Jack
Hi Jack,
Great information. I'm a little confused about the certificates though. I understand that laptops joined to the domain won't need any certs imported. Will Android tablets/phones need certs imported or just set the following:
EAP Method: PEAP
Phase 2 Authentication: MSCHAPV2
CA Certificate: (unspecified)
User Certificate: (unspecified)
Identity: Active Directory Username
Anonymous Identity: leave blank
Password: Your Active Directory Password for the user
Thanks!
E
Hey Eric,
You will want to import your CA's certificate on iOS devices as it will prompt you to verify if you trust the certificate or not of the NPS server, however I haven't seen this behavior on the Android side.
Also, you will want to import the certificate authority to your local machines/laptops, so they trust the network when trying to connect.
Hope this helps,
Jack
Hi,
is this setup possible to work for Guest WIFI?
Guest Wifi is on another subnet, and RADIUS is on AD. Also guest users are on AD but I can't apply GPO on guest laptops.
Thanks
Hi Dusan,
Not sure why you would like this on a guest network as you would want it 100% separate from your main network, but if you do want to proceed, you should be able to as long as the Guest WiFi can communicate to the NPS server.
Jack
hello sir,
i have following your guide, and ended up with ssid who asking for username and password?
is this the goal or i have made a mistake?
thx
If your computer objects have autoenrollment configured properly, you should not be prompted for a username/password.
Jack
Hi,
I have two Windows AD servers in different domain in the setup. For example abc.com belongs to AD server 1 & xyz.com belongs to AD server 2. These two AD server have trust relationship with each other. I want to integrate these two AD servers with Cisco WLC & create one SSID for users of two domains i.e abc.com & xyz.com.
I hope this will work. Users belong to different domain will be able to authenticate through respective AD server using single SSID.
Regards,
Ram
Hi Ram,
You should be able to do this, just make sure you tell the NPS server to allow those resources when you create your groups.
Hope this helps,
Jack
This article is phenomenal in terms of being 1) easy to understand and 2) thorough. In my case, I was using Aruba WAPs and not Cisco, but the Windows part is the harder part and poorly documented by MS. Thanks much for making this valuable resource available to sysadmins the world over.
Appreciate the feedback Dave!
This worked like a charm thanks a lot for the document.
I have been using this for laptops for years. Has anyone had any luck using NPS with Cisco 8821 wireless phones? If so, can you point me to a tutorial? I have done some ready, but I have not had any luck getting it to work. I am trying to get away from PSK.