Here are the steps to configure SSL on your servers running the Windows Server Update Services. This guide was written using Server 2012 R2, however it should be the same steps for Windows Server 2008 R2 as well. This guide also assumes you have a working instance of WSUS installed and configured, using default ports.
- Login to your WSUS server
- Open up Server Manager
- Select Tools -> Internet Information Services (IIS) Manager
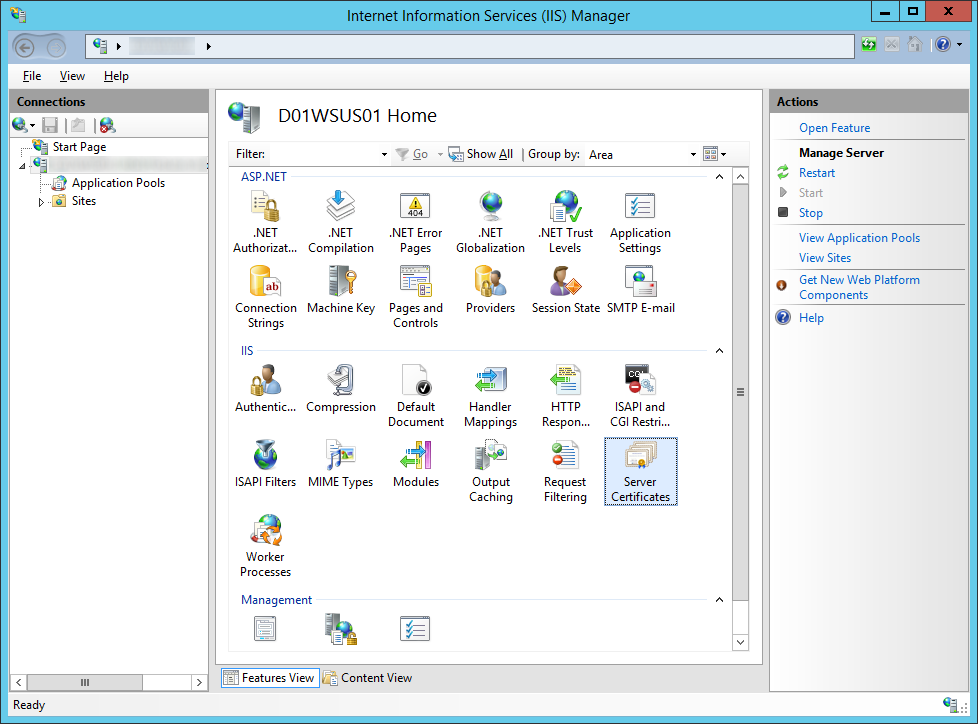
- Generate a SSL certificate
- Click on your Server and select Server Certificates
- If you have your own PKI environment, follow these steps, if not, jump to step three
- If you need to submit a certificate request to an external certificate authority like Goaddy, Verisgn, Comodo; follow these steps
