Problem:
Gathering trace/event logs in ADFS is not a trivial task. The following article will show you how to gather these logs to further help investigate relying party trust issues or issues with end users authenticating to the service. This tutorial will be leveraging ADFS v3.0 on Server 2012 R2. The same steps should apply for v2.0 on Server 2008 R2. This process does change slighting in ADFS on Server 2016 as the logging engine was rewritten. Depending on demand, a second article will be released for ADFS on Server 2016.
Caviets:
Before beginning, as a side note, debugging in ADFS v2-3 is honestly a total PITA (pain in the... butt). The problem with ADFS logging is logs are stored on the machines serving the requests, not centrally. In this case, you will likely have to enable tracing on each ADFS server, or configure your load balancer/host file to temporarly route requests to a specific machine so you know which server to hunt down for the logs. Likewise, as you will find at the end of the tutorial, the logs gathered from ADFS are very verbose. Take some time to familiarize yourself with the logs of a working request vs a failure to get used to what logs are actually meaningful.
Tutorial:
Enable list of events/audits to be logged
- Login to one of your ADFS servers that you believe will be authenticating the end users
- Open Server Manager
- In Server Manager, select Tools -> AD FS Management
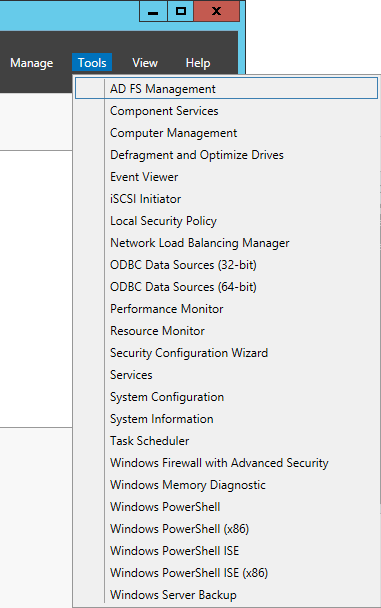
- In AD FS Management, select AD FS in the top left and select Edit Federation Service Properties...
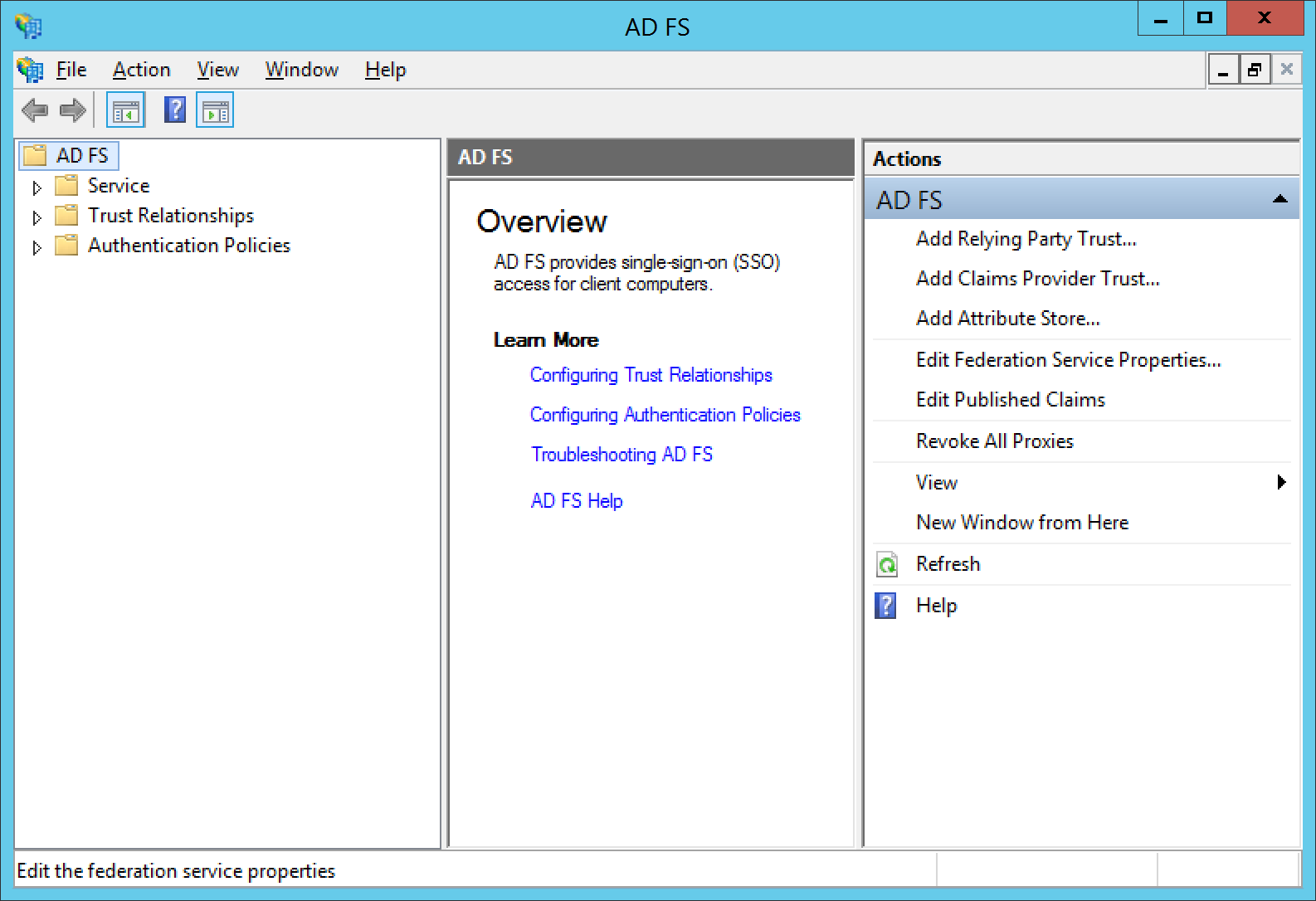
- Click on the Events tab and check all the items you wish to log and click OK

Enable tracing
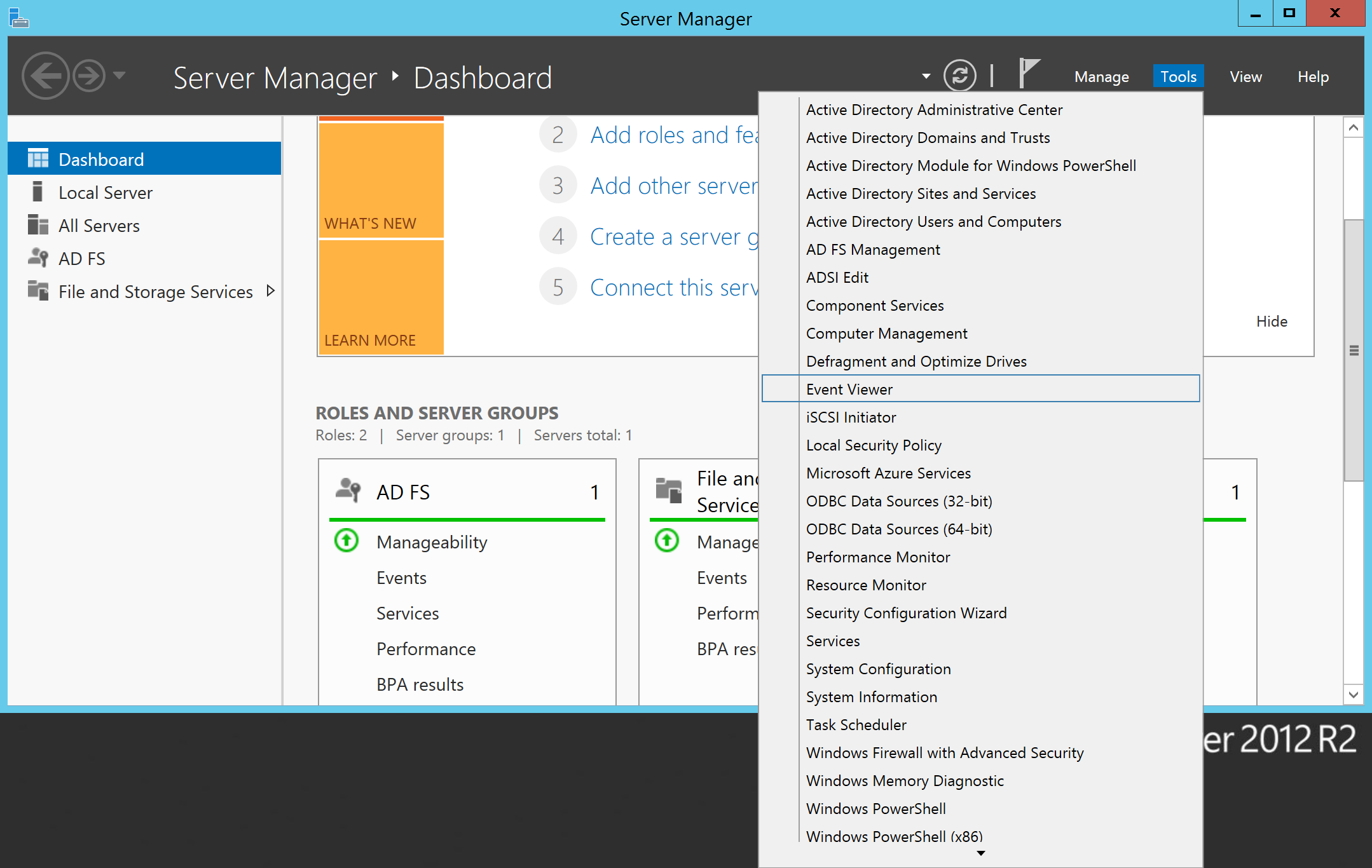
- Open Server Manager

- Select Tools -> Event Viewer
