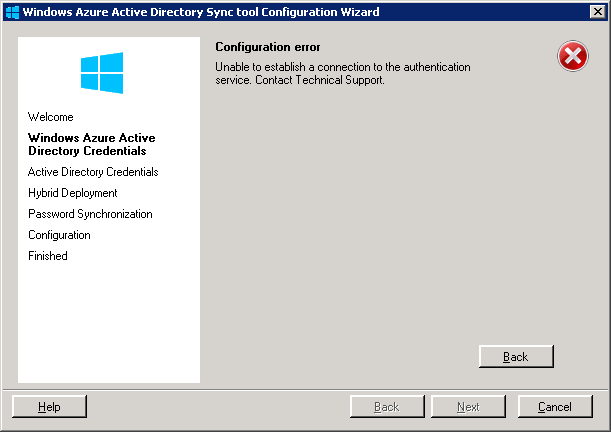
Symptom: You receive the following errors when running the Windows Azure Active Directory Sync tool Configuration Wizard or the Microsoft Online Services Directory Synchronization Configuration Wizard.
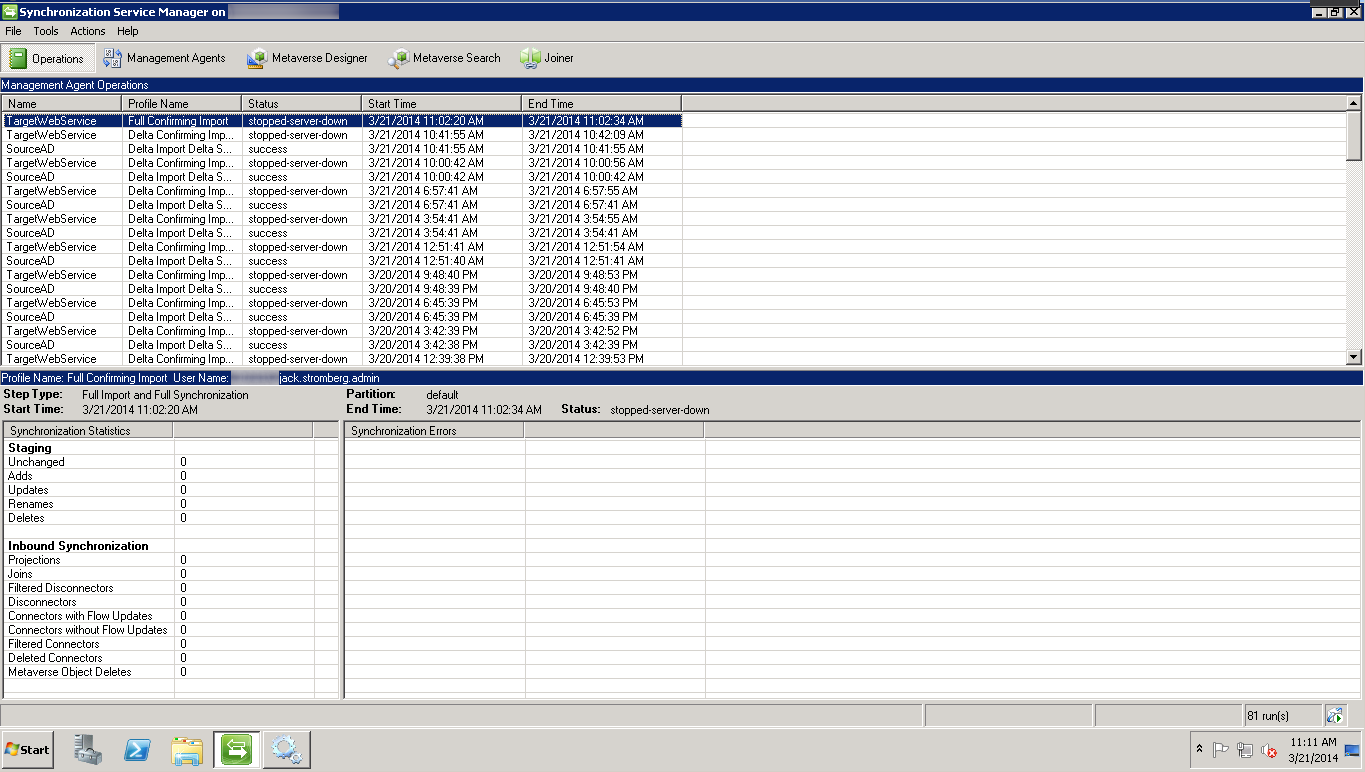
Synchronization Service Manager shows stopped-server-down status.
You receive the following events inside of event viewer:
Log Name: Application
Source: Directory Synchronization
Date: %Date%
Event ID: 0
Task Category: None
Level: Error
Keywords: Classic
User: N/A
Computer: %ComputerName%
Description:
Unable to establish a connection to the authentication service. Contact Technical Support. GetAuthState() failed with -2147186688 state. HResult:0. Contact Technical Support. (0x80048862)
Log Name: Application
Source: Directory Synchronization
Date: %Date%
Event ID: 102
Task Category: None
Level: Error
Keywords: Classic
User: N/A
Computer: %ComputerName%
Description:
Unable to establish a connection to the authentication service. Contact Technical Support.Log Name: Application
Source: FIMSynchronizationService
Date: %Date%
Event ID: 6803
Task Category: Management Agent Run Profile
Level: Error
Keywords: Classic
User: N/A
Computer: %ComputerName%
Description:
The management agent "TargetWebService" failed on run profile "Delta Confirming Import" because the server encountered errors.The Windows Azure Active Directory Sync tool Configuration Wizard presents you the following error message:
Unable to establish a connection to the authentication service. Contact Technical Support.
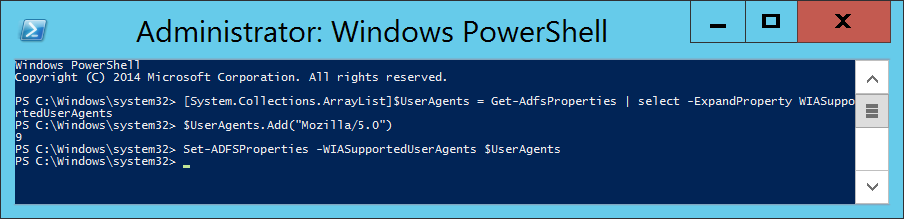
Solution: This turns out to be an issue with the provided credentials entered in the Windows Azure Active Directory Credentials step. Please make sure you verify the following.
- Do not use a federated Global Administrator service account. Federated service accounts are not allowed to be used with the synchronization tool. You should have a non-federated Global Administrator account with an @mydomain.onmicrosoft.com UPN.
- Ensure your Office 365 Global Administrator service account's password has not expired.