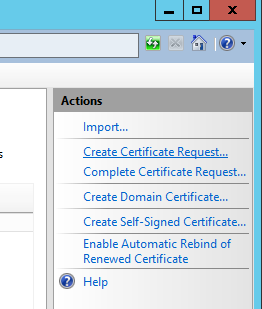
- Click Create Certificate Request on the right side
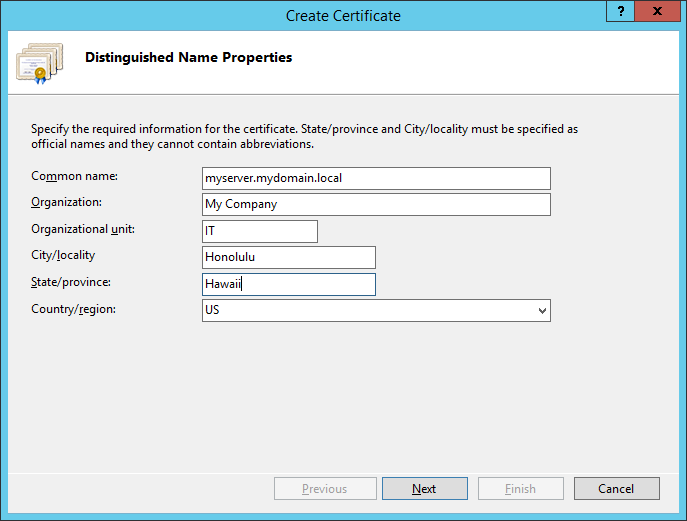
- Fill out the Distinguished Name Properties and click Next
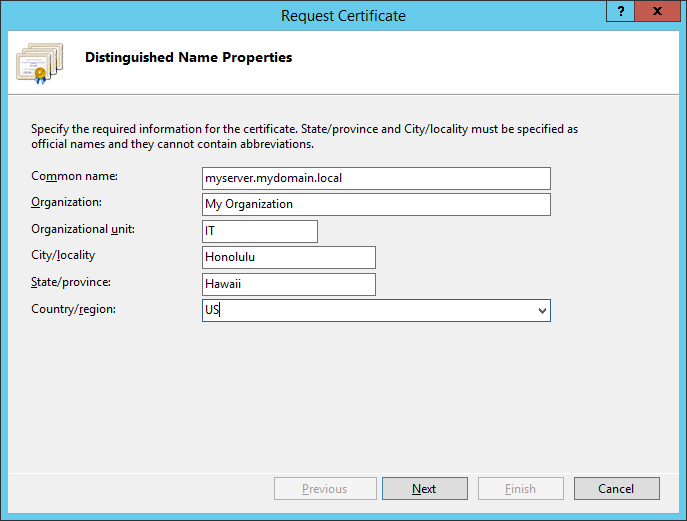
- Change the Bit length to 2048 and click Next
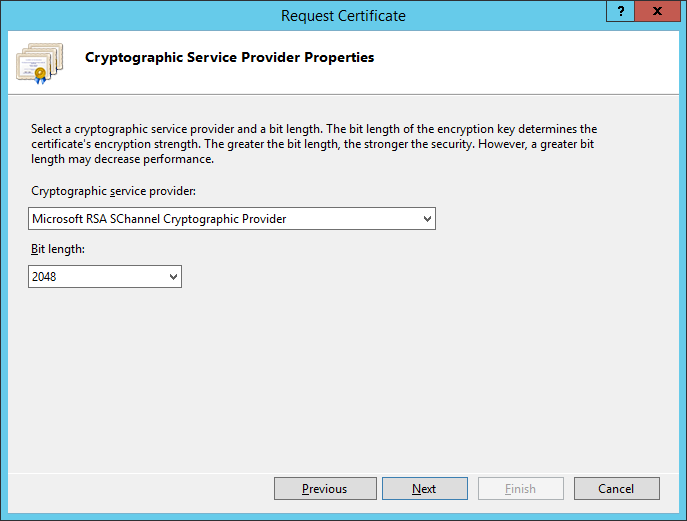
- Select a location on where to place the CSR file that will be generated by the wizard and click Finish
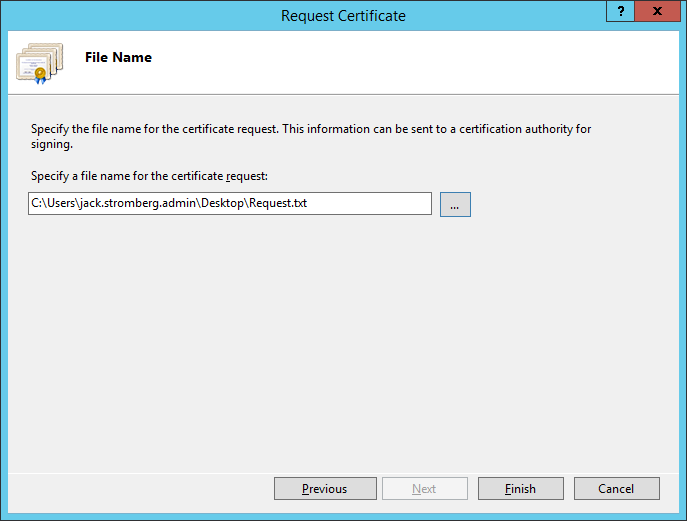
- At this point, send the request to your certificate authority (like GoDaddy, Verisign, or your own internal certificate authority). You should receive back a .cer file once the claim has been fulfilled.