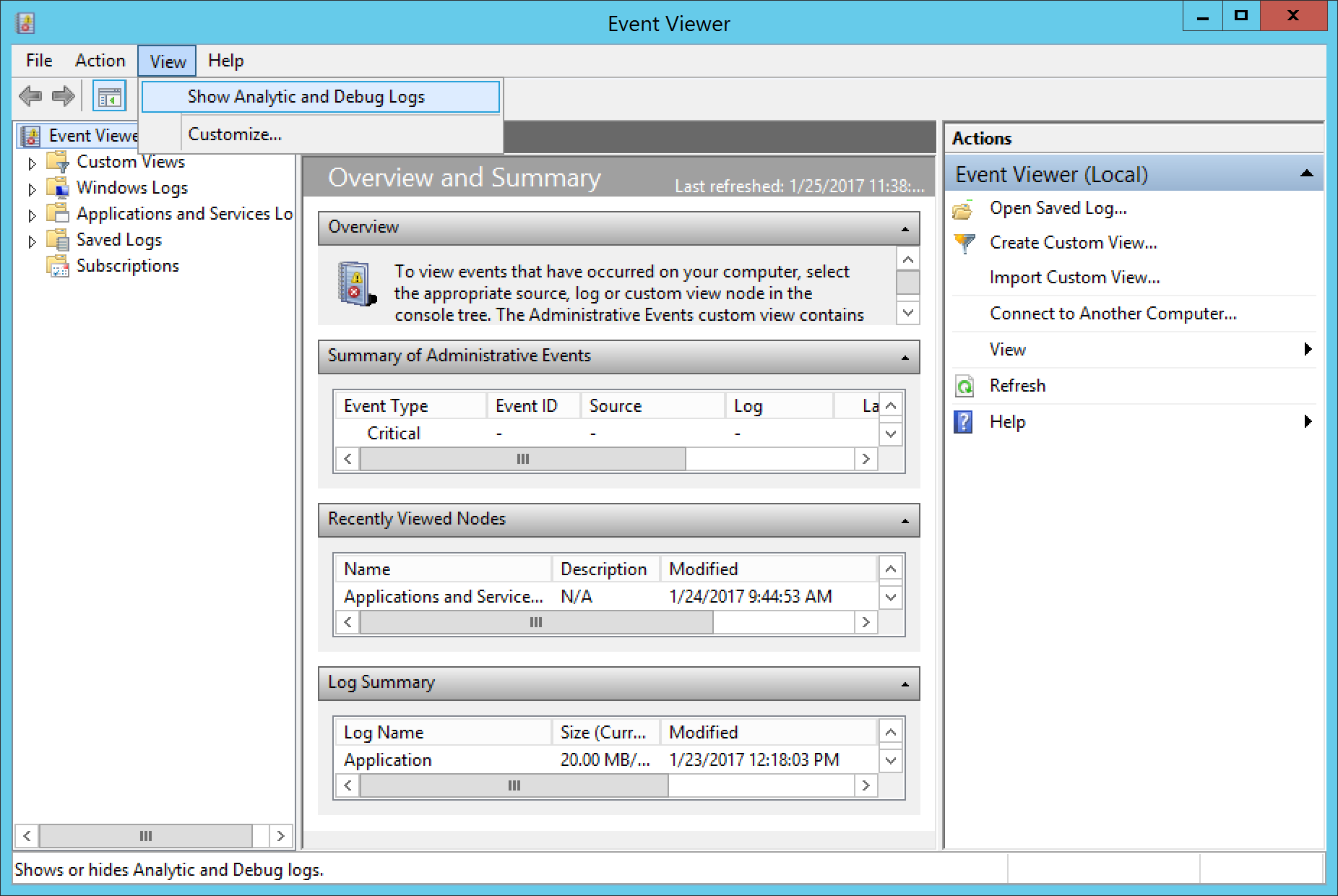
- In Event Viewer, select View in the top menu, and select Show Analytic and Debug Logs
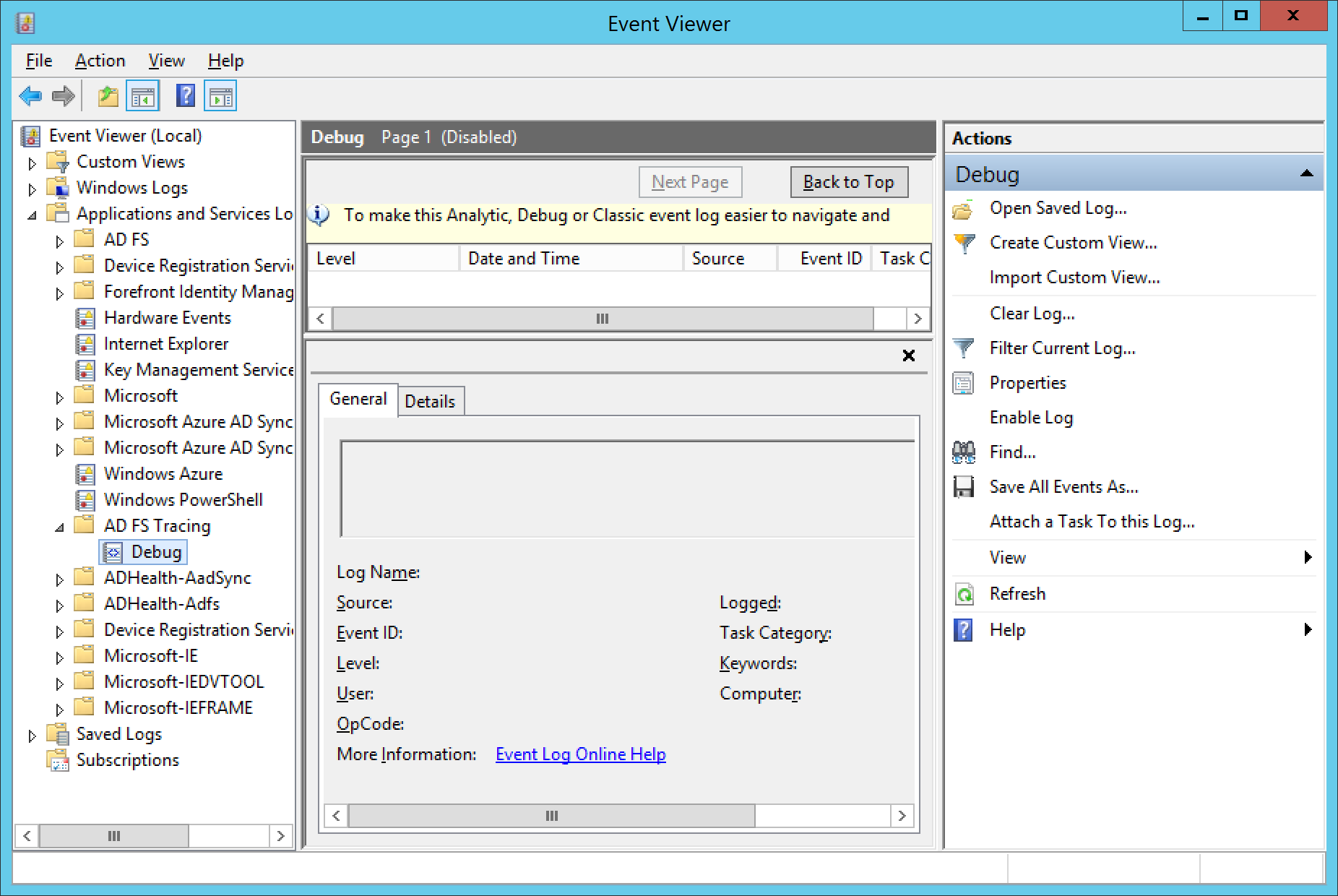
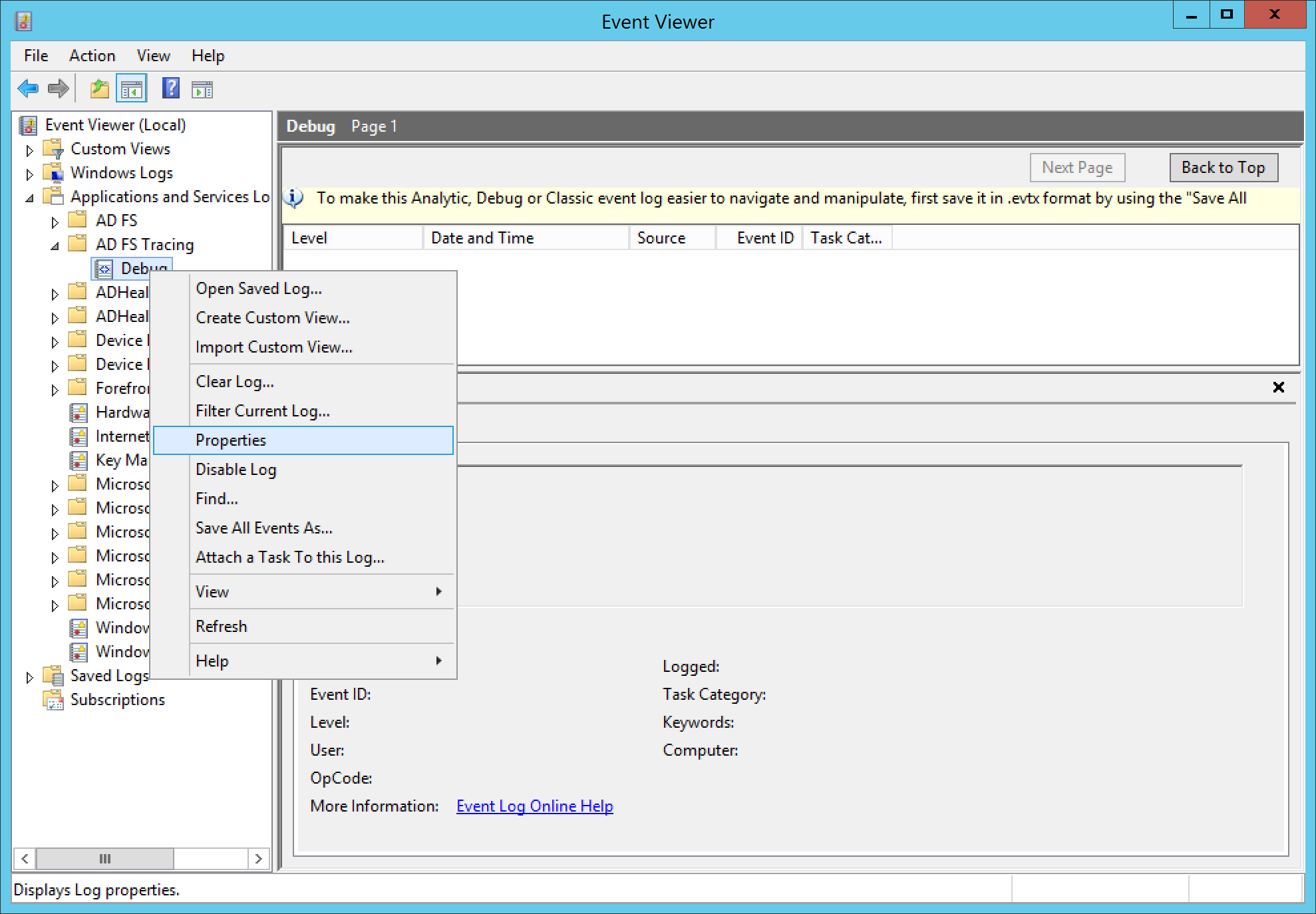
- Expand Applications and Services Logs, expand AD FS Tracing, and select Debug
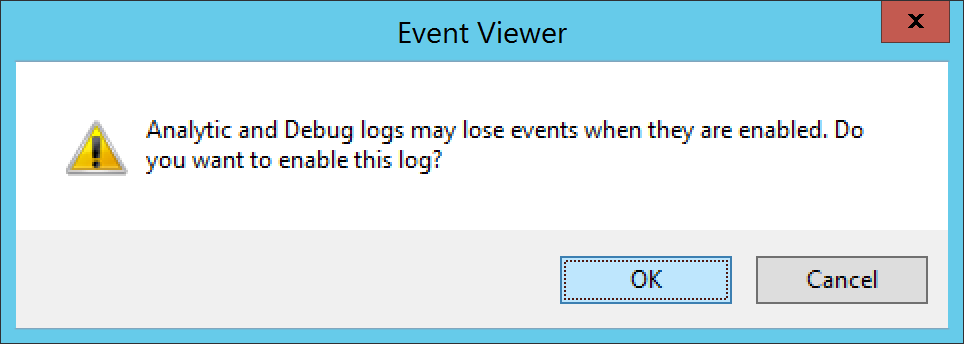
- When you are ready to begin collecting logs, right click on Debug and select Enable Log
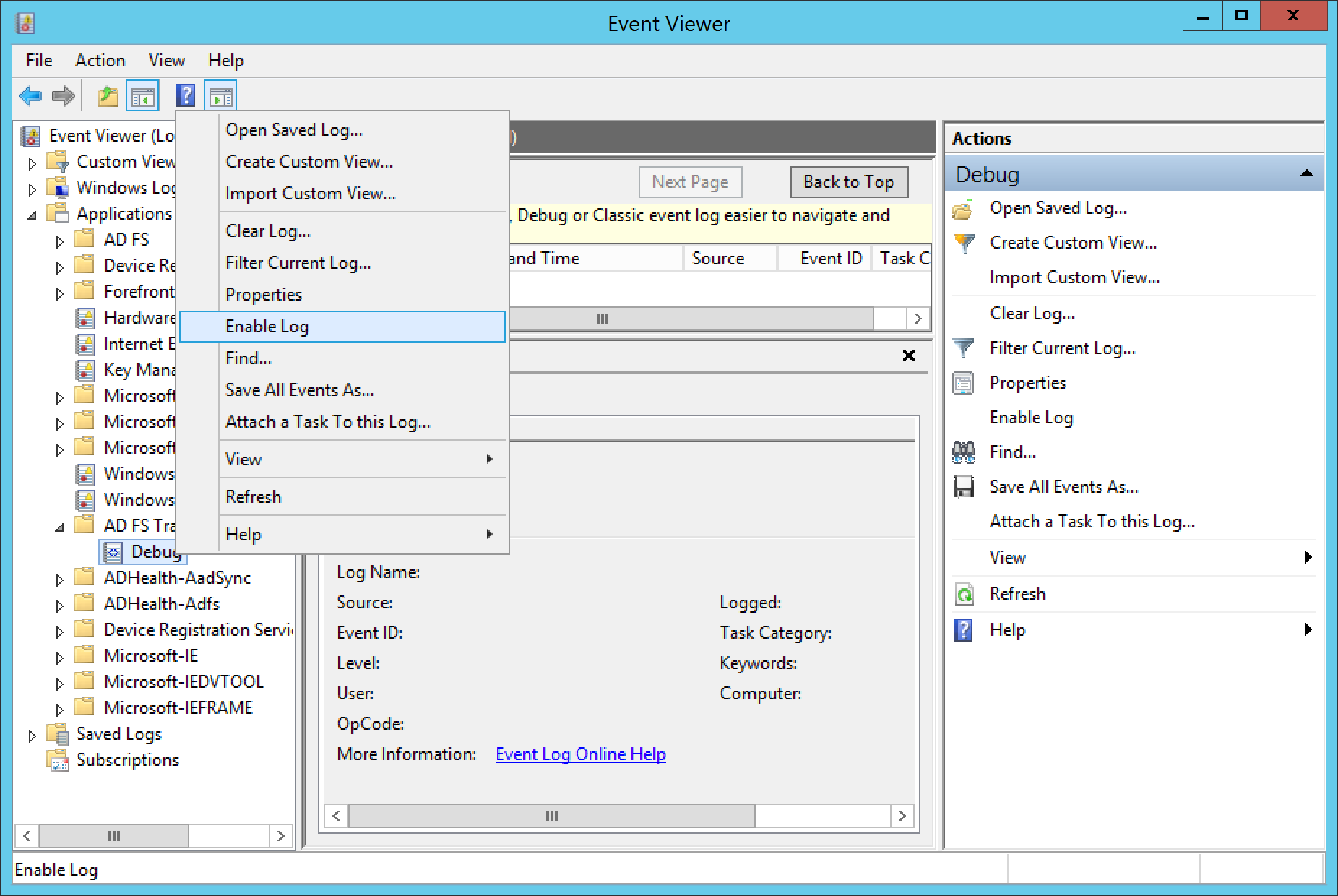
- Click OK when prompted to write over the existing event logs
- At this point, recreate the issue, error, or login to the relying party you want to debug.