- Click on Complete Certificate Request on the right side
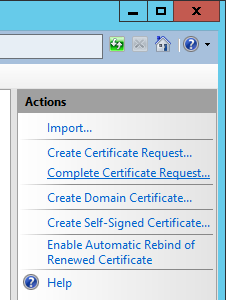
- Select the .cer file that your public certificate authority provided you, type in a friendly name (this can be anything), select Web Hosting for the certificate store, and click OK
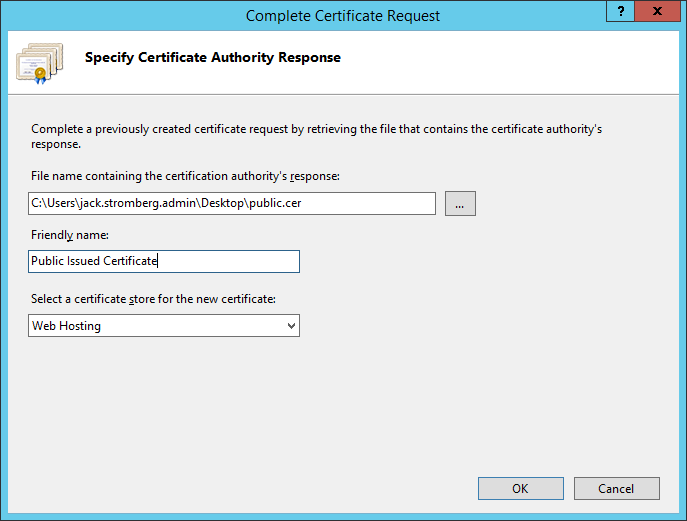
- Click Create Certificate Request on the right side
- Click on your Server and select Server Certificates
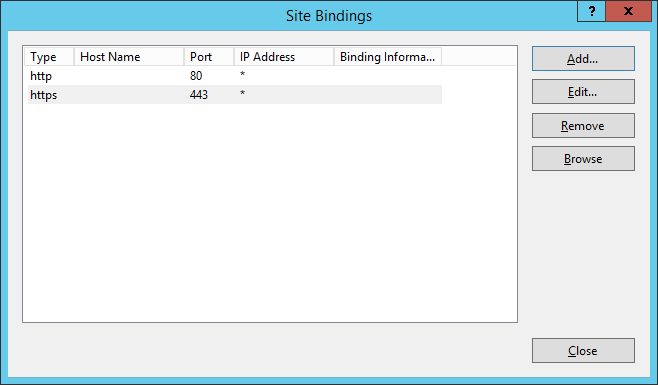
- Next, we need to bind the SSL certificate to your network adapter.
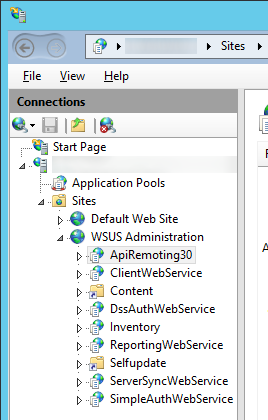
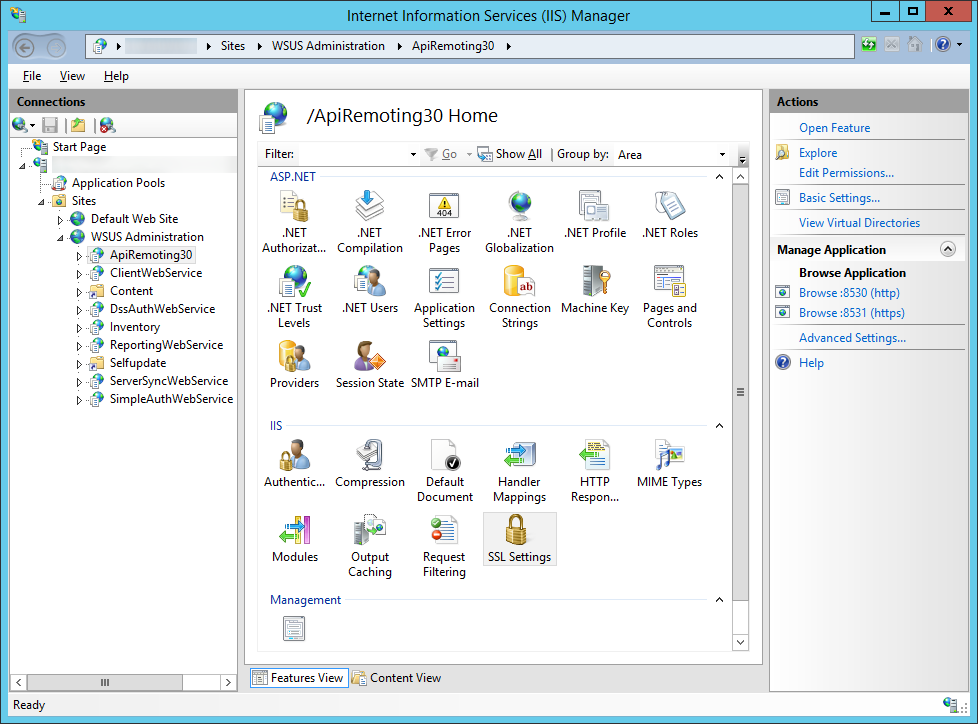
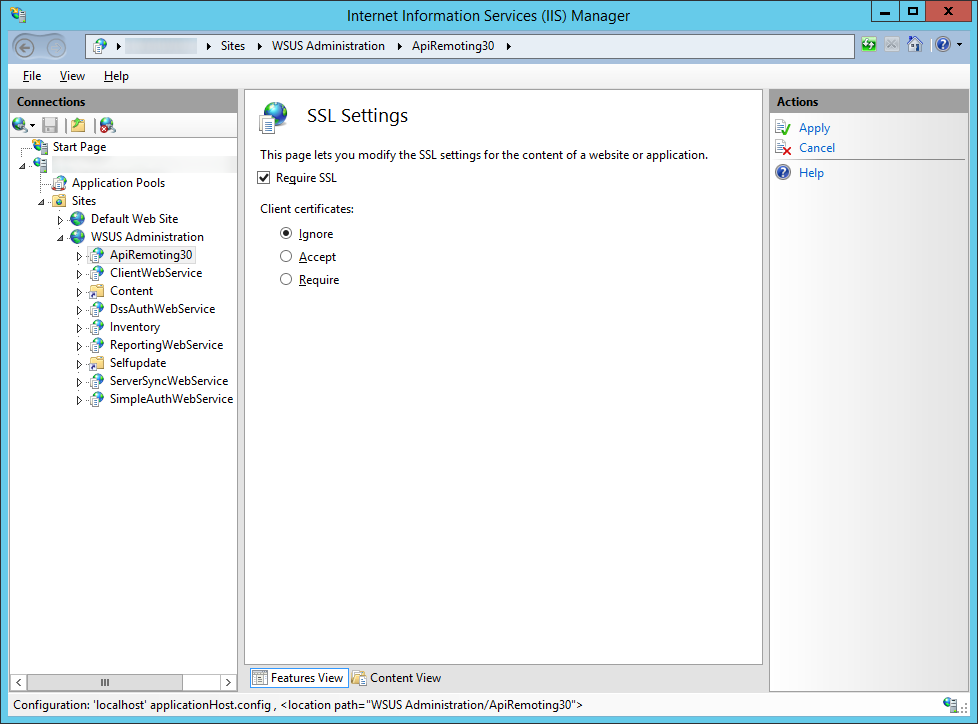
- Next, we need to enforce SSL encryption on the following virtual roots
• ApiRemoting30
• ClientWebService
• DSSAuthWebService
• ServerSyncWebService