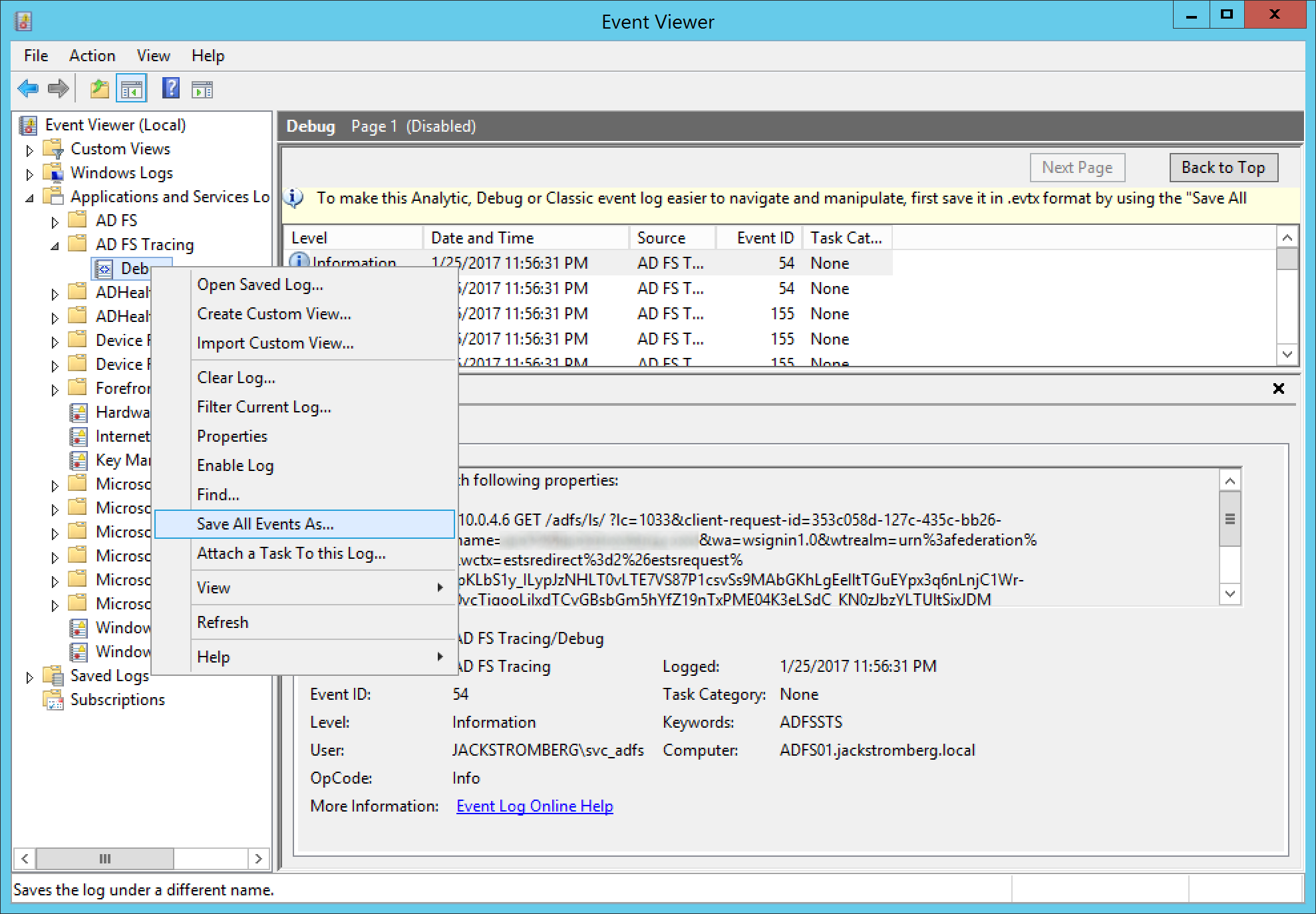
- Once you have recreated the error or logged in, go back to Event Viewer, right click on Debug and select Disable Log
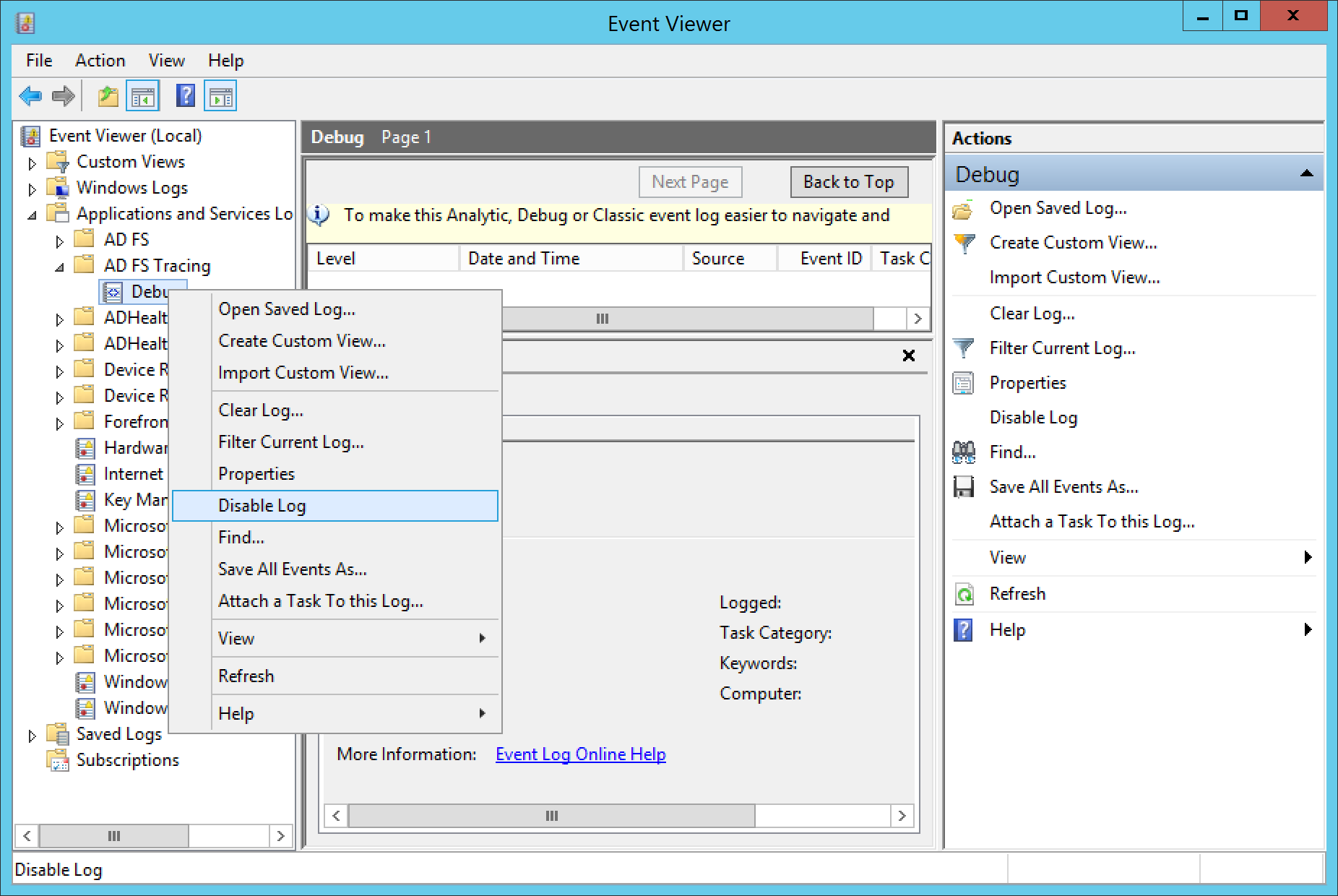
- At this point, you should have some events captured to further analyse 🙂
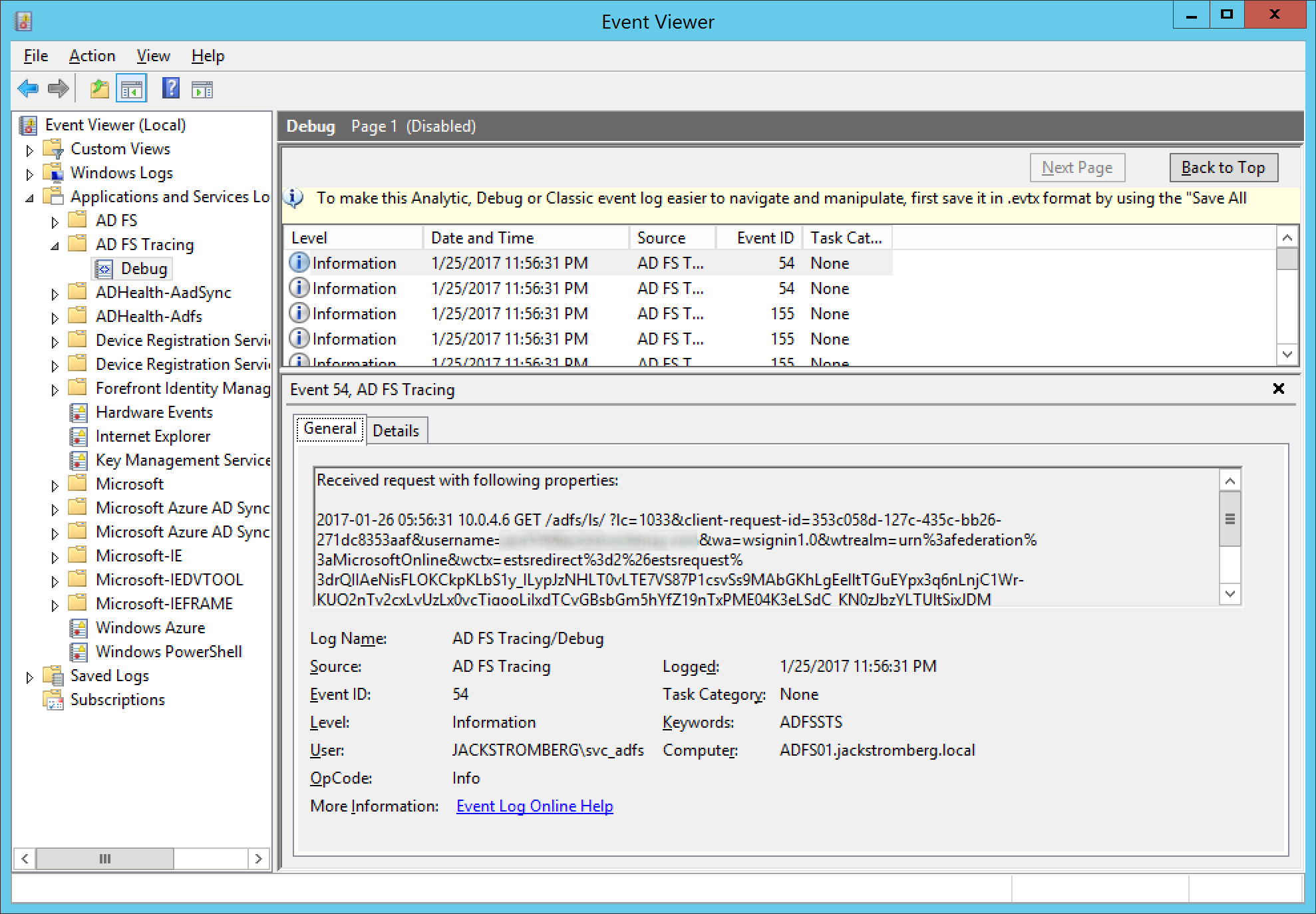
- Optional Step: Right click on Debug and select Save All Events As... This will export to a evtx file, in which this can be sent to another team for analysis or you can reference the logs at a later time.