• SimpleAuthWebService - Next, we need to execute a command to tell WSUS to use ssl
- Restart the WSUS server to make sure all changes take effect. You should be able to bring up the WSUS management console if all went well.
- Configure your clients to connect via SSL to the WSUS server via Group Policy
- Login to your domain controller
- Open up Server Manager

- Open up Group Policy Management
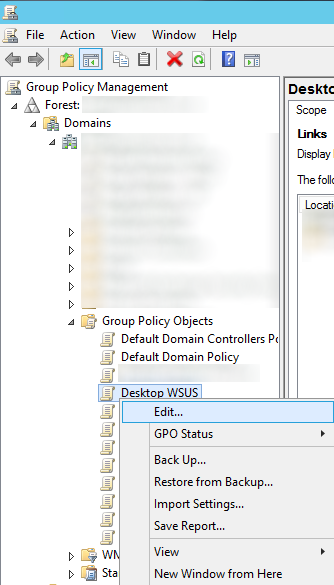
- Right click on the policy you want to edit and select Edit
- Expand Computer Configuration -> Polices -> Administrative Templates -> Windows Components -> Windows Update
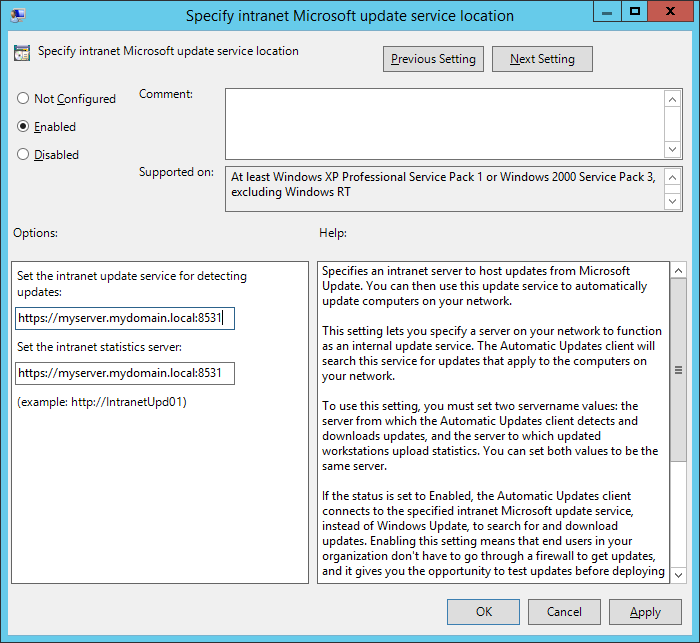
- Double click on Specify intranet Microsoft update service location
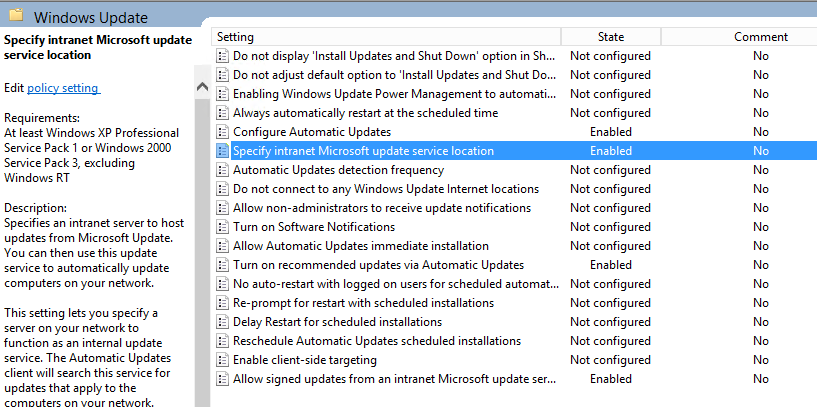
- Change the intranet update service url to https and specify port 8531 and then click Apply.
That should do it! Try doing a gpupdate /force on your local machine and the check for windows updates. If windows successfully completes checking for updates, you should be good to go! 🙂
Notes: Official documentation from Microsoft in regards to using SSL and WSUS can be found here: http://technet.microsoft.com/en-us/library/hh852346.aspx#consswsus
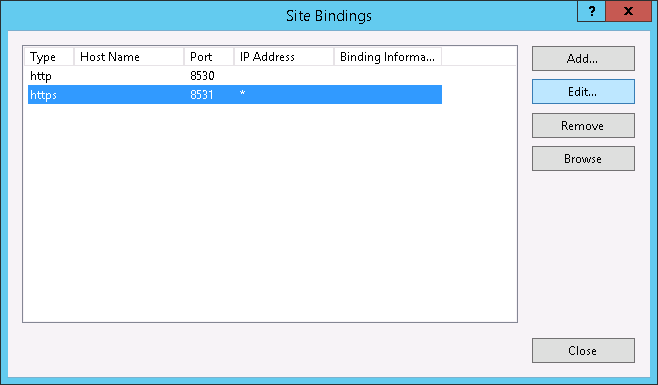
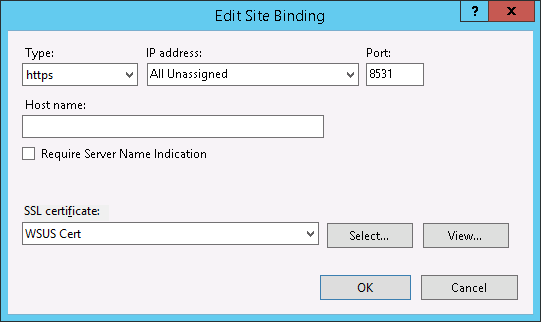

There is an error in your doco. You have in Step5 assigning the cert to the default website, instead of the WSUS Administration website
Hey Mark,
Thank you for pointing this out! I have updated the document to reflect the correct settings.
Appreciate the feedback!
Jack
Hi Jack,
Thanks for providing these instructions - very helpful!