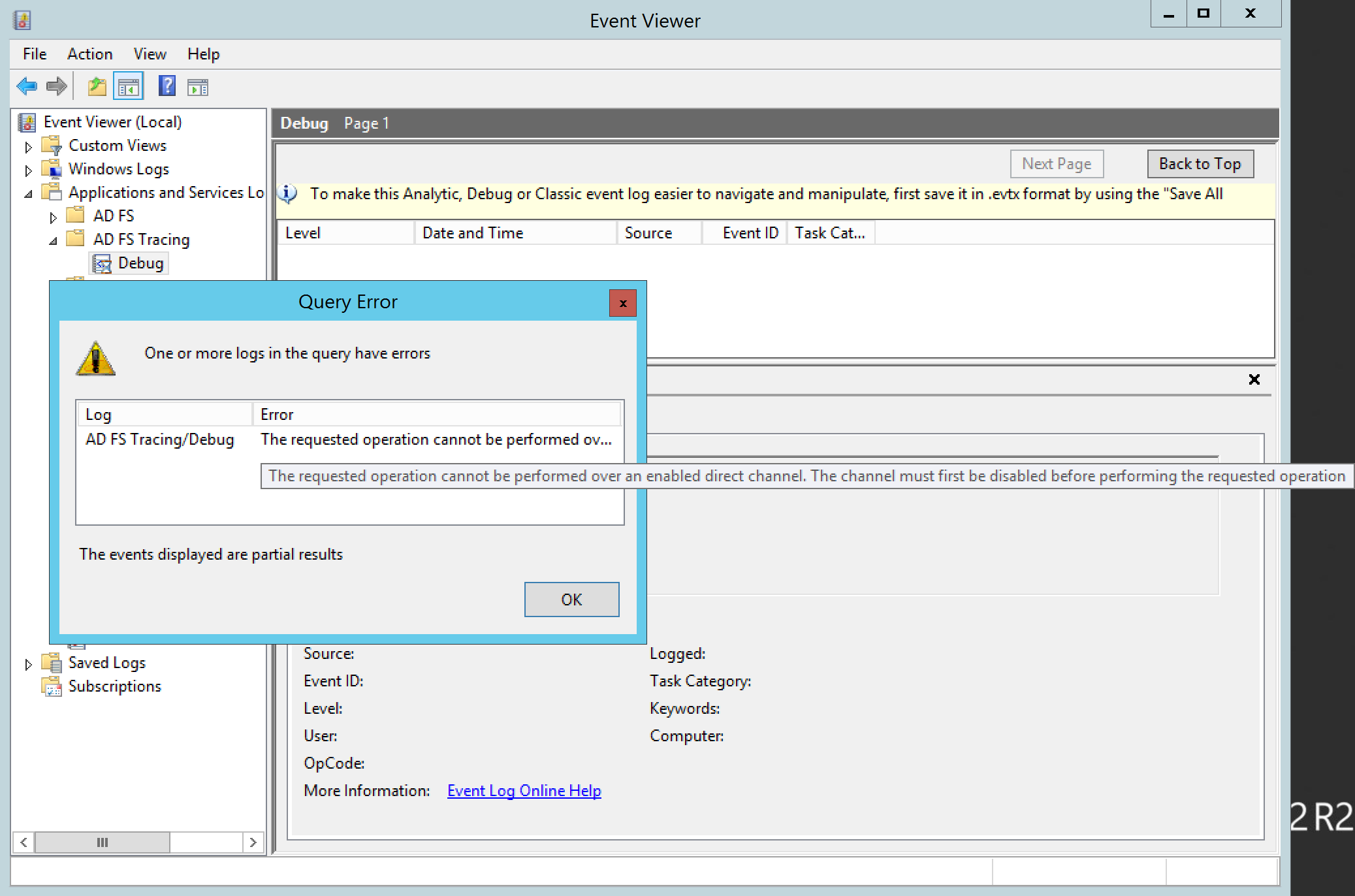
Common error when enabling Debug logging
One error I typically see is the following:
AD FS Debug - The requested operation cannot be performed over an enabled direct channel. The channel must first be disabled before performing the requested operation
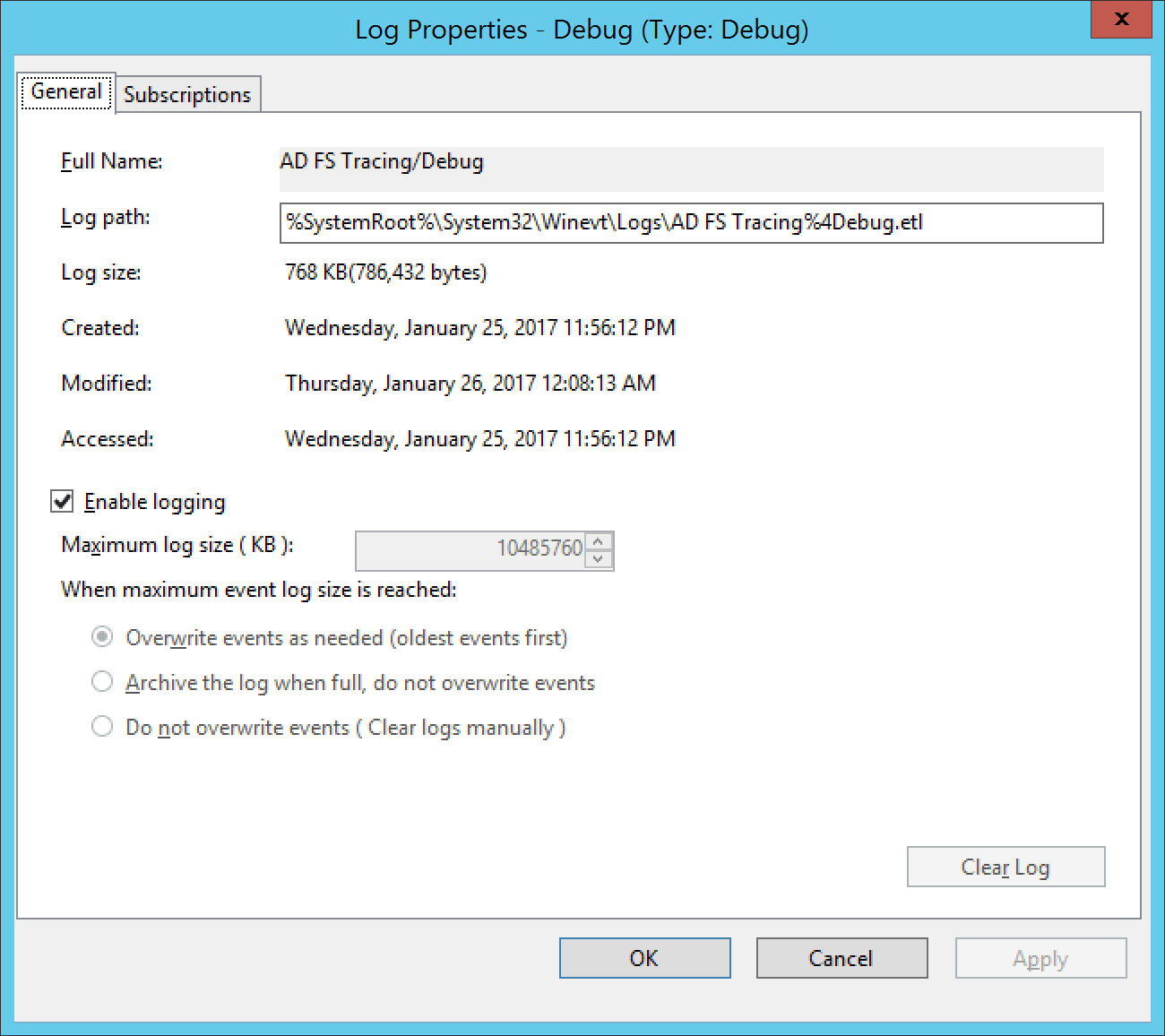
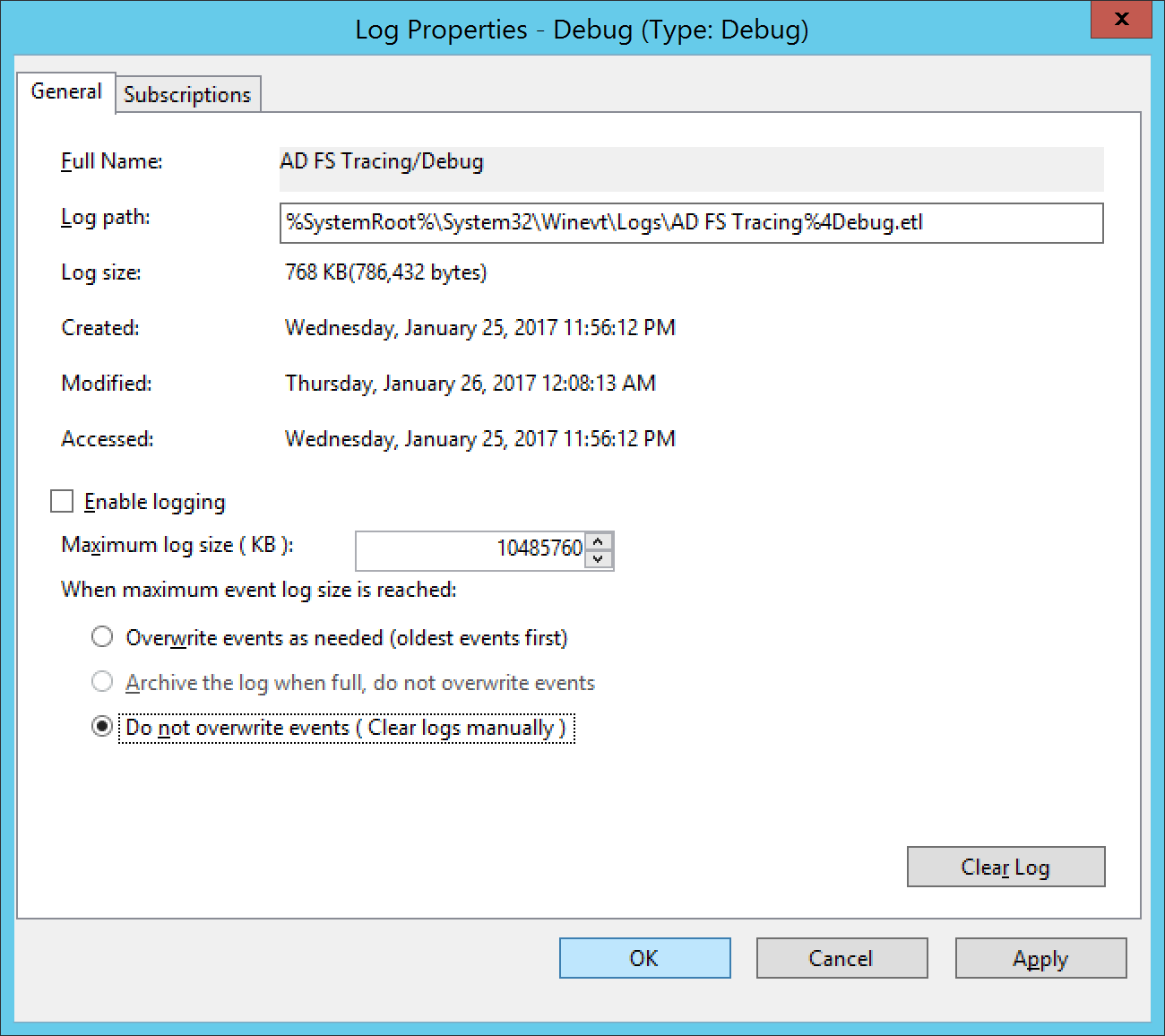
This error is caused by a misconfiguration on the logging properties of the Debug log. Please verify that you have not manually enabled the debug log nor have the maximum log file size set to Overwrite events as needed.
To fix, right click on Debug and select Properties
Typically, the screenshot below is an example of the incorrect settings used; make sure that Enable Logging is unchecked and is Do not overwrite events ( Clear logs manually ) is checked
Here is a picture of the correct settings for the AD FS Tracing Debug Logs; at which point, once the settings are applied, you should no longer receive this error when conducting your debug/trace logging.