Does this also provide client authentication? In other words, does the WSUS server require WSUS clients to authenticate themselves to the WSUS server by providing a computer certificate?
Thanks in advance,
Anwar
This requires the client to use SSL to communicate with WSUS but does not require the client to authenticate itself with their computer certificate. I believe you can achieve this by checking Require in IIS instead of Ignore (as shown in step 6-3).
Hope this helps,
Jack
Exelent write-up.
Maybe add that wildcard certificates are a NO-GO.
And add the command for moving to port 443 / 80 instead of the 853x ports 🙂
Why cant you use a wildcard cert?
There is no documentation by Microsoft stating that WSUS v3.0 supports or doesn't support. In this case, based on forums and the blog, it appears there are issues with the WSUS service understanding wildcard certs properly.
I was able to get our setup to just use a wildcard certificate, and port 443 only.
In IIS, for the wsus website, I added an additional https binding, port 443, and set the hostname to wsus.domain.com, and bound the *.domain.com certificate to it. So the bindings it creates are untouched.
On my client machines (actually other azure VMs in various networks), we set the WUServer = "https://wsus.domain.com", WUStatusServer = "https://wsus.domain.com" and all connects fine.
Thanks for the comment Michael! Sorry for late approval on this comment (seem to have missed this one), but can you provide what version of Windows Server you were using?
Jack
Pingback: Migrer un serveur WSUS en SSL - TechSpaceTechSpace
Thank you for a version in French 🙂
How would you create a certificate to work with an external FQDN and internal FQDN using an internal root CA?
Use a SAN certificate. See here: https://blogs.technet.microsoft.com/sus/2011/05/09/how-to-create-an-internet-facing-wsus-server-that-uses-different-internal-and-external-names/
Jack
At Step 6, by mistake I have applied "Require SSL" and "Ignore" on all subdirectories and the main directory "WSUS Administration" which broke something and WSUS is not showing the page and showing error with "Reset Server Node" button. Can you please guide, what setting I should choose for all those directory and subdirectories?
Please see the following article for the correct permissions: https://technet.microsoft.com/en-us/library/bb633246.aspx#procedureSection1
Perform the following steps on the APIRemoting30, ClientWebService, DSSAuthWebService, ServerSyncWebService, and SimpleAuthWebService virtual directories that reside under the WSUS Web site.
-On the SSL Settings page, select the Require SSL checkbox. Ensure that Client certificates is set to Ignore.
I did same but I want to revert because this setting broke something.
Great doc - to the point - very helpful
Hi Jack,
Great post, just followed it. Very smooth process. I am also setting up a Downstream server to connect to the primary and so I am following another document and I saw this:
"The certificate of the certification authority (CA) must be imported into the local computer Trusted Root CA store, or the Windows Server Update Service Trusted Root CA store on downstream WSUS servers. If the certificate is only imported to the Local User Trusted Root CA store, the downstream WSUS server will not be authenticated on the upstream server.
For more information about how to use SSL certificates in IIS, see Require Secure Sockets Layer (IIS 7).
You must import the certificate to all computers that will communicate with the WSUS server. This includes all client computers, downstream servers, and computers that run the WSUS Administration Console. The certificate should be imported into the local computer Trusted Root CA store or into the Windows Server Update Service Trusted Root CA store."
Does this mean anything outside of your document? Do I have to perform additional actions on Local PCs? I've already updated the WSUS GPOs for each Computer Group as mentioned above.
I'm guessing the statement provided above was due to the use of self-signed certificates. If you are using signed certificates from a public Certificate Authority (CA) or have already trusted the root certificate that issued the SSL certificate you are using, you should be fine for the downstream servers.
Jack
This has helped me loads, I've got my MCSA but one does this setup so infrequently 🙂
Excellent step-by-step
After some searching I figured out the issue. I accidentally added a character to the SSL cert. After creating a new cert this worked.
Thank You!
I am configuring SSL for our Upstream and downstream server(replica, but downloads updates from Microsoft). Should I go with domain certificate or self-signed certificate. Please advise!
If you have a PKI environment and can use domain issued certs, definitely use that over the self-signed cert.
We do not have PKI environment at the moment. But, is it safe to use self-signed cert?
I wouldn't use a self-signed cert. Any machines that need to connect to this will have errors unless you roll that certificate's public key to all machines.
So, whats the best certificate that you suggest for wsus in prod enironment?
Pingback: Computers doesn’t show in WSUS - Boot Panic
Appreciate the comment!